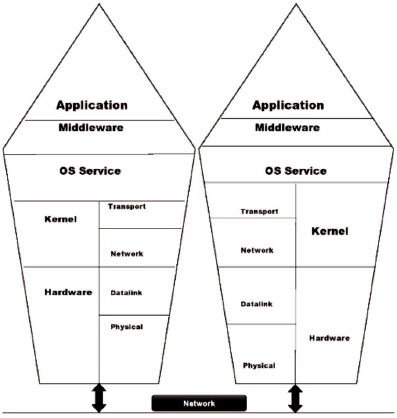
Figure 1. Different Layers of Logical Organization of Distributed Systems
Recently, security in software is becoming complex, especially in distributed computing. A secured and trusted environment is critically important for distributed computing. Different services and resources in the distributed system have to be secure at different levels; therefore, in this paper, we have analyzed in detail the flaws of the distributed systems, common security threats, common scenarios at which the system faces risk, and the best possible solutions to secure the distributed system. Globus security mechanism is discussed in detail as how the authentication can be done and how message confidentiality and integrity can be achieved. Every idea that radiates all sorts of solutions to this matter is verified and analyzed. This paper provides necessary knowledge to help one understand the meaning of a secure system, the security policies, and the security mechanism.
The consistency of security tactics preserved by distributed systems is a significant threat (Firdhous, 2012). Authentication, authorization, encryption, system protection are few of the essential elements in the distributed system (Bai, 2008; Chatterjee et al., 2017). Basically, a distributed operating system gathers details from different autonomous computers connected to a distributed computing system and recognize them as computational nodes. Essentially, a distributed operating system addresses an expansion of the OS utilized in networks that aids more significant data exchange and blends of the system across the networks (Sinha, 1998; Tanenbaum & Steen, 2007). The distributed system comprises different layers in the logical organization as shown in Figure 1.

Figure 1. Different Layers of Logical Organization of Distributed Systems
In the beginning stage, the system of the security environment has been reliant upon a single authority structure. Presently the improvement has been made concerning each activity, trained professional, and gathering with shared obligations. The fundamental assaults on distributed systems are snooping (getting access towards confidential information), disguising (hides the personality of clients), tampering data (destroying or editing data), replying, and rejecting the system administrator. The reliability of the distributed system is significant in various environments (Prakash & Darbari, 2012). The concern over security in the distributed operating systems is increasing with the emerging innovation. Notwithstanding, if the assailant has actual intention with the attack on the proposed system, it would be difficult to secure the framework concerned (Xu et al., 2003). Different fundamental components of safety have been shown in Figure 2.
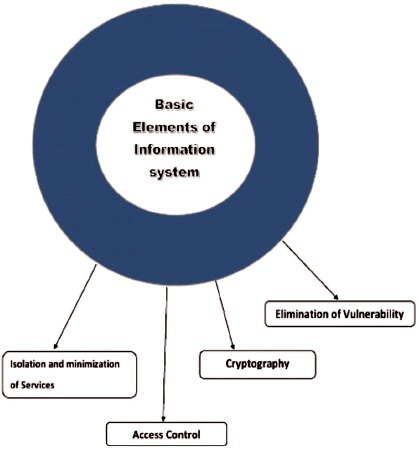
Figure 2. Essential Components of Data System Security
As we move forward connected to the world of computers, we realize that they are becoming increasingly distributive as we focus on the geographical aspect (Nuredini, 2013). The purpose of distributed systems is to connect and collaborate between different computing or institutional communities. Enterprises have considered extending the collaboration and data sharing belonging to varying businesses among other cooperation entities that will fulfill the need and utilize capital assets and processing (Jiang et al., 2012). The distributed systems hold a common ground and goal to entail the interactive activities between various distinctive independent entities (Bai, 2008). In simpler terms, in a distributed system, CPUs of nodes do not function as part of a whole system. To its users, it is displayed as any other ordinary centralized operative system. From the beginning, security has been an issue bearing the most important, that if not handled with proper care, might harm the enterprises and the user communities massively (Demir & Khan, 2010; Ding et al., 2012; Koshutanski, 2009). Due to these scenarios, this paper aims to explain the concept behind security issues and the preventative measures taken against them in distributed systems.
In Firdhous (2012), the author aimed for researching the security of distributed cluster, grid, database systems, and distributed storage using the technique of grid authentication method, CIAA (Confidentiality, Integrity, Availability, and Authentication) threat model, multilevel secure database system which has benefited him in terms of improvement in the security of distributed resources, distributed data, and grid computing. In Ghafari et al. (2015), authors went on to research on secure framework for ATMs using the mechanism of SFAMSS framework having the benefits to ensure confidentiality, non-repudiation and integrity. In Prakash and Darbari (2012) the authors reviewed security issues in distributed systems using the mechanism of Path authentication technique which has the advantages of ensuring a secure grid environment. In Uzunov et al. (2012) authors worked on the evaluation of reliability patterns by adopting the method of reliability pattern approach and its benefit in terms of system design and development. In Huang et al. (2010) worked on providing security and protection in distributed system using the mechanism of a non-exclusive structure for threefactor validation that benefited in terms of affordable smart card application due to its efficient design. Applying distributed management system architecture, Sloman et al. (1993) had researched on isolating administration strategy from robotized administrators which has the advantages of automated distributed systems dealt by the automated manager. Thakur and Chaudhary (2013) researched on detection of content sniffing attacks using the algorithm of automatic file rendering and have its advantages of securing the programs against content sniffing attacks. They also used the potential features of DoS attack which has benefited in terms of reduction in time required for detecting DoS attack. In Sirbu and Chuang (1997), the authors had researched on enhancing the security and scalability of distributed systems using Kerberos framework and using Public-key cryptography which is good to achieve fully distributed authentication. Research on secure communication in distributed systems has been done by Stading (2003) using the mechanism of Identity- Based Encryption which is favorable for secure, efficient, and authenticated communication in a distributed systems. The summary of the related works are presented in Table 1.
Four types of security threats in the distributed system are:
Interception: An unauthorized user endeavors to access assistance or information. For example, replicating information, sniffing passwords.
Interruption: Services or data become blocked off, unusable, or demolished, for instance, denial of service attacks, wiping out of data.
Modification: Unauthorized persons access the data as well as change the data or meddling with assistance so it no longer holds quickly to its subtleties. For instance, it is obstructing and changing conveyed data, modifying a program so it subtly logs the exercises of its client.
Fabrication: An unauthorized user inserted a fake message into the network. For example, we have included a passage to a secret word data set, replaying recently sent messages.
This figures out what is secure for the framework or association, or substance. It essentially alludes to the limitations on the attributes of the individuals and regulations forced upon the foes by different procedures. So, a security policy exercises the components in a structure allowing to accept and deny (Hamdi & Mosbah, 2009).
A distributed system's security mechanism is envisioned for forestalling or recuperating from a security assault. A security administration essentially utilizes at least one security instrument. Generally, a security administration improves the security of the information preparing frameworks (Sloman, 1994; Yao, 2003).
Encryption: Data are codified which the assailant cannot grasp.
Validation: checks the declared character of a part.
Authorization: grants components to simply get to those resources that are equipped for access.
Auditing: logs which clients got to where and what they have.
The internet server running on a grouped framework gives mechanisms to secure the framework against:
Heterogeneity is applied to the organization, PC equipment, working framework, and in execution of various designers. Middleware is an important component of the heterogeneous dispersed system in a customer working environment. Middleware is a bunch of administrations that empowers applications and end-client to connect across a heterogeneous disseminated framework (Tillwick & Olivier, 2004).
The straightforwardness of the dispersed framework is settled basically by how much new asset-sharing associations can be made open to the clients. Accessible designs are depicted by how their key interfaces are appropriated. It depends upon a uniform correspondence section and scattered interface for enlistment to shared assets. It will, as a rule, be made from heterogeneous equipment and programming (Tillwick & Olivier, 2004).
The adaptability of the framework ought to stay effective even with a critical expansion in the number of clients and assets associated (Tillwick & Olivier, 2004).
The security of a data system has three parts: confidentiality, integrity, and availability. Encryption secures shared assets, maintains delicate data secrecy when communicated (Tillwick & Olivier, 2004).
When a few issues happen in equipment and the product program, it might deliver erroneous outcomes, or they may stop before they have finished the proposed calculation. So restorative measures have to be executed to deal with this case (Tillwick & Olivier, 2004).
Concurrency: There is a likelihood that few clients will endeavor to get to a common resource simultaneously. Different clients make demands on similar assets, i.e., read, compose, and update. Every resource should be protected in a similar environment (Tillwick & Olivier, 2004).
Transparency: Transparency guarantees that the appropriate framework ought to be seen as a solitary substance by clients or the application software as opposed to the assortment of independent frameworks, which are coordinating (Tillwick & Olivier, 2004). The client should not be informed about where the administrations are located, and the transition from a neighboring computer to a remote one should be simple.
Execution problems Responsiveness: Intelligent applications need a quick and predictable reaction. The response is determined not only by the server network load and execution, but also by the deferrals in all the item parts involved, i.e., the OS, the middleware (for example, farflung strategy ideas like name), and the application code itself providing assistance.
Throughput: This is the rate at which computational work is completed (number of customers updated per second), and it is influenced by planning speeds, as well as the speeds at which consumers and workers move data.
Balancing Computational Loads: Servers that are overburdened when possible, use a few servers to host solitary support and offload work, for example, an applet on a web server (Domingo-Ferrer & Mateo-Sanz, 2002; Qi et al., 2010; Samarati, 2001) to the client. In a distributed system, cycles (for example, customer-side and server-side cycles) collaborate by exchanging messages, resulting in correspondence message passing (Vijayarani & Jothi, 2014; Toshniwal, 2013) and coordination synchronisation and exercise request (Pallickara et al., 2007). Every interaction has a distinct state. Communication execution (Sawant et al., 2013), for example, is frequently a limiting feature, and there is no single global notion of time because timekeepers on diverse PCs will be in general drift. There are three methodologies for insurance against security threats.
Vulnerability: It demonstrates a deficiency in the framework that empowers an assaulting specialist to make unseemly malignant performance (Priyadarshini et al., 2019).
Threat: A danger is something pointed toward hurting the framework.
Compromise: It alludes to the effect of the weak assault.
Exploit: It means that software takes advantage of a framework's weaknesses and limitations.
Payload: This alludes to executing the activities prearranged as the point of the concerned assault.
Rootkit: It alludes to a bunch of projects that shrouds the existence of the aggressor concerned.
Malware: This is the nonexclusive name for pernicious projects.
The different sorts of external attacks that can happen are outlined in Figure 3.
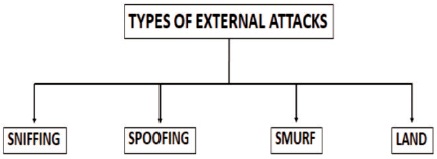
Figure 3. Different Types of External Attacks
Sniffing is an interaction of checking and catching all information parcels going through a given organization. Sniffers are used by the network/structure head of an organization to screen and investigate network traffic. Aggressors use sniffers to catch information parcels containing delicate data like passwords, account data, and so forth.
Spoofing is the point at which an aggressor imitates an approved gadget or client to take information, spread malware, or sidestep access control frameworks. There are various sorts of Spoofing, with three of the most well-known being: IP address parodying - Attacker sends packets over the organization from a bogus IP address.
A Smurf Attack is a Denial-of-Service (DoS) attack that involves delivering ICMP reverberation requests (ping) traffic to the transmission addresses of switches and other network devices in large PC networks with a spoofed source address, i.e., the location of the ideal DoS target (Thakur & Chaudhary, 2013).
If the first request (to a device in a large network) is sent to a large number of machines, the subsequent assault can be extremely powerful. Regardless, most switches do not send items delivered to transmission addresses after 1999. As a result, the chances of a successful massive extension Smurf Attack are quite low (Thakur & Chaudhary, 2013).
It has been described as the event of deceiving the individual in issue while communicating with them.
Many assaults on computer systems are associated with particular types of assaults.
This includes the way toward assuming control over the vital data from different machines.
Lately, there has been a considerable proportion of information concerning burglaries, for instance, Visa number burglary, tampering ATM, electronic money robbery, data set burglary, etc.
Distributed DoS and identity assaults generally happen in the distributed framework (Khan et al., 2018).
Distributed DoS (DDoS) attack is an assault where the primary reason for the aggressor or programmer is to annihilate the help of assets utilized by the real client when this assault happens in the dispersed framework, then it is called distributed DoS attack (Harinath et al., 2017). A DDoS attack is one in which a large number of disrupted frameworks attack a single target, causing a DoS on the targeted client framework. The influx of approaching messages to the objective framework effectively forces it to shut down, denying genuine customers access to the framework. In a typical DDoS attack, a hacker exploits a flaw in one PC system and turns it into the DDoS ace. The intruder identifies and communicates with various frameworks that can be settled using the expert framework (Specht & Lee, 2003). The intruder downloads a variety of breaking tools from the internet. The intruder instructs the controlled computers to launch one of numerous flood assaults against a predetermined target with a single command. DDoS attacks can also cause more widespread disruption. During the year 2010, a massive DDoS attack knocked out Myanmar's whole internet infrastructure. A zombie is a computer that has been extensively impacted by an intruder (Le et al., 2016; Peng et al., 2002). Figure 4 illustrates the various types of DoS attacks.
DDoS prevention is being researched by researchers.
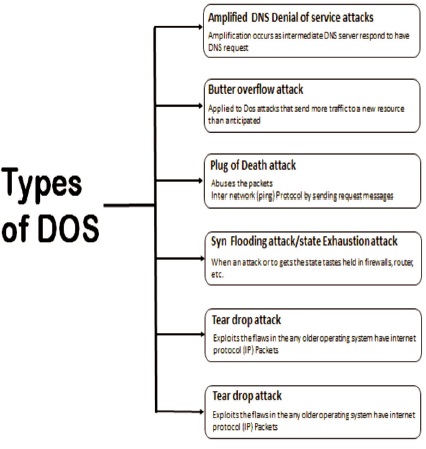
Figure 4. Types of DoS Attacks Security
DDoS prevention is being researched by researchers.
IP filters are used by several ISPs to try to prevent various types of attacks. Malicious packets with known marks or potentially bad TCP/UDP choices are flagged by ISPs. This also eliminates a large number of attack paths. Governments can also assist in the event of such attacks by implementing methods on particular ISPs to block specific routes and subnets if attacks occur. These efforts, however, are extremely local, and even ISPs in the same country frequently do not share information about banned IPs or dangerous hosts.
A few organisations monitor web activity and compile a unique list of IPs with a risk rating. This enables the observer to determine the extent and duration of Internet-related blackouts, as well as the limited impact of such blackouts. ICMP (ping) is used in a lot of these checking projects, but it is not a huge percentage of the time. As a result, we use TCP and UDP to test availability to the Internet core framework and amongst Team Cymru scenarios. The focus of the investigation is on DNS and BGP, the two most fundamental administrations.
For example, Group Cymru examines the explicit Internet fundamental framework. This enables the observer to determine the extent and duration of Internet-related blackouts, as well as the limited impact of such blackouts. ICMP (ping) is used in a lot of these checking projects, but it's not a huge percentage of the time. As a result, we use TCP and UDP to test availability to the Internet core framework and amongst Team Cymru scenarios. The focus of the investigation is on DNS and BGP, the two most fundamental administrations.
The one significant security threat is authorization. It is a system that shows if a massive activity is allowed. Same as other asset sharing structures, matrix figuring frameworks need asset explicit and explicit approval. Secure Channelbased authentication is a sort of verification that upholds the protected exchange of validation information. It is utilized in blend with Cronto pictures or QR codes to exchange the Secure Channel messages. This verification process requires the utilization of Digipass licenses activated using multi-device licensing (MDL) (Huang et al., 2010). The working of the Secure Channel-based authentication is shown in Figure 5.
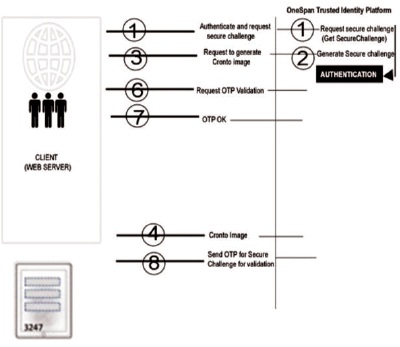
Figure 5. Secure Channel-Based Authentications
The authorization system is divided into 2 categories in the grid computing system. The first one is considered as VO (virtual organization) level system, and the second one is a resource level system. VO framework has a unified approval system that gives credits for the administrators to gain admittance to the assets. Apart from that, resource level structures are decentralised, allowing customers to make purchases based on the credits accumulated by the heads (Huang et al., 2010; Neuman, 1993).
VO Level System: VO, a dynamic group of individuals or groups of firms, elaborate the terms and conditions (business goals and procedures) for sharing funds. VO caliber grid computing organization is a centralized authority for the whole VO. Structures are made huge if the VO is accessible there, which includes sets of customers and various Resource Providers (RP) who are the owners of the assets for being worked by the heads of the VO. On the other side whenever a customer wants to get to the particular resources asserted by RP, they have an accreditation from the approval framework, which lets the administrators guarantee the explicit right.
Resource Level System: Other than a centralized authorization system, decentralized systems have implemented the decisive step to make authorization to get access to the set of assets. Asset suppliers offer offices to the local gatherings. This interaction is completed to acquire the trust relations of local communities. On the other side, an end client wants to get their hands on the assets; they create their accreditations that have acquired unmistakable strategy attestations. The asset supplier has to concede or deny the solicitation for admittance to the support. The end clients introduce the certifications to the resources to gain admittance to it. In this sort of structure, the resources need to hold over the last position to supporting or keeping the system from getting end clients.
Large scale distributed computing system has specific concern towards data integrity such as the grid whose soul production is the outcome of the computation. If data integrity ought to be maintained, then the system must be resistive towards the aggressor attacks. The security mechanism is dependent on two categories, transportlevel security and message-level security (He et al., 2009; Xu et al., 2003).
Transport Level Security: The network connections on the transport layer are encoded by TLS and SSL. Asymmetrical cryptography has been used in TSL and SSL for the vital exchange; symmetrical has been used in message authentication codes for message integrity and privacy integrity. For the security of the communication between the client and the server, Globus Toolkit 4.0 (GT4) uses the SSL/TLS protocol over HTTP as shown in Figure 6.
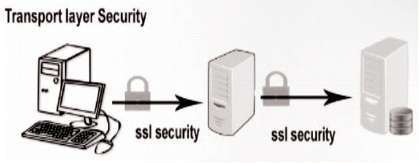
Figure 6. Transport Level Security
Message Level Security: This operates at the upper level and uses the web services based on WS-Security, WSSecure Conversation, etc. which are the standard protocols. These standard protocols propose to establish plus use specific context and SOAP messages (Simple Object Access Protocol). Initially, a secure framework is created between a client and a server. If the security framework is established, then the following messages are signed utilizing the XML-signature standard. XML-signature works with a symmetrical key to sign messages which is also the reason for its fast operations, but additional round trips are also required to maintain connections. This procedure works properly for several interactions. GSI operates the system to give security on a per-message basis, i.e., there is no pre-existing situation between the receiver and sender to an individual message as shown in Figure 7.

Figure 7. Message Level Security
There are two special encryption techniques known as symmetrical and asymmetrical (public) used for making secure grids.
The single secret key is shared to perform to encrypt as well as decrypt information. To make sure that the data is only revealed between two users (the one who sends the message and the one who receives the message); the key should only be given to the two users who are sender and receiver. Regarding performance, this form of encryption dominates asymmetrical encryption but should be handled more carefully with additional administrative care of the shared key. Some examples of symmetrical key protocols include Data Encryption Standard (DES), Rivest Cipher 6 (RC6), and Advanced Encryption Standard (AES). The exchange security relies upon symmetrical critical protection. Suppose an aggressor captures the symmetrical key; he will read the cipher text and create a new one as shown in Figure 8.
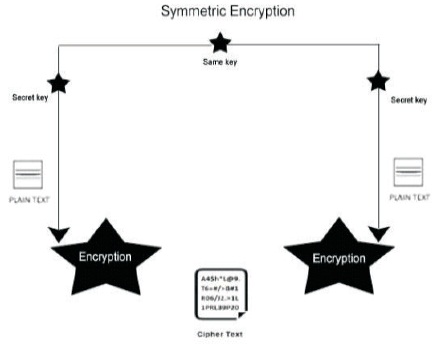
Figure 8. Symmetric Encryption
This produces public key as well as private key pairs dependent on cryptographical secure mathematical methods. Assume a communication is encrypted with the public key and can only be decrypted with the private key. Everyone can see the public access. The symmetrical key is responsible for the computation, which starts with the discovery of two incredibly huge apparent numbers. Even if the public key is widely published, computers will be unable to calculate the private key from the public key. The security fact is that exceeding hundreds of digits is difficult. This mathematical approach improves security, but it necessitates a very long encryption time, especially for data in the access amount. Figure 9 shows how public key encryption is used to send symmetrical encryption keys between the two groups, and then symmetrical keys are used for further encryption.
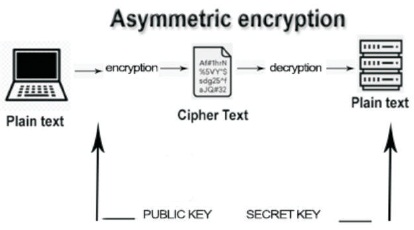
Figure 9. Asymmetric Encryption
Secure groups can be elaborated as:
In support of FCY, every time a member joins or leaves, the group keys should always be changed. There might be a high value. Hence, attempts should be made to put FCY at ease without removing security in both Ensemble and the DVPN system (Shehab et al., 2008).
With the help of the Access Control List (ACL), members' trust policies are elaborated. Other than the above 3 requirements, another requirement allows members to change their ACLs (Sawant et al., 2013) dynamically.
Assume a conference of military staff with full assistance from civilian advisors, where the four requirements are described in motivation. While the meeting's security is low, they distribute low-security information to the advisers. Previously, the gathering has been defined by common citizens leaving the room, while the tactical staff continued to complete the community with the use of high-security data. High-security information had not been shared while civilians were still there (He et al., 2009).
Assuming a model is the best way to establish this policy and the way that security instruments provide in distributed systems to implement such types of strategies. In the Globus Perfect Forward Secrecy (PFS) security policy, group keys cannot be used on a large scale (Bai, 2008). Globus is a framework for massive-scale distributed computation, in which several hosts, records, and assets are used to do the calculation at the same time. Computational frameworks are another name for these conditions (Xiaoyong et al., 2010).
The security plan for Globus incorporates accompanying assertions:
Although there are several administrative domains, each section has local security. Furthermore, because the field participates in Globus, it is believed that local policies cannot be amended. As a result, guarantee in Globus prevents it from working, which can cause problems in a few areas related to this problem. Furthermore, Globus understands that local tasks to a domain are only subject to the security policy of the domain in question. The Globus security method indicates that various activity solicitations can be launched locally or globally. The initiator can be a client or a service that is following on behalf of a client and is only known to the initiator inside each domain (Chang-Ji et al., 2003).
When a client or a service that follows a client is validated, it is critical to double-check the precise access rights to assets. A client seeking to refresh a document, for example, will first be validated; a short time later, it will be determined whether the concerned client is actually permitted to update the record. The Globus security strategy depicts access control decisions being made locally inside the realm of the accessed resource's location. Furthermore, Globus focuses on security threats, implying a variety of fields. In particular, the security strategy exhibits the portrayal of a client in any distant domain, just as the distribution of assets from a far-off domain to a client or the agent. The architecture of the Globus security strategy is as demonstrated in Figure 10.
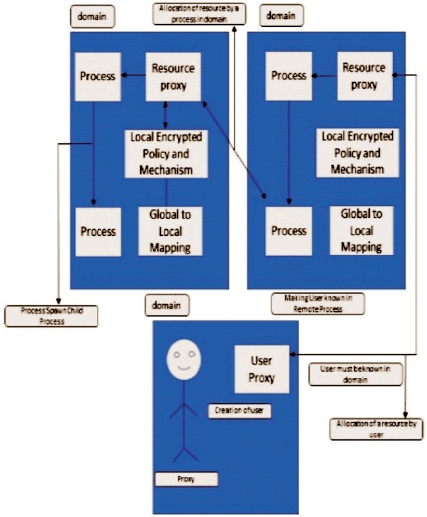
Figure 10. Architecture of Globus Security Policy
The reliance existing among administrations concerning trust brings about the thought of a Trusted Computing Base (TCB). A TCB addresses a bunch of all security instruments in a disseminated PC framework that is vital for guaranteeing a security strategy needed to be trusted (Pallickara et al., 2007; Stallings, 2006). The more modest the TCB is, the better it will be. Besides, TCB in a distributed system can consolidate the neighborhood working frameworks at a few hosts. A document worker in a disseminated record framework may be accepted on the few assurance components managed by the local operating system (Xu et al., 2003; Yu & Singh, 2002). Besides, middleware-based distributed systems need to confide in the current local operating system. If there is no trust, a portion of the local operating system's utility must be integrated into the distributed system (Priyadarshini et al., 2019).
Different sorts of safety approaches are utilized to make a safe distributed system and is explained in Table 2. The few important approaches are trust-based, authentication based, cryptography techniques based and access control-based.
The authentication procedure is proposed in Shehab et al. (2008). It is suggested that domains be empowered to protect themselves in a cooperative environment by using an on-request path finding algorithm. In a recent paper, a transportation mechanism for accessing drugs in authorised distributed systems has been developed (Pallickara et al., 2007). Heterogeneously distributed systems are extremely useful in a variety of applications, such as electronic exchange handling systems and stock statement update systems that require authentication, integrity, and confidentiality. Systematic security-driven planning engineering is introduced in Xiaoyong et al. (2010). This strategy has been proposed for DAG (Direct Acyclic Graph). The methodology powerfully gauges the trust of every node. The verification of the remote client is a significant exploration region in the distributed systems. A three-factor-based validation approach is discussed in Huang et al. (2010). In this, two-factor validation has been stretched out to three-factor verification; it guarantees customer security proficiency in disseminated frameworks. The three components used to foster this methodology are, password, smart card, and biometrics. In Vitti et al. (2014), different parts of the security in distributed systems have been given including, user authentication using passwords and digital certificates and confidentiality in information transmission. The job of authentication servers in distributed computing systems has been examined in Chatterjee et al. (2017). The primary plan issue is the cryptographic calculations, synchronization, and measure of trust. The methodology depends on a notable authentication protocol, called Kerberos.
It is created for different applications (Ramana et al., 2010), similar to the P2P framework. This model provides a significant part in securing the framework of the distributed application. An extended D-S theory-based trust model (ExDSTM) is created in Jiang et al. (2012). Other D-S hypothesis models are proposed (Huang et al., 2010; Wang & Sun, 2009; Yu & Singh, 2002). A dynamic and context-sensitive trust-based security component has been created. The concept presented by Lin and Varadharajan (2006) applies risk management for trust based security decisions by maximizing the utility. Further, this new approach has introduced way to link security system with risk management to achieve economical benefits through utility maximization.
Essentially, data security access control is about figuring out who gets access to what materials (documents, catalogs, applications, and so on). For example, if an employee accesses the organizations system, they would be able to access reports permitted by the their login privilege. Someone in the finance department, on the other hand, would have to audit financial records. However, someone outside the organisation would be unable to access any of these resources.
Objects, on the other hand, could be valuable resources that need to be protected from unauthorised access, use, or disclosure. Furthermore, the client (or a group of clients, or even non-individual entities such as applications or administrations) is the subjected to the privileges login control. Thus, access controls (in a broader sense) are the devices, mechanisms, models, and tools that enable one to grant or deny access to extended or physical resources in the organization. This includes anything from restricting or authorising access to specific documents and databases to IT frameworks and physical locations.
Essentially, these types of physical and permanent restrictions prevent unauthorized people from doing what they are not supposed to do with the vulnerable infrastructure or information. Moreover, they also help prevent accidental disclosure or disclosure of sensitive material.
The cryptographic framework in a distributed system basically represents a device level security handle. Public key cryptography, software agents, and XML binding innovations are designed for this methodology. The improvement of secured distributed framework utilizes different methodologies, similar to Public Key Infrastructure (PKI) and Role-Based Access Control (RBAC). In Chang-Ji et al. (2003), the RBAC approach is utilized to foster verification dependent on Public Key Certificates (PKC).
Hamdi and Mosbah (2009) proposed a framework for specification, verification and implementation of security policies.
Based on a set of abstractions, this framework allows to write modular security policies that are independent of the distributed system. Here, security policies can be implemented without expertise in computer security.
Uzunov et al. (2012) surveyed different technologies available in securing distributed systems using patterns. They also reviewed a number of pattern-based security methodologies, evaluated their maturity and appropriateness for securing distributed systems.
Quorum systems are relevant in addressing the issue of information consistency in distributed fault-tolerant systems. Zhou et al. (2010) introduced an Intrusion- Tolerance Quorum System [ITOS] of half breed time model dependent on Trust Timely Computing Base (TTCB). Quorum-based access structures include threshold systems and they can be applied to multiple distributed control and management tasks.
Self-protection is a framework for identifying illegal practises and retaliating in the form of countermeasures. De Palma et al. (2012) suggested a technique for reviewing, implementing, and evaluating one's own framework. It is possible to improve the design of distributed security frameworks and the genetic algorithm is utilized for this reason by Bykovyy et al. (2008). The security heterogeneity approach for redundant models in an appropriate framework is developed in Xie and Qin (2007). A novel heuristics scheduling algorithm is introduced, that seeks to increase the likelihood that all business layers run without the risk associated with an attack. In Cappello et al. (2005), XtremWeb design has been discussed, which encompasses operation in large distributed system. The architecture of the system and parallel programming paradigms are explained well overall. A proposal for secure exchange in a mobile system dependent on the delegate object model is explained in Shenbagavadivu and Savithri (2012). It centers around client side encryption and remote storage of encrypted content in a mobile system. The RAIN project is discussed in Bohossian et al. (2001), which is a coordinated effort between Caltech and NASA-JPL on common processing. A few validation applications are created: like an exceptionally accessible web server and video server communicated through checkpoint frameworks. A legitimate Information Flow (LIF) scheduler is introduced in Enokido and Takizawa (2007) to synchronize transactions to prevent illegal information flow.
Many security approaches are discussed (Le et al., 2016; Prakash & Darbari, 2012; Rhee et al., 2005) to make distributed environment secure. These are authentication Based Security, Pattern-Based Security, Policy-Based Approaches, Trust-Based Security, Quorum Based Security Systems, and other security technique (Le et al., 2016; Prakash & Darbari, 2012; Rhee et al., 2005).
Due to extensive adoption of distributed computing architectures, computing infrastructures are vulnerable to threats. We evaluated background solutions that were developed to safeguard the distributed system in this survey report. The security issues of distributed systems need to be investigated further. In a previously published studies, researchers from industries, organizations, and academia have proposed viable answers to these security concerns. The DDoS attack was discussed in detail with possible solutions. We believe that by addressing the shortcomings indicated in this survey report, a comprehensive solution capable of safeguarding distributed systems can be achieved. Many advancements in the development of safe and trusted distributed systems include authentication, access control, cryptography, quorum, trust based models, etc. These attacks had happened in the past can happen in future in any distributed system. The solutions to these attacks have been summarised and contrasted in this work. In contrast, after taking into account all of these factors, the distributed system is likely to be more adaptable and secure.