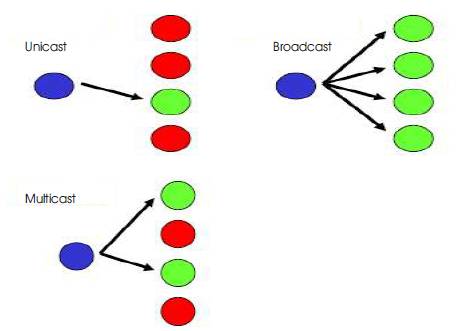
Figure 1. System models of unicast, broadcast and multicast networks
Multicast is communication between a single sender and multiple receivers on a network. Multicast routing in Mobile Ad hoc Networks (MANETs) poses several challenges due to inherent characteristics of the network such as node mobility, reliability, scarce resources, etc. There are many protocols that can help multicast data transmission. Agent based multicast routing is one of the ways to achieve multicast routing in an efficient manner. There are lot of concerns and challenges in adhoc environment in multicast routing like tree based or mesh based, mobility manner, and traffic in the adhoc environment. An Agent can be hardware or software program and it can be used to get routing information, source and destination nodes information. The desirable character is to reduce flooding of packet, minimum end to end delay and maintain reasonable packet delivery ratio. Three agent based protocols are taken from different environment and studied by their working nature of their agents. The protocols are ASSM, MAMR and ABMRS. Analysis of the nature and limitations of these protocols help to understand agents in an adhoc network and identify the base for agent based multicast transmissions.
Multicast is the delivery of a message or information to a group of destination nodes or hosts simultaneously in a single or multi-hop transmission from the source. There are many protocols in adhoc environment to achieve multicast transmission like MAODV, ODMRP etc, These protocols can be classified into tree based protocols, mesh based protocols, and hybrid protocols. All the three classes of multicast routing protocols use flooding as a basis for the construction of a mesh or a tree and for other multicast management functions. The flooding technique involves considerable amount of control traffic on the network, this would result in an overhead on the low bandwidth. In agent based protocols a separate mobile or static agents are created and they can move or stay static throughout the network and get the information about adhoc environment like traffic and moving speed of the nodes. Agent can get the traffic information and provides the desired path for the source to transmit the data. 'Multicast' the technical word means one to many, that is from one sender to many receivers and there are many techniques of any cast. Any cast is defined as transmitting the data to the nearest neighbour in the network in group transmitting, (or) any cast is nothing but transfering the data to a group of members having same destination address.
Figure (1) shows that unicast is the term used to describe communication where a piece of information is sent from one point to another point. In this case there is one sender, and one receiver.eg., Ethernet. Multicast is the term used to describe communication where a piece of information is sent from one or more points to a set of other points. In this case there may be one or more senders, and the information is distributed to a set of receivers. Example of multicast technique is sending an e-mail message to a mailing list. Teleconferencing and videoconferencing is also used for multicasting, but it requires more robust protocols and networks. Broadcast is the term used to describe communication where a piece of information is sent from one point to all other points. In this case there is just one sender, but the information is sent to all connected receivers. ASSM: Agent Based Source Specific Multicast Routing Protocol for Wireless Mesh Networks using agents to transmit data in the mesh network. ASSM based on source specific multicast routing use more than two agents. Mobile Agents Aided Multicast Routing (MAMR) protocol is a hybrid protocol where intelligent mobile agents have been integrated with existing on-demand multicast routing protocols such as Multicast Ad Hoc On-demand Distance Vector (MAODV) routing protocol, On demand Multicast Routing Protocol (ODMRP) and others.

Figure 1. System models of unicast, broadcast and multicast networks
Agent Based Multicast Routing Scheme (ABMRS) in MANETs, uses a set of static and mobile agents [1]. The scheme operates in the following sequence: 1) identify reliable nodes, 2) connect the reliable nodes through intermediate nodes, 3) construct a backbone for multicasting using reliable nodes and intermediate nodes, 4) join multicast group members to the backbone, 5) backbone management and group member's management in case of mobility. These protocols use five agents to achieve multicasting. There are lot of ways to compare routing protocols but here the important thing is behaviour of agent in different environments and how they are helping or working to build a multicast environment.
There are no certain definitions for an agent in adhoc environment. According to different kinds of network, an agent may have different characteristics. It may be static or mobile around the network. It may be hardware, a special node that move around the network or static node to monitor the network population and routing information or may be a software program which means a packet that flow through the network and actually update the information on every node for the multicast transmissions. The desirable characteristics of a mobile agent are,
Wireless mesh network (WMNs) consist of mesh routers and mesh clients. Mesh client can be stationary or mobile while mesh router have minimum mobility. Specific-source multicast (SSM) is a multicast service model in which the datagram is transmitted by a source S to an SSM destination address G, and receivers can receive this datagram by subscribing to channel (S,G). It uses tree topology with core node which is the multicast source of the group. For each multicast group, each forwarder of the group knows its head node, which is the node through which it receives packets coming from the group source. Also each forwarder have a list of its downstream nodes which are neighbour nodes registered to receive multicast packets of this group [3]. A forwarder must have at least one neighbour node which is registered to receive multicast packets or it should withdraw from being a forwarder. By using the forward node, the node in the network informs its position to the source. Once this forward node reaches the core, it creates one backward agent and transfers all its memory to it and die. The backward agent reach the source and give the information about the nodes which need to are all want to receive the multicast data. In this way the route is identified using agents. Agents are also used by nodes to join the multicast group. There are four types of agents used to achieve the multicast transmission.
When a node decides to join a multicast group, its start to launch forward agents toward multicast group core in specified time intervals. A forward agent will use a probabilistic vector of its multicast group at each node to choose the next hop and randomly travel through the network nodes until it reaches the group core. When a forward agent passes a node, it stores a node id in its memory and after reaching the core will pass its memory to backward agent. Time to live field in forward agent packets can be set according to network dimension so that forward agents that cannot manage to reach the destination in appropriate time and are wondering around the network are discarded automatically [3].
When forward agent reaches the core of the multicast group it will launch a backward agent toward a node on how one wants to join to the group and transfer its memory to this agent and die. Backward agent travel the reverse path travelled by forward agent and at each intermediate node and at the destination update the local routing information and probabilistic vector of this multicast group [3].
When a node considers joining a group using a path provided by backward agent, it will launch a reserve agent and the backward agent memory will be transferred to this agent. Reserve agent will travel a reverse path travelled by backward agent until it reaches a group forwarder or the group core. When a node receives a reserve agent of a multicast group, it will set the flag to forward the data packet for this group [3].
When a multicast group member considers using another path or wants to withdraw from receiving multicast packets, it launches a release agent to its head node. Upon receiving a release agent, forwarder node removes the sender from the list of receiving neighbours of this multicast group and the release agent dies [3].
All the work is done through the agents, so there is less work for remaining nodes in the network. There is a less chance for flooding because the routing is done through a defined technique.
Too many agents and the agents are moving forward and backward periodically and it needs a certain movement of nodes. It is harder to implement new mobility models for this protocol. Creating an agents in frequent interval may cause heavy traffic, if the number of nodes are large. The reserve agents are not required for simple mobile network as it will waste the time and increase the packet overhead.
Mobile Agents Aided Multicast Routing (MAMR) protocol workes like a hybrid protocol using intelligent mobile agents. It can be integrated with existing on-demand multicast routing protocols such as Multicast Ad Hoc On-demand Distance Vector (MAODV) routing protocol, On demand Multicast Routing Protocol (ODMRP) and others. Agents are small software programs or packets that can be send through the network to get or modify the information in nodes.
MAMR uses the concept of reachability to find the multicast route from source to destinations [4]. Every node has reachability table which contain whether the destination node can be reached through the node. The work of the software agent here is to update the neighbour information when moving from source to other nodes. The mobile agents are simple packets that are generated at selected nodes in the network. The mobile agents move across the network and collect information such as node id, and QoS values related to the parameters like link delay, congestion etc. This information is used for updating the reachability table. When a mobile agent arrives at a node, the reachability table is updated for the neighbour node on which the mobile agent arrives. If the regency value for the node brought by the mobile agent is greater than regency value of the node stored in the reachability table, then it updates with regency value contained in the mobile agent packet. After it completes all its tasks, it randomly chooses one of the neighbour nodes for its next move.
A no return principle is employed for mobile agents to avoid looping in the network i.e. it will not choose the neighbour node which it has already traversed. Then the remaining part is like normal on demand protocols sending request for path but the request is sent only to its neighbour in the reachability table. After finding the route the transmission takes place. If no entry exists in the reachability table for the destination node, then the protocol follows broadcast route discovery mechanism of MAODV.
Little agent idea forms MAMR concept, and it may help for better transmission of packets and avoid packet loss. It can be implemented easily by just adding little packets called agents.
Agents are nothing, if the network size is small and it is like waste of bandwidth and increasing packet overhead. It mostly works like normal multicast protocols without agents if the density of the network is minimum, and then there is no use of agents. Earlier references show only little advantage over MAODV in all parameters.
Agent Based Multicast Routing Scheme (ABMRS) in MANETs, uses a set of static and mobile agents. The scheme operates in the following sequence: Identify reliable nodes, connect the reliable nodes through intermediate nodes, and construct a backbone for multicasting using reliable nodes and intermediate nodes, join multicast group members to the backbone, backbone management and group member's management in case of mobility. It uses reliability factor to find the reliable node and use it for multicast transmission. The agents are defined clearly as combination of many factors and the definition is as follows: Agents are autonomous programs which sense the environment and act upon the environment using its knowledge to achieve their goals [4].
An agent environment is generally referred as a host system, network, a user via a graphical user interface, a collection of other agents, or perhaps all of these combined. Agents are classified as single agent and multiagent systems. Single agent systems comprise of a single agent interacting with resources, humans and other processes to perform a dedicated task. Multiagent systems comprise of set of agents that interact, cooperate, and coordinate with each other to perform a set of tasks or a dedicated tasks. Mobile agents are multiagent systems, which roam in the network to achieve their goals. The agents are clearly defined according to their working nature. Five types of agents are used in the scheme: Route manager agent (static), Network initiation agent (mobile), Network management agent (static), Multicast initiation agent (mobile), and Multicast management agent (static) [5].
It is a static agent responsible for creating other agents, agents actions synchronization and the knowledge base. It computes the reliability factor of a node and sends the information to its neighbours periodically.
It is a mobile agent which performs collection of reliability advertisement packets from neighbours and declares itself as a reliable node and it has highest reliability factor among the advertised packets. NIA is periodically generated by RMA. Period of generation depends on the mobility of the nodes.
It is a static agent, which has easy connection maintenance between nodes and manage circumvent mobility problems.
It is a mobile agent, which is used to construct a multicast group using the multicast key and travel to reliable nodes and request multicast transmission. After performing the initial membership survey and collecting the necessary group membership information, MIA forms an initial multicast tree comprising of reliable nodes, intermediate nodes and group members, and provides the Group ID to all the members of the packet-forwarding nodes in the multicast tree and destroys itself.
It is a static agent and does the function of multicast tree maintenance. It resides on all the group member nodes and acts to repair connection breakage between the child node and the reliable node.
It comprises of network information like type of the node, multicast group IDs and forwarding table, responsibility list, connection list, status of connectivity, status of group member, etc.
The routing is performed by five steps as mentioned in the earlier steps and the protocols agent does all the work to perform multicast routing.
Agents are clearly defined and work of agents are identified by a clear paradigm. It controls flooding and increase the efficiency of the multicast transmission. Agents are designed to destroy themselves after a particular period. So the network does not get more agent than nodes.
Agents are more in number. It takes time to do all the work and communication between node and agents and knowledge base and agents. If the network size is the whole paradigm is not worth to implement. If the network is chang in rapidly then it is difficult to collect the information from it and to form the multicast backbone.
The above mentioned protocols use agents to implement multicast routing in adhoc environments. The importance is given to agents and their working nature and how efficiently they are used to implement a multicast adhoc network. The routing methods of these protocols are not discussed deeply. The conclusion of this work is, Agent based multicast routing is not efficiently used to deploy multicast networks in adhoc environments. The agents must be designed and assigned works according to the environment, size of the network and mobility speed of the nodes. It is not an easy task to design a general agent based paradigm to create multicast networks. An agent may be anything like software program, hardware node, or human interaction with the network or combination of all the above. If someone use all the above in a needful manner then that will be the best for real time implementation of multicast adhoc environments.