Figure 1. Detection of ARP Cache Poisoning Attack
In this paper, the author presented how Man-in-the-Middle problem can be executed by an attacker. He also proposed a simple and lightweight protocol that will make it undesirable for black hats to carry out this act. The proposed detection protocol has been simulated in a wireless environment to test the effectiveness of the detection mechanism. In all cases the simulated Man-In-The-Middle attack was detected. The performance of the proposed detection mechanism was evaluated against an existing detection mechanism.
Man-In-The-Middle attack (often abbreviated MITM), is a form of active eavesdropping in which the attacker makes independent connections with the victims and relays messages between them, making them believe that they are talking directly to each other over a private connection when in fact the entire conversation is controlled by the attacker. A man-in-the-middle attack can only be successful when the attacker can impersonate each endpoint to the satisfaction of the other.
In the real world game of keep-away, two people toss a ball back and forth while a third person –the man in the middle – tries to intercept the ball while its enroute. In the cyber world, the game of keep-away gets a new twist; the two players have no idea the Man In The Middle (MITM) exists. It works like this
While computer C has the intercepted communication, it can modify the communication or even redirect it to an entirely new destination (i.e. Computer D). Meanwhile, computer A continues to believe that it is communicating By only with computer B.
Computer C has been able to interject itself between A and B through a process known as ARP poisoning [4].
With the business of e-commerce on its peak, more sensitive information is being passed around on computer networks. Financial and identity information are at a higher risk of being stolen or modified as users take advantage of the ease of doing business through computer networks. Sensitive user information is constantly transported between sessions after authentication and hackers are putting their best efforts to steal or modify them.
Computer networks face a variety of serious threats and risks. Most of the preventive methods against these attacks concentrate mainly on workstations that are not part of the computer networks and may be willing to be connected to the network illegally in order to wave malicious activities on the authorized nodes on the network. However, some authorized nodes on the network may as well be malicious as nodes that are not part of the network and because these malicious nodes are legitimate nodes on the network, less suspicions are placed on them. These threats are based on vulnerabilities associated with the ARP. ARP, or Address Resolution Protocol, uses a 'pick me' approach to resolving computers on a network. When computer A tries to communicate with B, ARP sends out a broadcast to the network devices asking 'who is B'? But there is no authentication built into ARP and thus ARP has no way of determining whether the response (pick me) is really B or not. By exploiting this lack of authentication, a malicious computer can tell ARP it is computer B, after which ARP will begin directing future requests for computer B to the malicious computer [4].
The final consequence is the disclosure of data which can be an act of economic terrorism, alteration of data such as grade fixing and denial-of-service attacks including Synchronization (SYN) floods and smurfing.
To write a computer program that will be used to simulate the proposed technique.
There is no such thing as perfect security; we need to consider how a system will react to a successful attack. Indeed the most critical part of a security system is not how well it works but how well it fails.
The main objective of the research is to write a computer program that can be used to detect MITM. We will achieve this by using the state of the art of executing MITM to come out with an effective desirable protocol. At least three laptops with wireless enabled will be used to create MITM scenario. Computer A and B will be the nodes to initiate the traffic and Computer C will be the 'man in the middle'. Colasoft Packet Builder 1.0 will be used to create and send packets from computer A. Computer B will be the node to receive the traffic. A will send the traffic with an IP, IP_A for some time. Computer C will intend to send packets with an IP, IP_A (instead of IP_C) while computer A is taken out of the network. A network protocol analyzer, Wireshark will be used to capture data packets arriving on Computer B and analysis made on the captured packets. We will further write a computer program using ActivePerl 5.101 that will be used to simulate the protocol.
Security, in terms of the integrity of the network's own infrastructure, the safety of its customers, and the nation itself, is becoming increasingly important in network operations today and cannot be considered optional [2].
An adequate security system management policy has long been an important issue [1]. A comprehensive network security plan must also consider losses of privacy when we define authentication and authorization as well as losses of performance when we define key management and security protocols. Therefore, a security plan must encompass all of the elements that make up the wireless and/or wired network, and provide important services such as
Fortunately, there are several ways to protect your computer from the hackers on internet.
Software companies are always updating their products, trying to eliminate any security breach that could be exploited by hackers. For this reason, their software makes a periodic check on the latest version available in the internet. It doesn't matter if they are operating systems, office suites, drivers, games or any other kind of specialized software, you always need to assure yourself that every software package is up-to-date.
Firewalls became main stream with the Internet. Now-adays it's impossible to be connected to the net without being checked by hackers, looking for possible breaches in your connection. Although they can be hardware or software, the most common one among users are the software firewalls, which are installed in your operating system and continually check the transmission of information from your PC to the external world and vice versa.
From all the security packages that a user needs to have installed in his PC, antivirus software is the first. It has been with us for a long time, even before the internet and the now common news on internet hacking. In the old days, virus spread through corporate networks to employee home computers who innocently took work home via diskettes. Finally, it spread to their friends' computers. Today, the Internet has provided viruses a better way to spread themselves through the world. A real time antivirus software package is a must for any user who wishes to navigate safely through the net and not find himself being a victim of a hacker attack.
All digital mobile systems provide security through some kind of encryption. Data can be encrypted in many ways, but algorithms used for secure data transfer fall into two categories: symmetric and asymmetric. Both rely on performing mathematical operations using a secret number known as a key. The difficulty with symmetric algorithms is that both parties need to have a copy of the key. On the other hand, asymmetric techniques use two separate keys for encryption and decryption. Usually, the encryption key can be publicly distributed, whereas the decryption key is held securely by the recipient
The most widely used symmetric algorithm is DES (Data Encryption Standard), developed by IBM in 1977. It uses a 56-bit key, which seemed unbreakable at that time. In 1997, a group of Internet users managed to read a DE Scoded message. Most organization now use triple-DES, which uses 112 bits. The basic idea is that larger keys mean more possible permutations, and so better encryption.
Several different asymmetric algorithms have been developed, each using a different type of “one-way” mathematical function. Rivest et al. [6] proposed an efficient algorithm, which they refer to as RSA, that relies on the fact that factorization is more difficult than multiplication. Indeed, multiplying two prime numbers together is easy for a computer, but recovering those two numbers from the product is not. The main drawback of asymmetric schemes is that they use a lot of CPU, and so cannot be used to encrypt an entire message through a mobile phone. Instead, it encrypts the message itself using a symmetric algorithm, with a key randomly generated by the network and sent to the handset using an asymmetric algorithm.
MITM attack is used by malicious internal users to sniff the network traffic between target hosts, in switched networks [8]. Malicious users can tap in on the network traffic for information without the knowledge of the networks’ legitimate owner. This information can include passwords, e-mail messages, encryption keys, sequence numbers or other proprietary data. Often, some of this information can be used to penetrate further into the network, or cause other severe damage. MITM can also be known as
When a Man in the Middle (MiM) is performed, a malicious user inserts his computer between the communications path of two target computers. The attack consists of rerouting the network traffic between two target hosts to a malicious host. Then the malicious host will direct the received packets to the original host, so that the communication between the two target hosts will not be interrupted and the two hosts will not notice that their communication is being sniffed [8]. With all the data between the hosts flowing through the hijacker's sniffer, he is free to modify the content of the packets. The trick to this technique is to get the packets to be routed through the hijacker's host. Lam, LeBlanc, and Smith [3] list two “tricks” that hijackers use to redirect traffic to create this “man in the middle” situation.
The first technique is to use forged ICMP (Internet Control Message Protocol) packets to redirect traffic between client and server through the hijacker's host. ICMP is an extension of IP that is used primarily to send error messages indicating problems in procession packets through a connection. In this case, the hijacker is forging messages to fool the client and server into thinking that the route through his host is better than the original path (better as in faster, shorter, or non-error prone).
The second technique is ARP (Address Resolution Protocol) spoofing. ARP tables are used by each host to map local IP addresses to hardware addresses or MAC addresses. ARP spoofing involves sending out forged ARP replies to fool the host broadcasting the ARP request into updating his ARP table, mapping the IP to be impersonated to the hijacker's hardware address. All traffic intended for that IP will be delivered to his host instead. He can then choose to alter and forward the packets to the real host.
To map a particular IP address to a given hardware address (MAC address) so that packets can be transmitted across local networks, systems use Address Resolution Protocol [5].
Each host in a network segment has a table, called ARP cache, which maps IP addresses to their corresponding MAC addresses. There are two entries in an ARP cache; static entries which remain in the ARP cache until the system reboots, mostly used in small LANs and dynamic entries which remain in the ARP cache for few minutes (depending on Operating System (OS)) then they are removed if not referenced. This mechanism is used by large networks.
This is a method of exploiting the interaction of IP and Ethernet protocols [7]. This is a malicious act by a host in a LAN. The host introduces a “spurious” IP address to MAC address mapping in another host's ARP cache. ARP operates by sending out “ARP request” packets. An ARP request asks the question “Is your IP address x.x.x.x? If so, send your MAC back to me.” These packets are broadcast to all computers on the LAN, even on a switch network. Each computer examines the ARP request, checks if it is currently assigned the specified IP, and sends an ARP reply containing its MAC address. To minimize the number of ARP requests being broadcast, OS keep a cache of ARP replies. When a computer receives an ARP reply, it will update its ARP cache with the new IP/MAC association. As ARP is a stateless protocol, most OS will update their cache if a reply is received, regardless of whether they have sent out an actual request.
ARP spoofing involves constructing forged ARP replies. By sending forged ARP replies, a target computer could be convinced to send frames destined for computer A to instead go to computer B. The process of updating a target computer's ARP cache with a forged entry is referred to as “poisoning”. This can be done by manipulating directly the ARP cache of a target host, independently of the ARP messages sent by the target host. This can be done by either adding a new fake entry in the ARP cache of the target host or by updating an existing entry with a fake IP address to MAC address mapping.
An efficient technique to protect an ARP cache against ARP cache poisoning attack is to use static entries in the ARP cache [8]. The entries in ARP cache cannot be updated by ARP request and reply packets and do not expire. However, in some OS such as windows 2000 and SunOS Solaris 5.9, this is deceitful. Those OS mark static entries in their ARP cache's but authorize their updates by ARP request and reply packets.
To corrupt the entries in the ARP cache of a target host, a malicious host generates an ARP request or reply messages including fake IP and MAC addresses. The success of this depends on the OS of the target host. A malicious host may attempt to send fake ARP reply message to a target host even though the malicious host did not receive ARP request message from the target host. If the OS of the target host accepts the fake ARP reply from the malicious host without checking whether it has send an ARP request message to the malicious host, the fake ARP reply corrupts the ARP cache of the target host with a fake IP/MAC entry. The malicious host can also send an ARP request message instead of an ARP reply message.
An experiment conducted to ascertain which commonly used OS with dynamic entries in the ARP caches are vulnerable to ARP cache poisoning attack indicate that all tested OS accept windows 2000 and Free BSD 4.11, and do not allow the creation of new entry by ARP reply messages and all tested OS allows the creation of new entry by ARP request message. Tested OS are windows XP, windows 2000, windows 2003 server, Linux 2.4, Linux 2.6, Free BSD 4.11 and SunOS Solaris 5.9. However, if the entry already exists in the ARP cache, all tested OS allow its update by ARP reply message (even in the absence of ARP request message) or request message [8]. Therefore using ARP reply message for ARP cache poisoning is difficult to realize against most OS. However it remains possible when using ARP request messages. Malicious users can first use ARP request messages to create fake IP/MAC entries in the ARP caches of their target host. Then, fake ARP fake reply messages are used to maintain existence of the fake entries in the ARP caches of the target host.
This technique consists of corrupting the ARP cache of the suspicious hosts and forcing them to forward packet received from their victim to the test host. By analyzing the traffic generated by a suspicious host, it is possible to ascertain whether it has performed ARP cache poisoning attack against other hosts in the network.
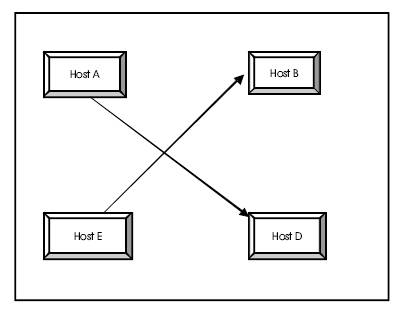
Let A, B, C, D, and E be hosts in a network. Hosts A and B are transmitting data. Host D has enabled its IP packet routing and it has corrupted the ARP cache of A and B in order to sniff the traffic generated by A and B. The ARP cache of C is not corrupted. Host E is the test host. The detection technique above allows us to identify D as a suspicious host since it has enabled its IP packet routing. The ARP cache of hosts A, B, C, and D before ARP cache poisoning is as follows
ARP cache of host A is IP_B-MAC_B, IP_C-MAC_C, IP_DMAC_ D, ARP cache of host B is IP_A-MAC_A, IP_C-MAC_C, IP_D-MAC_D, ARP cache of host C is IP_A-MAC_A, IP_BMAC_ B, IP_D-MAC_D and ARP cache of D is IP_A-MAC_A, IP_B-MAC_B, IP_C-MAC_C.
After ARP cache poisoning attack, the ARP caches of the various hosts are as follows
ARP cache of A (corrupted ARP cache) is IP_B-MAC_D, ARP cache of B (corrupted ARP cache) is IP_A-MAC_D, ARP cache of C is IP_A-MAC_A, IP_B-MAC_B and ARP cache of D is IP_A-MAC_A, IP_B-MAC_B.
For each suspected host, we corrupt its ARP cache using ARP cache poisoning attack. To do that, the test host E, send a fake ARP request to the suspicious host D, so that all the entries of the ARP cache of host D will have the MAC address of the test host E as MAC_E.
Consequently, all packets send by A to B will first go the suspected host, D since all the ARP caches of A and B have been corrupted by D. Suspicious host D will then redirect the traffic to the test host, E since the ARP cache of D has been corrupted by the test host E. The test host will send a copy of the received packet to its original destination B. Figure 1. indicates a detection of ARP cache poisoning attack.

Figure 1. Detection of ARP Cache Poisoning Attack
By analyzing the packet sent by the malicious host D, to the test host E, we can deduce that the source IP address in the IP header of the packet is of host A, but the source MAC address in the Ethernet header of the packet is of the malicious host D, when it should have been that of host A.
The rationale behind the design is to have a mechanism for checking the source MAC address and the source IP address against a list of authorized users on a WLAN. The goal of this rational is to flag out any unusual IP address/MAC address mapping and hence detecting the host with that particular MAC address as a malicious host. Figure 2 indicates the logic of the software design.
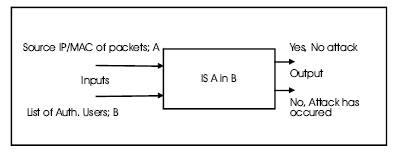
Figure 2. Logic of the Software Design
From the state of the art of executing man in the middle attack and detection method discussed above, we have realized that by analyzing the packet sent by the malicious host, D to the test host E, we can deduce that the source IP address in the IP header of the packet is of host A, but the source MAC address in the Ethernet header of the packet is of the malicious host D, when it should have been that of host A.
Wireshark was used to capture the packets. The captured packets were printed into a text file called which is then normalized and read into to retrieve the source MAC address and the source IP address.
From this, it was realized that the MAC address, 00:26:55:bb:25:09 was mapping to two different IP addresses, 192.168.7.17 and 169.254.2.2. The objective of this study was then to write a computer program to detect this anomaly. A database of all authorized users of the network which contains IP address and MAC address concatenated to form a string was generated.
A computer program was further wrote which will read into the text file and retrieve the source IP address and source MAC address. These strings (Source IP and source MAC) are concatenated to form a string.
This string is checked into the database and if it exist, success should be printed else an alert message should be printed. (Alert: Man in the Middle Attack Detected).
Figure 3 shows the output of the simulation
It is recommended that network security should be a concern of all. Session hijack attack does not depend on specific software or hardware vulnerabilities, but rather a design limitation within the TCP/IP protocol that does not guarantee security after the connection is made. It is therefore recommended that TCP/IP protocol should be extensively researched on in order to ensure that each data packet on a session is authenticated at the receiving node.
It is also recommended that an authentication be built into ARP to enable ARP to have a way of determining whether the response, “pick me” is really from a legitimate host.
It is also recommended that networks should be tested and monitored continuously in order to make them impenetrable by the intruders.
Man-In-The-Middle attack is a serious threat to networks as most of the systems are vulnerable to it. Although the above explanation and countermeasures will give insight to the defender to protect his /her network, it will also raise the security bar and will force the hijackers to apply more complex attacks to compromise the system. Networks should be tested and monitored continuously in order to make them impenetrable by the intruders.
In this research, the authors presented how Man-in-the- Middle problem can be executed by an attacker. They further presented how to detect this malicious act by using the state of the art of Man-in-the-middle attack. They proposed a simple and lightweight protocol that will make it undesirable for black hats to carry out this act.
They further wrote a computer program that can be used as a simulator to the Man-in-the-middle problem.
The performance of the proposed detection mechanism is evaluated against monitoring of Received Signal Strength (RSS). RSS is a measure of the energy observed by the physical layer at the antenna of a receiver. From intrusion detection perspective as suggested by Rupinder Gill, et al, by periodically monitoring the RSS values for a particular STA or an AP from a passive monitor we can develop a dynamic profile for the communicating nodes based on their RSS values. Any abrupt or unusual changes can be flagged as suspicious activity indicative of a potential session hijacking attack.
However the strength of RF signals undergoes some attenuation during transmission after leaving the sender's radio and this signal strength deterioration is governed by a variety of factors like RF interferences, rainfall, wind, intervening obstacles etc. These factors can cause the signal strength to change abruptly without necessary passing through an adversary as some of these factors are natural occurring phenomenon. This detection mechanism can not indicate who is actually stealing the session.
Also Rupinder Gill, et al also argue that the distance between sender and adversary must be the same as the distance between the sender and receiver before the adversary can deduce the signal strength the receiver will be expecting, so he can re-route the stolen data packets to the receiver without the receiver noticing that the data packets actually came the adversary. However the adversary can form an equilateral triangle with the sender and the receiver such that the distance between the sender and the adversary will be the same as the distance between sender and the receiver.
However the proposed detection mechanism is not affected by these factors as it was proven to be deterministic based on the simulations results above. Also, apart from being a detection mechanism, it was able to detect which of the nodes on the network actually carried out the malicious activity.