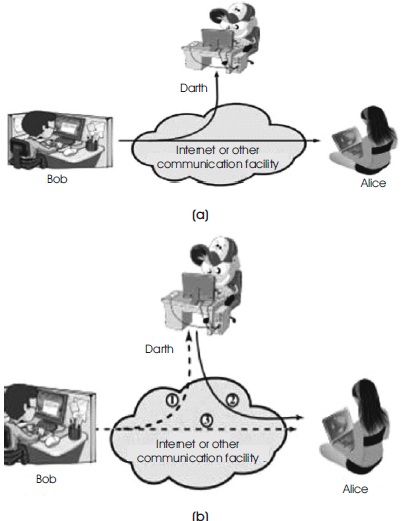
Figure 1. Security Attacks, (a) Passive Attacks, (b) ( Stallings, 2006)
Now-a-days, secured information transfer to others require security because the data might be stolen from hackers. To avoid these type of problems, are use Cryptography Secure Algorithms. Cryptography Algorithms play important role in network security. It is an Advanced Encryption Standard (AES) Algorithm. The AES is a Symmetric encryption using private key. This encryption process consists of blocks such as Key Expansion, Pre Round Operation, Add Round Key, Sub Bytes, Shift Rows and Mix Column. The Advanced encryption standard algorithm is using cryptographic secret keys-128 bits, 192 bits, and 256 bits to encryption, and decryption input data is 128 bits. This paper represents the survey of Cryptography Secure AES algorithm.
Communication system plays an important role to transfer large amount of data in various fields. Some data might be transmitted through insecure channel from sender to recipient. Different techniques and methods have been used by private and public sectors to protect secret data from intruders, because security of electronic data is critical. In security attacks, important information is stolen or the original information is changed.
There are two types of security attacks, passive and active attacks as shown in Figure 1. Passive attack means important data is stolen by hackers between sender and recipient. Active attack means data is stolen and original information is changed by hackers before sending to recipient.

Figure 1. Security Attacks, (a) Passive Attacks, (b) ( Stallings, 2006)
In Network Security, Cryptography techniques play an important role. The opponents are of two category i.e. Human (hackers), and software (virus, worms) to enter into the security information files. Cryptography techniques or algorithms act as a gate keeper in the security of data like password authentication.
Network security working principle starts from sender side. The secret key is added to the input data, and it becomes secure information. That secure information is sents to the channel. Later the recipient receives secure information by adding secret key. Then the original information is recovered as shown in Figure 2.
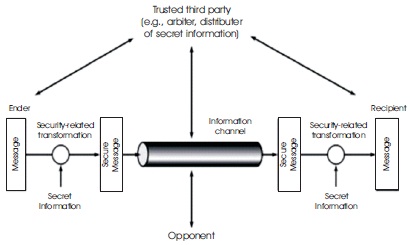
Figure 2. Model for Network Security (Stallings, 2006)
In 1997, the National Institute of Standards and Technology ( NIST, 1999) has standardized security of information using DES (Data Encryption Standard) Algorithm ( NIST 1999). DES data (64 bit) was needed as its key size (56bit) was too small. Increasing computing power was considered for complete key search attack. Triple DES was designed to overcome this type of drawback, but triple DES was found to be slow. Drawbacks are Key size is too small, Less security and Slow process ( Srinivas & Akramuddin, 2016).
In 2001, The National Institute of Standards and Technology (NIST) have standardized AES Encryption and Decryption Algorithm which turned into Federal Information Processing Standard (FIPS) ( NIST 2001). AES algorithm was developed by two professional cryptographers Daemen and Rijmen (1999). Applications are Mobile Phones, Smart Cards, Magnetism Cards, Intel Core Processors Family, Automated Teller Machines (ATM), World Wide Web servers, Solid State Devices, IPSec and Secure Sockets Layer Protocols, various other transmission protocols standardized by IEEE 802.11i WPA2 standard Wi-Fi networks for secure encryption and digital video systems, etc( Sai Srinivas, MD. Akramuddin, 2016).
Based on key types the encryption algorithm can be classified into two groups.
Symmetric encryption with private key algorithm is shown in Figure 3 (The sender and recipient must have the same key in order to encode or decode the protected information) ( Srinivas & Akramuddin, 2016) (FIPS PUB, 2001).
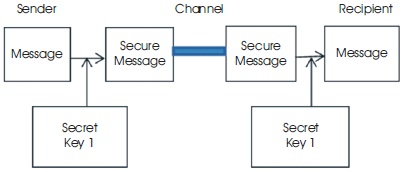
Figure 3. Symmetric Encryption
Asymmetric encryption with public key algorithm is shown in Figure 4 (The sender and recipient have different keys with respect to the communication roles played) ( Srinivas & Akramuddin, 2016).
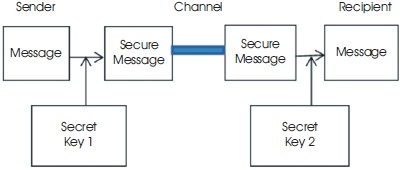
Figure 4. Asymmetric Encryption
Symmetric key algorithm is faster to execute electronically than asymmetric key algorithm.
Ueno et al. (2019) proposed that datapath utilizes new operation reordering and register-retiming techniques to unify critical components with fewer additional selectors. And datapath has the lowest critical path delay compared to conventional ones with tower-field S-boxes. So architecture can perform encryption/decryption with the lowest power/energy consumption.
Jindal et al. (2020) executed AES (Advanced Encryption Standard) simulation, on double 7th series capital to investigate the comparison of cost and performance. The implementation of traditional AES algorithm has been accomplished on Artix7 and Kintex 7 FPGA. Xilinx VIVADO tool has been used for simulation. Here it was found that Kintex-7 FPGA consumes less area in comparison to Artix-7 FPGA. Based on cost Artix-7 FPGA is preferred.
Chauhan and Sasamal (2019) proposed an algorithm which generates multiple s-boxes for different rounds, that is s-box changes with respect to key and hence increases the security of cipher. However, it will take extra hardware to key with s-box as compared to normal AES with simulated Xilinx ISE 14.7.
Davis et al. (2019) proposed that Low power encryption key to the safety and long-term performance of these power constrained implantable devices. So a new low power AES design based on a novel implementation for the ShiftRows operation, is designed and implemented using 45nm and 90nm technology nodes.
Gaded and Deshpande (2019) proposed design of S-box which works on Composite Field arithmetic reduction in the area in terms of FPGA slices and reduced gate delay and path delay. Coding of S- box is designed using Verilog HDL, simulated in Modelsim 6.4c and synthesized in Xilinx ISE 13.2.
Shashidhar et al. (2018) mainly focused on AES with operating frequency reaching 291.68MHz and throughput 37.21Gbps. Implemented Pipelined architecture for AES algorithm increased the Performance.
Srilaya and Velampalli (2018) evaluated performance of DES and AES algorithms based on few important parameters. Based on plain text of 32 bytes, it was concluded that encryption and decryption time in DES is least compared to AES. Throughput of encryption and throughput of decryption of DES is more compared to AES.
It was concluded that performance of AES is better than DES.
Yuan et al. (2018) proposed that AES implementation is piped into 4 stages, which leads to a performance improvement in term of area and throughput. A design of 1st order mask has been proposed, which can resist 1st order differential (or correlation) power attack. This design can be easily expanded to other SPN-based primitives.
Andriani et al. (2018) focused on comparison of AES 128,192 and 256 in terms of processing time. It was found that AES 128 bit has faster processing time compared to AES 192 bit and AES 256 bit. Although on the CPU usage for the process of encryption and decryption of files, AES 192 bit requires the lowest CPU usage compared with the other two AES algorithms.
Equihua et al. (2021) focused on GF Multiplier used for area consumption and processing speed, and involvement in Mix- Columns and Inverse Mix-Columns transformation is presented.
Good and Benaissa (2006) proposed Two low-area designs for the Advanced Encryption Standard on Fieldprogrammable Gate Arrays (FPGAs) devices-Xilinx Spartan II FPGA (XC2S15), Xilinx PicoBlaze soft core.
Rao and Sharma (2017) focused on implementation of memory-less AES architecture for encryption and decryption Algorithm. The major drawback of this research work is encryption and decryption could not be performed in parallel with XC7A100T (Atrix7) FPGA Board.
Shreenivas et al. (2017) implemented S-Box for AES encryption algorithm designed with low area power and timing, modelled and verified using the Verilog hardware description language. The Cadence SimVision tool was adopted for simulation of the hardware design. The hardware model is synthesized using Cadence Encounter RTL compiler Tool.
Abhijith et al. (2013) designed the operations as LUTs and ROMs, the best high speed encryption algorithm with G XILINX– VIRTEX5 Field Programmable Gate Array (FPGA).
Mohan and Rambabu (2014) implemented low complexity architecture easily achieved with low latency as well as high throughput with Xilinx, Altera using APEX20KC FPGA.
Wang et al. (2012) designed system computing speed, the pipelining and parallel processing methods by used Virtex- 5 FPGA Xilinx ISE 13.3.
Hasamnis and Limaye (2012) reduced Thermal Power Dessipation with Altera NIOS II processor. Li and Friggstad (2005) designed critical path, small gate count and versatility (between encode and decode) by Xilinx.
Huddar et al. (2013) introduced Vedic Mathematics techniques, 100% area efficiency and a 2 times increase in speed using Spartan 3E series XC3S100 E XILINX FPGA.
Chawla and Goel (2015) designed a new architecture for Byte Substitution and Add Round Key operations of different key expansion algorithm, less to Differential Power Analysis (DPA) and saturation attacks, using Virtex-7 FPGA for two parameters, Performance and Area using Vivado Design Suite.
Balupala et al. (2021) focused on Galois Field (GF) implementation of arithmetic operations. This algorithm used removal of side-channel attacks of cryptography. Sbox and inverse S-box were generated on a Xilinx Vertix-7 FPGA. This design can be verified on all FPGA's. Future work concerns deeper analysis of improving power, performance, and area [PPA] of these Galois field arithmetic operations in various cryptographic applications.
Kaur et al. (2021) focused on analyzing and selecting research on AES. Also analyzed Machine Learning techniques like Artificial Neural Network used to protect side channel attack for images. Recent developments like effective differential power analysis technique and hybrid encryption algorithm using LZW have been analyzed in detail. Finally it is concluded with a systematic analysis of different types of attacks on AES.
Equihua et al. (2021) focused on optimized Galois Field Multiplier for area consumption and processing speed. The GF design involves a routing circuit which allowed the proposed architecture to perform encryption or decryption by using common modules. The result mentions that proposed digital circuit expends fewer LUTs and fewer registers.
Peng and Zhu (2021) focused on pipeline architecture to optimize AES-128 algorithm, including the key expansion part and the encryption and decryption part. The bit width conversion module in encryption part can be connected with other types of bus to improve the data throughput and clock frequency. For implementation, Quartus tool is used to compile AES algorithm and entity PCB circuit to test in real time environment.
Yendamury and Mohankumar (2021) focused on AES cryptographic core using an effective logic locking technique. AES lock block is inserted in sub process of AES decryption algorithm. AES Lock block is highly efficient to secure the AES cryptographic decryption core.
Few AES Encryption Techniques have been discussed in Table 1 based on area, throughput, delay, clock cycles and frequencies used in different AES Techniques.
AES means Advanced Encryption Standard. The cipher is a component which is a combination of original text and secret key. It is responsible for performing encryption or decryption on blocks of input data of 128 bits, while the key expander may be 128, 192 and 256 bits, responsible for preparing the input key for use by the cipher all round. The Advance Encryption Standard (AES) is composed of four different process that are repeated in a number of rounds. These are SubByte, ShiftRow, MixColumn, and AddRound key. The AES algorithm uses cryptographic keys of 16 bytes, 24 bytes, and 32 bytes to encrypt and decrypt data in blocks or input 16 bytes. The number of rounds in AES is variable and depends on the length of the key, i.e 10 rounds for 16 bytes key, 12 rounds for 24 bytes key and 14 rounds for 32 bytes key. Each of the round uses a different 16 bytes round key, which is calculated from the original AES key. When a key of size 32 bytes is used, the number of rounds are repeated which is equal to 14 (Daemen & Rijmen, 1999).
AES encrypts 128bits (16 bytes) of data at a time. Figure 5 shows the encryption process of AES algorithm. The block AES encrypt in Figure 5 has 4 internal steps which includes SubBytes, ShiftRows, MixColumn and Key Expansion.
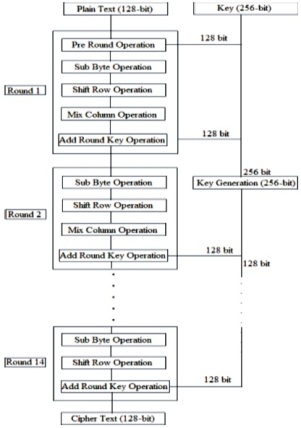
Figure 5. AES Encryption Process (Daemen & Rijmen, 1999)
It treats 16 bytes as a grid of 4*4 matrix. It is divided into 3 types namely AES-128, AES-192 and AES-256 which has 10, 12 and 14 rounds respectively as shown in Table 2. It is the widely used algorithm in providing high security to the message input (Daemen & Rijmen, 1999).
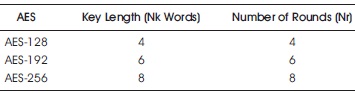
Table 2. Combination of Key Length and Total Number of Rounds
Input and Output: Sequences of 128 bits (digits values of 0's or 1's). This is also called blocks. The cipher key means combination of input data and secret key. The cipher keys are sequence of 16 Bytes, 24 Bytes and 32 Bytes.
Block length or input data = 128 bits or 16 Bytes
Key length = 128 bits or 16 Bytes
Key length = 192 bits or 24 Bytes
Bytes Key length = 256 bits or 32 Bytes.
0000-0, 0001-1, 0010-2, 0011-3, 0100-4, 0101-5, 0110-6, 0111-7, 1000-8, 1001-9, 1010-A, 1011-B, 1100-C, 1101-D, 1110-E, 1111-F
SubByte: The SubBytes transformation (shown in Figures 6 and 7) is a non-linear byte substitution that operates independently on each byte of the State using a substitution table S-box as shown in Figure 8 (FIPS PUB 197,2001).

Figure 6. Effect of SubBytes Transformation (FIPS PUB 197, 2001)
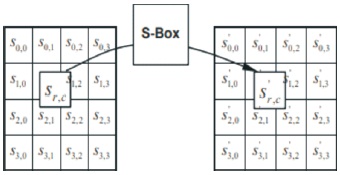
Figure 7. SubBytes Applies the S-box to each Byte (FIPS PUB197, 2001)
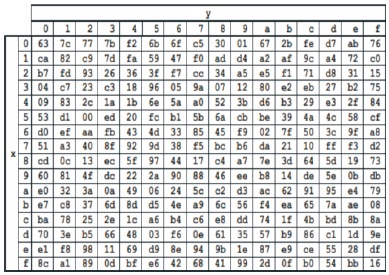
Figure 8. S-Box (FIPS PUB 197, 2001)
ShiftRows: In the ShiftRows transformation, the bytes in the last three rows of the State are cyclically shifted over different numbers of bytes as shown in Figure 9. The first row, r = 0, is not shifted (FIPS PUB 197, 2001). Here all shifts are left shift, second row one shift left, third row two shift left cyclically and fourth row shift 3 shifts cyclically but first row does not shift cyclically.
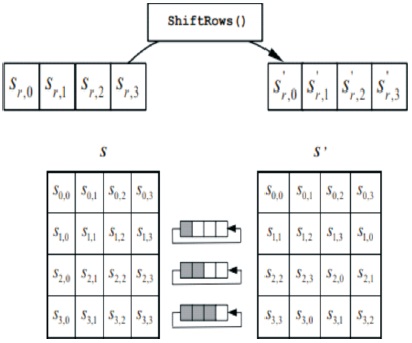
Figure 9. ShiftRows Cyclically Shifts Last Three Rows (FIPS PUB 197, 2001)
MixColumns: The MixColumns transformation operates on the State column by column, treating each column as a four terms polynomial (FIPS PUB 197, 2001). MixColumns round performs multiplication of two 4X4 matrix. Later the result of multiplication performs XOR operation. Final result is in 4X4 matrix, not changed as shown in Figure 10.
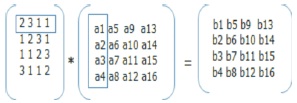
Figure 10. Multiplication Matrix
Example:
b1 = (a1 * 2) XOR (a2 *3) XOR (a3 * 1) XOR (a4 * 1)
And so on until end of rows and columns.
AddRround Key: In the AddRoundKey transformation, a Round Key is added to the State by bit wise XOR operation as shown in Figure 11 (FIPS PUB 197,2001).
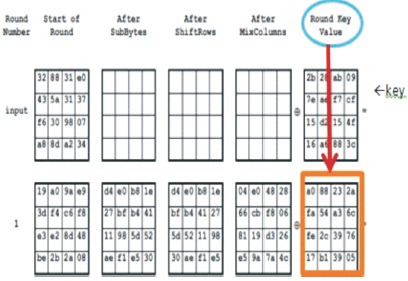
Figure 11. Add RoundKey Transformation (FIPS PUB 197,2001)
Figure 12 shows the decryption process of AES algorithm which is the reverse process of AES encryption. The no of rounds is determined by size of key and it is shown in Table 2. Key length can be 16, 24 and 32 bytes. AES algorithm is a type of symmetric cryptographic algorithm.
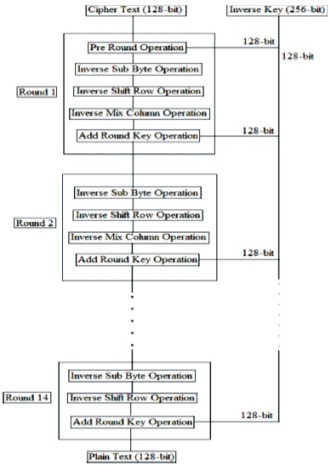
Figure 12. AES Decryption Process (Daemen & Rijmen, 1999)
InvSubBytes: InvSubBytes transformation is the inverse byte substitution transformation, in which the inverse S-box is applied to each byte of the State as shown in Figure 13.
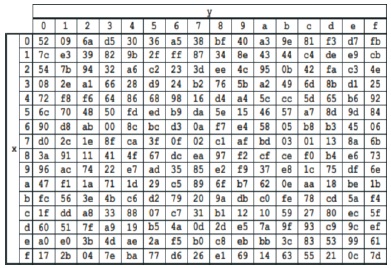
Figure 13. Inverse S-Box (FIPS PUB 197, 2001)
InvShiftRows: InvShiftRows is inverse of ShiftRows transformation. The bytes in the last three rows are cyclically left shifted over different numbers of bytes as shown in Figure 14. The first row is not shifted.
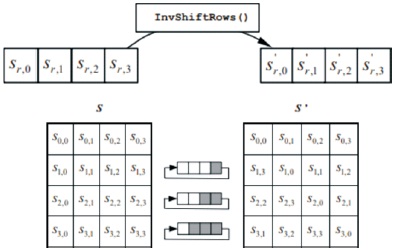
Figure 14. InvShiftRows cyclically shifts last three rows (FIPS PUB 197, 2001)
InvMixColumns: InvMixColumns transformation is the inverse of MixColumns. it operates on the State column- bycolumn, treating each column as a fourterm polynomial. ( FIPS PUB 197 ,2001)
InvAddRoundKey: In InvAddRoundKey, the transformation is on its own inverse with the application of the XOR operation.
Figure 15 shows AES encryption pre round module output in hexadecimal code. Figure 16 shows AES encryption pre round module output in binary code. Here we are taking input data as 128 bit and key is 256. For pre round module operation 128 bit key is used. The Pre round operation means: In the AES algorithm encryption first round is shown in Figure 5. Here we are taking 128 bit input (plain text) and key is 128 bit (means half from the main key). Both input data and key perform XOR operation in pre round operation. The output is shown in Figures 15 and 16. These outputs are sent to next operation that is Sub Byte operation. This is implemented in Verilog using XILINX 14.5 Software.
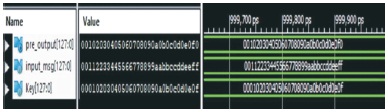
Figure 15. Pre Round Module Output in Hexadecimal of AES Encryption
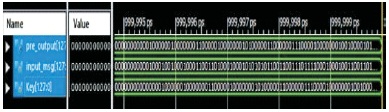
Figure 16. Pre round module output in binary of AES Encryption
In this paper, different AES encryption techniques of schemes to attain high throughput with low power and less area are discussed. All the existing architecture techniques are studied and analyzed. Each architecture techniques are unique and applicable for different applications. The AES algorithm is very secure compared to DES and Triple DES. The AES key could not be cracked till date, because of length of key and round functions mainly. This paper represents the survey of AES cryptography secure algorithm. Cryptographic algorithms are more prone to side-channel attacks, so we implemented this algorithm instead of using a lookup table-based approach. The proposed technique is AES-256 algorithm design and implementation in Verilog using XILINX 14.5 Software.