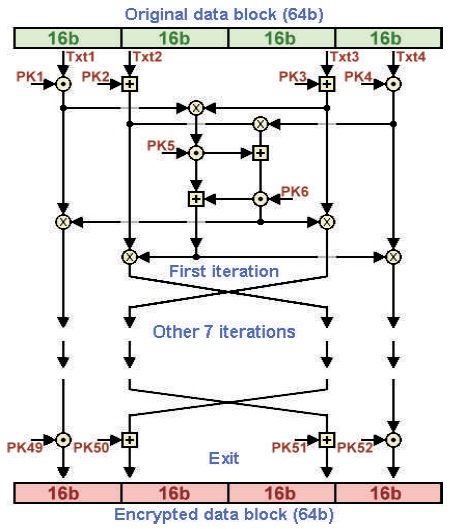
Figure 1. IDEA Encrypted Data Block
Now-a-days as the trend is to go online in every field like E-commerce, Banking, security is one of the main concerns. Some of this information additionally incorporates delicate data such as personal information or top secret government documents. So it is very important to protect personal data and information. Only DES or IDEA may be attacked by different sorts of cryptanalysis utilizing parallel procedure. In this paper, the author implements a symmetric key algorithm combining with two symmetric key algorithms, i.e. IDEA and 3DES with some modifications in order to improve the security and make it more complex for the attackers to break this algorithm. Using the combinations of these keys, we get 2^ (56+128) =2^184 that is 3.32 times stronger than conventional DES and 1.44 times stronger than conventional IDEA algorithm. The recommendation of S-IDEA algorithm is that it likewise be actualized in equipment utilizing VLSI innovation.
Internet is the base of all the online applications whether it is in the field of technology, e-commerce, banking sector, or social media. So it is about one's protection and security. Some of these data also include sensitive information such as individual data or top mystery government records as well as financial information. It is very important to protect their personal data and information, which is going online. So regarding this we are working on IDEA and DES algorithm to protect their privacy and Personal Information. It is essential to secure this delicate information against unapproved individuals (Nakahara, Preneel, & Vandewalle, 2003). This is the place encryption comes in. Cryptography is the investigation of scientific procedures, which aims to solve the information security aspects, such as confidentiality, information uprightness, substance verification, and information beginning authentication (Forouzan, 2008). Encryption is a good way to protect data. All the key calculations like DES (Data Encryption Standard), IDEA, RC4, RC5 (Rivest Cipher 5), etc., use basic permutations and basic mathematical calculations, that's why it is so fast. Here in this paper, a symmetric key algorithm has been implemented combining two symmetric key algorithms, i.e. IDEA and 3DES with some modifications in order to improve privacy. The Data Encryption Standard (DES) algorithm has been a well known mystery key encryption calculation and is utilized in many commercial and financial applications (Biham & Shamir, 1992). It is introduced in1976; it has demonstrated impervious to all types of cryptanalysis. IDEA was used as the symmetric cipher in early versions of the Privacy crypto framework. IDEA was to add to a solid encryption algorithm, which would replace the DES procedure created in the USA. in the seventies. It is likewise fascinating in that it entirely avoids the use of any lookup tables or S- boxes. IDEA was there in the first place decision for information encryption taking into account its demonstrated outline and its great reputation. In IDEA, the pre-existing algorithm uses 128-bit key and 8 rounds. In this way, the IDEA algorithm is improved in terms of security by adding greater level of diffusion and confusion using 3DES concept (Yide, 2005).
Symmetric Key Encryption Algorithms are likewise called as Secret Key Encryption algorithms. In such calculations, the sender and recipient utilize a similar key for encryption and decryption reason.
Blowfish Algorithm is a standout amongst the most efficient algorithm which is created by Bruce Schneier in 1993. It is additionally a block cipher figure Symmetric algorithm, which utilizes 64 bits square size of plain text. It has a key length fluctuating from 32-448 bit. In its first stage, the calculation utilizes key development, where 448-bit key is changed over into number of sub keys totaling 4168 bytes (Bhalla & Nagrath, 2013).
In 1991, James Massey and Xuejia Lai propose another symmetric key encryption algorithm. The algorithm is gotten from Proposed Encryption Algorithm (PES). It utilizes just 8 rounds and every round uses XOR, addition, multiplication tasks. The all out number of key utilized are 52 and the key size differs from 64 bit to 128 bit. IDEA is not yet broken by any straight or arithmetical attack.
1.1 Overview of IDEA Algorithm
In many commercial and financial applications, Data Encryption Standard (DES) algorithm is used because it has been a popular secret key encryption algorithm although DESI introduced in 1976 according to current standards it takes approximately 22 hours to search entire 56-bit key space (NBS, 1977). IDEA is a block cipher and was first described in 1991. It is a minor modification of a prior figure, PES (Proposed Encryption Standard); IDEA was originally called IPES (Improved PES) (Yang, Li, & Hao, 2004). IDEA was utilized as the symmetric cipher as a part of early forms of the Pretty Good Privacy cryptosystem. IDEA was developed as a strong encryption algorithm, which will replace the DES algorithm (NIST, 2012). which was developed in the seventeenth century IDEA was originally called as IPES as it is minor revision of earlier called algorithm PES (Demirci, Selçuk, & Türe, 2003), IDEA was usually used as symmetric cipher in early versions. Though IDEA is strongest Cryptographic algorithm, IDEA is not as popular as DES because of two main reasons, viz.
IDEA is block cipher algorithm. Like DES algorithm it also works on a block of 64 bit, but the key is longer and it is consisting of 128 bits (Chen, Xue, & Lai, 2008). IDEA uses both diffusion and confusion for encryption. Like DES is used in both ways, i.e. for encryption and decryption.
Step in Each Round
In Figure 1, there are eight rounds in IDEA and each round involves a series of operations on the four data blocks using six keys (Hellman, 1979). There are several steps as shown below, which includes multiplications, addition, and XOR operations:

Figure 1. IDEA Encrypted Data Block
Step 1. Multiply* P1 and K1
Step 2. Add* P2 and K2
Step 3. Add* P3 and K3
Step 4. Multiply* P4 and K4
Step 5. XOR the results of step 1 and step 3
Step 6. XOR the results of step 2 and step 4
Step 7. Multiply* the results of step 5 with K5
Step 8. Add* the results of step 6 and step 7
Step 9. Multiply* the results of step 8 with K6
Step 10. Add* the results of step 7 and step 9
Step 11. XOR the results of step 1 and step 9
Step 12. XOR the results of step 3 and step 9
Step 13. XOR the results of step 2 and step 10
Step 14. XOR the results of step 4 and step 10
The asterisk (*) sign in the above mentioned steps indicates that the addition and multiplication is not simple addition and multiplication, but it is addition modulo 2^16 (i.e. addition modulo 65536) and multiplication modulo 2^16 + 1 (i.e. multiplication modulo 65537).
3DES algorithm was born in order to increase security and privacy. It is a symmetric block cipher algorithm, in which 64-bit information scramble and decrypt (Curiger et al., 1993). The information encryption and decoding calculation are using the same structure, but keys used in decryption are in reverse order. The length of keys is 64-bit, but each 8-bit block is containing parity bit so after removing parity bit, the length of keys is 56-bit. And very little keys are considered as the weak keys, but they can be easily avoided. In DES algorithm, encryption and decryption process can be divided into five steps: (1) 64- bit key produces 56-bit key using PC (Permuted choice) and after that 56-bit produces 16 sub-keys through a Subkey algorithm which are K0, K1...K15 used, respectively each are 56-bit long and these keys are again passed through PC-2 and generate 48-bit key from 0, 1, .15 are used in each round from 1 to 16. 64-bit plaintext was rearranged after the IP (Initial Permutation) and divided into MSB (L0), which is the left 32 bits and LSB (R0) which is the right 32 bits. First R0 is directly assigned to L1 and after that R0 is encrypted by the sub-key K0 through some encryption function f(R, K) and result is 32 bit data set. The resultant 32 bit XOR with L0 to generate R1 is as shown in Figure 2.
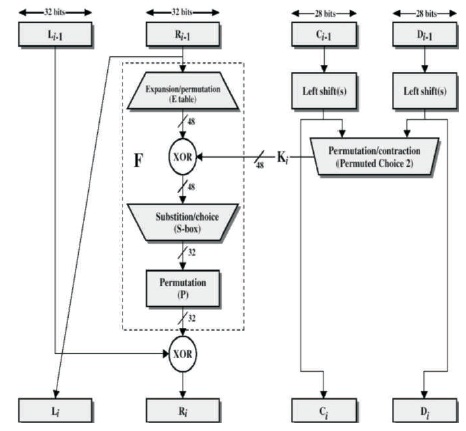
Figure 2. DES Encryption Process
L i = Ri-1
Ri = L i-1 ⊕ f (R i-1, K I)
where i = 1,2 ,3,…, 16
Thus the first iteration encryption is completed. Now this new generated R1 and L1 is used in second iteration. (4) The second iteration encryption to the sixteenth iteration encryption keys were used to sub-keys K1 ... K15, and their processes are same to the encryption in the first iteration. At the end of the sixteenth iteration encryption, it creates a 64-bit data set. Its left 32-bit (MSB) is considered as R15 and the right 32-bit (LSB) is L15. After that merged (R15, L15). The information encryption and decoding in order to produced 64-bit information set. 64-bit encrypted algorithm is messages will be got by the data rearranged through IP-1(Inverse initial permutation). Inverse DES encryption process (decryption process) and using the sub-key Ki (in reverse order), the encrypted messages can be decrypted.
S-box is a very important and critical step in DES algorithm, which is a more complex nonlinear function and all other operations are linear. By the S-box, plaintext has been able to express well as the confusion to have strong security. Algorithm complexity and security depend on S-box and function. If function is more complex than we improved data security and no one can easily decrypt message. But function complexity also affects overall speedup in encryption and decryption algorithm. S-box take m bit as input and output of S-box is n bit. In DES S-box take 6 bit input and output of s-box is 4 bit as shown in Figure 3.
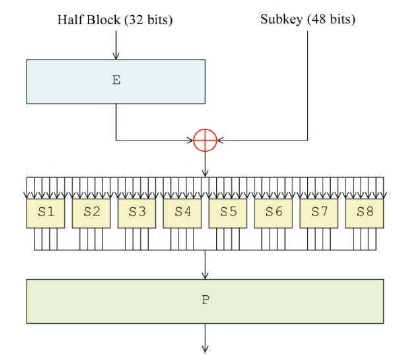
Figure 3. DES S-Box
Steps involved in S-box
For input S [0]: (X0, X1, X2, X3, X4, X5) --> (Y0,Y0,Y2,Y3) Processing step: X1X2X3X4 as a column and X0 X5 as a row in Table 1 is given below.
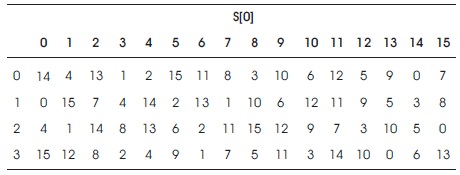
Table 1. Working of S-Box
3DES is only an adjustment to the more established DES encryption that relied on the balanced Feistel network. Basically, 3DES is just DES connected three times to the data that is being encrypted. 3DES is a more secure than DES algorithm. 3DES algorithm is the cumulative computing of the three times DES algorithm that is the process of Encryption - Decryption - Encryption. In order to obtain higher security, three keys should be separate. 3DES the encryption key is restricted to 56 bits as directed by the DES standard. Be that as it may since it is applied three times, the implementer can have 3 discrete 56 bit keys, or 2 indistinguishable and 1 discrete, or 3 indistinguishable keys. This implies 3DES can have encryption key size of 168, 112, or 56-bit encryption key lengths, respectively. But due to certain vulnerabilities while reapplying the same encryption thrice, utilizing 168 bits has a reduced security equal to 112 bits and utilizing 112 bits has a reduced security equivalent to 80 bits. But in this paper, the author has used two different keys and two different algorithms in order to improve security that is shown in below diagram.
According to Table 2, the comparison among various security algorithms is shown.
Key= z, input size= y, combination to break the key=2^z (key size).
E.g. - In IDEA algorithm, Brute Force attack to encrypt=2^z (key size). =>2^128 combinations.
In 2DES algorithm, Brute Force attack to encrypt=2^z (key size) =>2^112 combinations.
In DES algorithm, Brute Force attack to encrypt=2^z (key size) =>2^56 combinations.
In this proposed symmetric key algorithm, in Figure 4 two concepts i.e. triple DES and IDEA algorithm are combined with a novel approach (Clavier, Gierlichs & Verbauwhede, 2008). In case of triple DES, we have three DES modules, but instead of that we are using one IDEA module in place of the second DES module increasing the confusion and diffusion (Nakahara, Preneel & Vandewalle, 2003). In case of Triple DES, we use three 64 bit keys, but in this approach we used only two keys, one 64 bit key for both the DES modules and another 128 IDEA module. So the two DES modules use a single 64-bit key with active 56 bit key so we get 128 possible keys. The reason why we are using only two keys one for two DES modules and one for IDEA module is generating 64 bit keys and 128-bit key can be quite cumbersome in a general purpose system (Nakahara, Preneel & Vandewalle, 2004), so to reduce that overhead we use only two keys. But using the combinations of these keys we get 2^(56+128)=2^184 that is 3.32 times stronger than conventional DES and 1.44 times stronger than conventional IDEA algorithm.
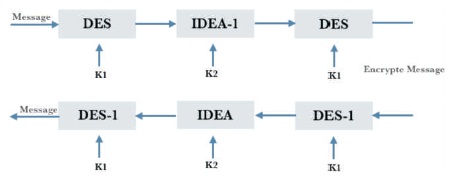
Figure 4. IDEA-DES Process Model
Table 3 shows the results for the execution time taken for different encryption algorithms, which are implemented in C language.
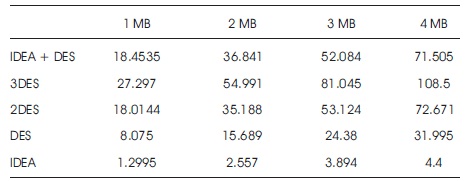
Table 3. Execution Time of Encryption Algorithms
The graph between different encryption algorithms and size of input data shown in Figure 5 is drawn from the tabular data. The results show that IDEA algorithm takes minimum time for encryption for input with different size. But the proposed algorithm (DES-IDEA-DES) has the same security with less time than 3DES.
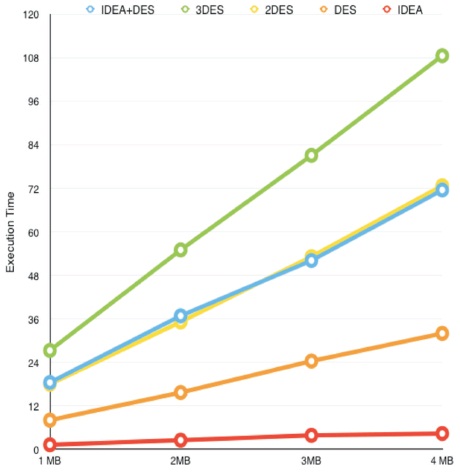
Figure 5. Graphical Representation of Execution Time
An Enhanced IDEA (International Data Encryption Algorithm) is a universally applicable block encryption algorithm, which allows the powerful security of transmitted and stored data against unauthorized access by third parties. The Enhanced IDEA (International Data Encryption Algorithm) is a strong block-cipher. Though there are many operations included in the whole calculation, just three diverse operations are involved and also increased rounds in algorithm builds the security of a calculation. The Enhanced IDEA (International Data Encryption Algorithm) eliminates the weak keys problem of an IDEA (International Data Encryption Algorithm) by key scheduling of an IDEA (International Data Encryption Algorithm). With a key of 128 bits in length; Enhanced IDEA is far more secure than the widely known also, unique IDEA. The proposed calculations expanded the cryptographic strength and eliminate the shortcoming of the existing International Data Encryption Algorithm (IDEA). The future scope of S-IDEA algorithm is that it likewise be actualized in equipment utilizing VLSI innovation.