Figure 1. (a) Cellular Network (b) Mobile Ad hoc Network (Hoebeke et al., 2004)
Cognitive Radio Networks (CRNs) are the key technology for the efficient utilization of spectrum in wireless networks in a dynamic manner. Mobile Ad hoc Networks (MANETs) using cognitive radio (CR) capability (CR-MANETs) has opened many areas of research. Among them routing in CR-MANETs is a challenging issue. Dynamic MANET On-Demand (DYMO) routing protocol is the successor of Ad hoc On-Demand Distance Vector (AODV) routing protocol. The drawback of AODV is that it does not support larger networks. It is resolved by DYMO routing protocol as it scales larger networks. But, DYMO does not support small network sizes with low mobility speeds. In this paper, CR-DYMO routing protocol for MANETs using cognitive capabilities is proposed using CogNS simulation framework to enhance the QoS performance for all network sizes. The simulations are evaluated using the various performance metrics, such as Average Throughput, Packet Delivery Ratio, Average End-to-End Delay, Routing overhead, Normalized Routing Load, Mean Jitter, Energy Consumed, and Energy Left through responsive (TCP) and non-responsive (UDP) traffic agents. From the results, it is observed that the Modified CR-DYMO routing protocol performs better when compared to DYMO and defacto CR-DYMO through the above-mentioned performance metrics under TCP and UDP traffic agents.
A computer network is a collection of independent devices that are interconnected to exchange the information between the sender and receiver nodes. Computer networks are broadly categorized into two types namely wired and wireless networks. Both wired and wireless networks have their own capabilities. Wired networks (Esmaeelzadeh et al., 2013) transmit data through a wire or cable. Wired networks have more transmission rate, enhanced security, highly reliable, and ensure less bit error rate compared to wireless networks. The communication in wireless networks is propagated through the free space without any wires (Schiller, 2003; Gast, 2005) and utilizes high-frequency radio waves. Wireless communications facilitates in providing high mobility, adaptability, and extensibility.
Wireless networks are basically of two types: Infrastructure (cellular or one-hop) networks and Infrastructureless (Ad hoc or multi-hop) networks (Chuah & Zhang, 2005) as shown in Figure 1 (Hoebeke et al., 2004). In cellular networks, each user directly communicates to the access point or base station whereas Ad-hoc network does not rely on fixed infrastructure and each mobile node communicates with other through wireless links in a multi-hop manner. Mobile Ad hoc Networks (MANETs) are a type of ad hoc network consisting of a collection of wireless computing devices, such as mobile phones, laptops, Personal Digital Assistant (PDAs), or homogeneous autonomous devices, which interconnects and transfers with one another with lack of centralized management (Attada & Setty, 2015). Nodes in these networks are self-configuring, self-organizing, multi-hop having the capability of acting as a sender, receiver as well as a router to carry out information exchange as well as control information (Chlamtac, Conti, & Liu, 2003). The list of main challenges associated with MANET includes the Dynamic topology of the network, Bandwidth utilization, Routing, Frequent link breakages, the High mobility of nodes, Energy constraints, Routing with security and privacy, Quality of Service, Scalability, and Robustness (Jorg, 2003).
The electromagnetic radio spectrum is a valuable natural resource used by transmitters and receivers approved by governments. The Federal Communications Commission (FCC) have planned for improving the way in which this valued resource is governed in the United States (Communications Commission, 2002; Haykin, 2005). But the underutilization of electromagnetic spectrum causes inefficient use of spectrum. The electromagnetic spectrum under utilization is named as spectrum hole. A spectrum hole is a group of frequencies allotted to a primary user, however, at a specific time and particular geographic position, the band is not used by that user (Kolodzy, 2001). The spectrum hole is shown in Figure 2 (Akyildiz et al., 2006).
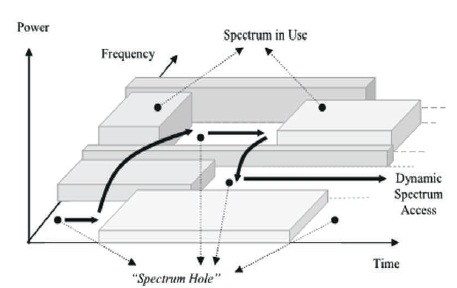
Figure 2. Concept of Spectrum Hole (Akyildiz et al., 2006)
The underutilization of the radio spectrum can be resolved using Cognitive Radio (CR). The term “Cognitive Radio” was first used by Dr. Joseph Mitola in 1999 in his Ph.D. thesis and in a number of publications. CRs are smart radios that can independently make decisions using collected information about the Radio Frequency surroundings through model-based perceptive and can also acquire and strategize according to their earlier experience (Mitola, 2000). Cognitive radio is a target-driven framework in which the radio independently notices the radio surroundings, deduces context, measures alternatives, produces strategies, administers multimedia services, and acquires from its faults (Mitola, 2001). The elementary idea of CR networks is that the unlicensed devices (also called cognitive radio users or secondary users) must vacate the band once the licensed device (also known as a primary user) is sensed (Akyildiz et al., 2006, 2009). The ultimate objective of cognitive radio is to obtain the best available spectrum through cognitive capability and re-configurability. Sharing of the licensed spectrum without conflicting with the transmission of other licensed users is the most significant challenge (Akyildiz et al., 2009). The four main functionalities of cognitive radio networks are Spectrum sensing, Spectrum management, Spectrum mobility, and Spectrum sharing.
With the intention to provide additional bandwidth for the increased demand and to accommodate existing and new services, users of both spectrum policy architects and communication technologists are discovering solutions to the spectrum scarcity. Borrowing of the spectrum from spectrum licenses is the notion started by FCC to accommodate unlicensed users to provide the essential bandwidth required by existing and future wireless services and applications. This method of spectral usage is known as dynamic spectrum access. With the growth of CR technology adaptable spectrum access to the licensed and unlicensed users is provided (Unlicensed operation in the TV broadcast bands, 2004; Federal Communications Commission (FCC), 2008).
Two Mobile Stations (MS) which are within communication range can exchange their information while those which are not within direct communication range can exchange information over multi-hop relay nodes. In order to eliminate the disadvantage of the local information of each MS, collaborative algorithms (Yu et al., 2011) are normally used for this type of architecture, where the local observation results are exchanged among the MSs to widen the knowledge on the network. This type of network is called as Cognitive Radio Mobile Ad hoc Networks (CR-MANETs) (Yu et al., 2011). The key feature of CR-MANETs is that they are “spectrum aware”. The following are some of the main features of CR-MANETs different from traditional MANETs which consists of two types of users-primary users and secondary users, Choice of transmission spectrum, Topology control, Multi-hop/ multi-spectrum transmission, CR-MANETs are more dependent on “delay tolerant” routing protocols.
In this paper, the performance evaluation of proposed CR-DYMO routing protocol with traffic agent TCP and UDP through CogNS framework is investigated using metrics: average throughput, average end-to-end delay, packet delivery ratio, routing overhead, normalized routing load, energy consumed, energy left, and mean jitter.
The drawback of AODV is scalability, that is, it does not support larger networks. But DYMO is scalable for larger networks and it is not suitable for smaller network sizes with low mobility speeds so the objective is to enhance the QoS performance of DYMO routing protocol by using Cognitive Radio to support all network sizes.
In the literature, a lot of research work and studies are carried on cognitive radio networks. In (Akyildiz et al., 2009; Akan et al., 2009; Cormio, & Chowdhury, 2009; Cesana et al., 2011; Issariyakul et al., 2009; Shah et al., 2016; Timalsina et al., 2013; Zareei et al., 2016; Pathak et al., 2010; Kamruzzaman, 2010), some of the important challenging issues and studies were going on in the different layers and especially on MAC layer of CRNs is explained. However, there are confined simulation frameworks for multi-radio multi-channel in wireless networks (Calvo & Campo, 2007; Wang, 2017; Chiueh et al., 2017; Dutta & Sarma, 2017). These frameworks do not support dynamic spectrum access, therefore, cannot be used for simulation in Cognitive Radio Networks. In (Di Felice et al., 2011), the author proposed a CRAHN simulator based on NS2 and this simulator uses two radio transceivers for each CR node and the used spectrum management introduces routing overhead because of agreement phase between CR nodes. In spite of having some simulation frameworks for multi-radio multi-channel networks and supporting cognitive radio networks, it is important to develop a simulation framework which increases the simulation and evaluates the scenarios and protocols in cognitive radio networks. In this paper, Cognitive Network Simulator (CogNS), a simulation framework for cognitive radio networks built on NS2 is used (Esmaeelzadeh et al., 2013). In (Mahamuni et al., 2011), the authors discuss the need to include sensing in the design of the transport protocol and evaluated the performance of throughput with and without routing and also end to end delay. In (Cacciapuoti et al., 2010), the author proposed CADOV for CRAHN based on AODV protocol and the results reveal the effectiveness in Cognitive radio ad hoc network. In (Rout & Sethi, 2013), the author analyzed the performance of Spectrum using the metric throughput and observed that the quality and efficiencies of the spectrum is high for less number of secondary users.
In (Ruslan et al., 2014), the author employed Ad-Hoc On- Demand Distance Vector (AODV) and Weight Cumulative Expected Transmission Time (WCETT) routing protocols to specify the efficient route choice between the source and destination nodes in Cognitive Radio Ad-Hoc Network (CRAHN). In (Selvakanmani, & Sumathi, 2014), the authors confer about Cooperative Opportunistic Routing protocol for Cognitive radio MANET (CRCN CORMEN) routing protocol using packet delivery ratio, delay in a cooperative way among the mobile nodes, when compared to the existing Cooperative communications.
In (Mansoor et al., 2015), up-to-date progress of cognitive radio ad-hoc network architecture is specified and the established mechanisms and performance assessments of the studied architectures were analyzed.
In Mobile ad-hoc networks, routing protocols are mainly classified into three types. They are Proactive routing, Reactive routing, and Hybrid routing protocols. Proactive routing protocols are also called Table-driven routing whereas reactive routing protocols are called On-demand or dynamic routing protocols (Attada & Setty, 2015). Reactive routing protocols are most popularly used in MANETs because they have less routing overhead when compared to proactive routing protocols and are more scalable (Attada & Setty, 2015). AODV, DSR, and DYMO are popular examples of reactive routing protocols.
DYMO (Dynamic On-demand MANET routing protocol) is a successor of AODV routing protocol, reactive, multi-hop unicast routing protocol. The basic functionality in the DYMO protocol is route discover y and route maintenance. In route discovery, a source node initiates dissemination of a route request (RREQ) packet throughout the network to find a route to the destination node. During this dissemination process, each intermediate node stores a route to the source node. When the destination node obtains the RREQ, it answers with a route reply (RREP) packet directed towards the source node. Each intermediate node that accepts the RREP packet establishes a route to the destination node, and then the RREP is unicast en route the source node. When the source node obtains the RREP, routes are built between the source node and the destination node in both the directions. Route maintenance involves two functions. Firstly, active routes are preserved and the nodes stretch their route lifetimes upon successfully forwarding a packet to the next hop. Secondly, the flow of traffic through the links is monitored by the nodes when the network topology changes. When a route for the destination is unknown or the link is broken, the originator node of the packet is notified. A route error (RERR) packet is sent toward the originator to indicate the existing route to a particular destination is invalid or not reachable. When the originator node receives the RERR, it removes the route. If the source node has to send a packet to the same destination, it is required again to perform route discovery process for that destination (Wister et al., 2011). The disadvantage of AODV routing protocol is that it is not scalable for higher network sizes, however DYMO is meant for both moderate and higher network sizes (Venkataramana & Setty, 2017).
Primary users play an important role in the performance of cognitive radio networks and the modeling of Primary Users (PU) activities is a vital task in CRNs. Since the arrivals of PUs are considered to be independent, inter-arrival time can be designed with exponential distribution. Therefore, primary user activity is modeled as two-state (ON and OFF) Markovian process with ON state means the channel is busy and OFF state means the channel is idle. The entrance and the departure rate of PUs of a channel are denoted as re and rd. The steady-state probabilities are evaluated as follows (Esmaeelzadeh et al., 2013; Bolch et al., 2006).
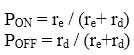
This model is used for simulating primary user activities in CogNS framework.
Spectrum Sensing is the process of finding free channels that are free of the primary user activity so that the CR user can operate on the free channel in CRNs. Therefore, spectrum sensing is the first main important task in cognitive radio networks and the accuracy of sensing plays a vital role in CRN performance. Spectrum sensing accuracy is measured using two parameters, namely, the probability of detection (Pd) and the probability of false alarm (Pf) (Tang & Mark, 2009). The probability of detection is the probability that a channel sensed is occupied by primary users and the channel busy is detected by the spectrum sensing. Probability of false alarm is the probability that CR user senses the channel is busy, but the channel in the spectrum is not occupied by primary users. The higher probability of detection leads to the lower interference with the primary user by the CR user. From the CR users context, the lower false alarm probability leads to increased use of spectrum, thus the performance of CR network will be enhanced. Maximum A Posteriori (MAP) Energy Detection for spectrum sensing is known as an optimal sensing scheme (Proakis, 2011). These models are used for simulating the sensing accuracy in the CogNS framework.
The probability of detection and a false alarm in MAP energy detection are modeled in terms of Q function as follows (Lee & Akyildiz, 2008).
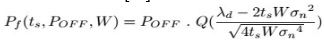
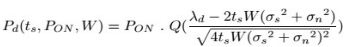
where POFF and PON are calculated by using equation (1), W is the bandwidth of the sensed channel, and ts is the duration of sensing; the σs2 and σn2 are the variances of the received signal and the noise, respectively; λd is the decision threshold of MAP energy detection.
CR users are incorporated with CR transceiver which perceives and chooses a free channel from the table of existing free channels and uses it. These capabilities are simulated in CogNS. All of the nodes are configured with equal fairness and same capabilities. The structure of each CR node object of CogNS, modules, timers, and relationships among them is shown in Figure 3 (Esmaeelzadeh et al., 2013).
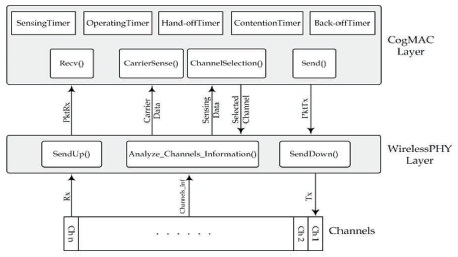
Figure 3. Cognitive Radio Node Object Structure in CogNS (Esmaeelzadeh et al., 2013)
As shown in this figure, the MAC layer, the physical layer, and the channels are changed on the basis of the structure of the mobile node object in NS2. The indicators between different layers denote the delivering of the control information and data packets. The major change has been done on the MAC layer of the Mobile node in which a cognitive CSMA/CA-based MAC protocol is implemented and named as CogMAC in CogNS framework (Esmaeelzadeh et al., 2013).
In order to understand the behavior of a CR node, the multi-channel environment is to be provided. A single channel can be accessed by all the other wireless nodes through the physical layer in NS2. So, the physical layer is connected to a group of channels as shown in Figure 3. The number of channels can be specified through TCL script. The physical layer (WirelessPHY) is responsible for controlling channels and administration. In this layer, a new module AnalyzeChannelsInformation() has been included to the NS2 wireless physical layer; also some alterations are done in some modules such as SendUp() and SendDown() to support the multi-channelstructure (Esmaeelzadeh et al., 2013).
The WirelessPHY has two stages in CogNS which are sensing phase and operating phase. In the operating phase, for the purpose of receiving a packet, the wireless PHY layer of a CR node has to monitor the channels on the basis of Round Robin algorithm. If a packet is present in a channel, receiving process (Rx) is invoked instantly and does not shift to a new channel till receiving the last bit in the packet. After receiving the packet completely, it is delivered to CogMAC layer over SendUp() procedure (PktRx). For the purpose of sending a packet, the wireless PHY layer of CR Node acquires a packet from CogMAC layer (PktTx) and sends it to the selected channel which is selected in the earlier sensing period (Tx). Sending is completed by means of the SendDown() procedure (Esmaeelzadeh et al., 2013).
In the sensing phase, usual modules of wireless PHY layer, i.e., sending and receiving the packets wait and the spectrum sensing is done to find the channels which are vacant of primary users. Having preexisting knowledge of PU actions, the existence of PUs are known for all of the channels; therefore CR users can observe the free channels in every sensing phase. After sensing phase, AnalyzeChannelsInformation() function directs the status of all channels to CogMAC layer on the basis of each channel information (Esmaeelzadeh et al., 2013).
A CSMA/CA based MAC protocol (CogMAC) has been implemented in CogNS. The basic modules operated in CogMAC layer are shown in Figure 3. The Sensing timer and Operating timers are used for sensing and operating phases, respectively and the channel hand-off is assumed through a Hand-off Timer. Back-off Timer and Contention Timer are used to assume the back-off and contention operations. After the sensing phase, ChannelSelection() function selects the appropriate channel for sending a packet based on the received information from WirelessPHY layer and the considered selection policy in tclscript.
Two policies are used for channel selection technique: (1) random policy and (2) QoS- based policy. In random policy, a channel is arbitrarily chosen from the available list of free channels. In QoS-based policy, a channel is chosen on the basis of preferred minimum channel interference QoS metric. Then, the chosen channel number is directed to the WirelessPHY layer. In the operating phase, the CarrierSense() function chooses about the condition of the intended channel on the basis of the information of other cognitive users in each channel which has been previously sent from WirelessPHY layer. Function Send() is responsible for sending a packet to WirelessPHY (PktTx) (Esmaeelzadeh et al., 2013).
Adaptive DYMO Routing protocol for Cognitive Radio Ad-hoc Network is named as the CR-DYMO routing protocol. Using CogMAC as the MAC protocol in the simulations, changes are made to the CR-DYMO routing protocol. The number of configurable parameters is set to a default value which is named as defacto CR-DYMO. These parameters are adjusted and fine-tuned experimentally to produce optimum result is termed as Modified CR-DYMO. The modified CR- DYMO will provide significant and better results when compared to normal DYMO and defacto CR-DYMO.
Table 1 presents the configurable parameters to be set in a Tcl file.
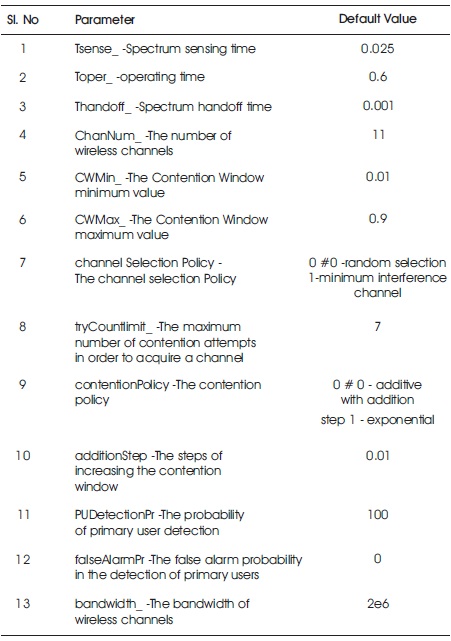
Table 1. Configurable Parameters Set in TCL File
Figure 4 shows the proposed CR-DYMO approach.
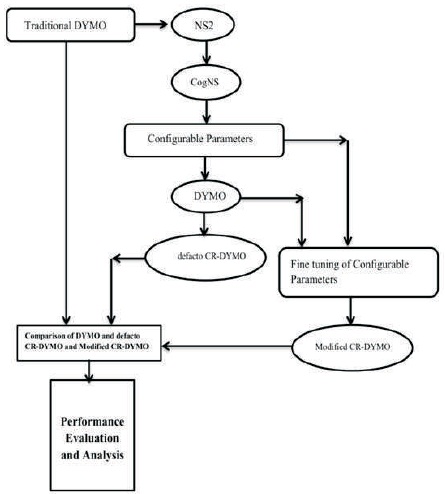
Figure 4. Proposed CR-DYMO Approach
The activity model of Primary User (PU) is given externally through a text file. Each row of the Primary User model file contains three field values separated by commas as follows:
channel_number, PU_arrival_time, PU_departure_time
where channel_number: this attribute indicates the number of wirelesschannels;
PU_arrival_time: this attribute indicates the primary user arrivaltime;
PU_departure_time: this attribute indicates the primary user departuretime.
In order to run the TCL file, the following command executed from the terminal window: ns test.tcl “address of PU-activity-file”.
In order to evaluate the designs proposed in this paper and to choose the most suitable evaluation methodology, three evaluation methodologies were identified.
1. Simulation
2. Experimental (Test bed), and
3. Mathematical
The mathematical methodology is too restrictive as it contains assumptions and hypothesis that cannot suit realistic and dynamic environments. Researchers would at the most need accuracy for further enhancement of their work and want to conduct their experiments on the real devices, using test beds. But, the experimental methodology is not practicable due to high cost and their lack of flexibility and setup for such networks, where experimentation is mostly accomplishable through simulation (Hogie et al., 2006). Simulation is an economical and an easy approach to carryout experiments. Research Methodology is shown in Figure 5.
Network Simulator 2 (NS2) is an object-oriented, discrete event-driven network simulator, which is highly reliable within the networking community and was developed first at the University of California-Berkeley. It supports both wired and wireless environments (Hogie et al., 2006). NS2 contains two key languages which are C++ and Object-oriented Tool Command Language (OTcl). The aim of C++ is to define the internal working exercised as backend of the simulation and the aim of OTcl is to establish the simulation by collecting and configuring the objects in addition to scheduling discrete events employed as frontend. So the combination of these two languages makes it powerful and efficient (Cavin et al., 2002).
The CogNS is designed on the basis of the open source network simulator (NS2). This framework is useful in understanding CRNs and facilitates the development of new protocols, validation of theoretical results, and performance estimation of CRNs at different layers. This framework is also used to study and estimate the effect of lower layers, i.e MAC and Physical layers. CogNS can be used to calculate the QoS metrics, such as average throughput, end-to-end delay, and packet drop, which is significant in real-time applications (Bhrugubanda, 2014).
The experiments are designed and conducted on Ubuntu OS 12.04 LTS with NS2 (Network Simulator 2) on CogNS simulation framework for the performance evaluation. The performance analysis is done on normal DYMO, defacto CR-DYMO, and Modified CR-DYMO using TCP and UDP Agent for Application traffic FTP and CBR, respectively. The performance assessment is done by means of QoS metrics Average Throughput, Average End-to-End delay, Packet Delivery Ratio, Routing Overhead, Normalized Routing Load, Mean Jitter, Total Energy Consumed, and Total Energy Left. The simulator parameters and their values are shown in Table 2.
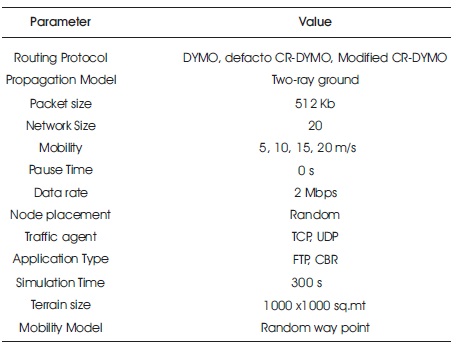
Table 2. Parameter Setting for Simulation Process
Figure 6(a) shows the simulation scenario initial setup in NS2.
Figure 6(b) shows the simulation scenario during execution in NS2.
Figure 6(a). Simulation Scenario Initial Setup in Ns2
Figure 6(b). Simulation Scenario during Execution in NS2
The performance evaluation of DYMO routing protocol in CRNs is evaluated through the CogNS framework. The metrics considered for performance evaluation and CRrelated parameters are described. Simulation results and analysis are presented in the next section.
Real-timedness and reliability are the two most important concerns which should be considered for provisioning Quality of Ser vice (QoS) in wireless networks (Esmaeelzadeh et al., 2013). In real-time applications, the reliability is highly required and it changes from one application type to another. In Wireless Networks, high throughput and low end-to-end delay are the necessary criteria to achieve QoS and reliability.
The real-time application capabilities in Cognitive radio networks increases and the authors investigate and analyze the impact of CR-DYMO routing protocol through CogNS in terms of Average Throughput, Average End-to-End Delay, Packet Delivery Ratio, Routing Overhead, Normalized Routing Overhead, Energy Consumed, Energy Left, and Mean Jitter. The traffic agent TCP and UDP is considered for the Application types FTP and CBR.
It is defined as the average number of packets successfully received from the source node to a destination node in a simulation amount of time. It is measured in bits per second using the formula,
Average Throughput = Σ(number of packets successfully received / total duration of simulation)*(8/1000)
It is defined as the percentage of total number of packets received against the total number of packets sent. Packet Delivery Ratio=Σ (total packets received)/ Σ (total packets sent)*100
It is defined as the average delay experienced by the packets to reach the destination (i.e., the sum of processing delay, transmission delay, queuing delay, and propagation delay).
Average End-to-End Delay =
where Np is the total number of received packets by destination nodes, tir is receive time of ith packet by the transport layer of the destination node and tis is send time of ith packet by the source node.
It is defined as the number of control packets produced for the data packets to reach the destination node.
It is defined as the average number of control packets produced for a data packet to reach the destination node.
It is defined as the total amount of energy consumed by all the mobile nodes for the packets to be transmitted from the source node to the destination node.
It is defined as the total amount of energy left for all the mobile nodes during the packets transmission from the source to destination.
It is defined as the average delay in variance for the packets to reach from the source to the destination.
Figure 7(a) indicates Average Throughput with a variation of mobility on network size 20 using TCP agent. Figure 7(b) indicates Average Throughput with a variation of mobility on network size 20 using UDP agent.
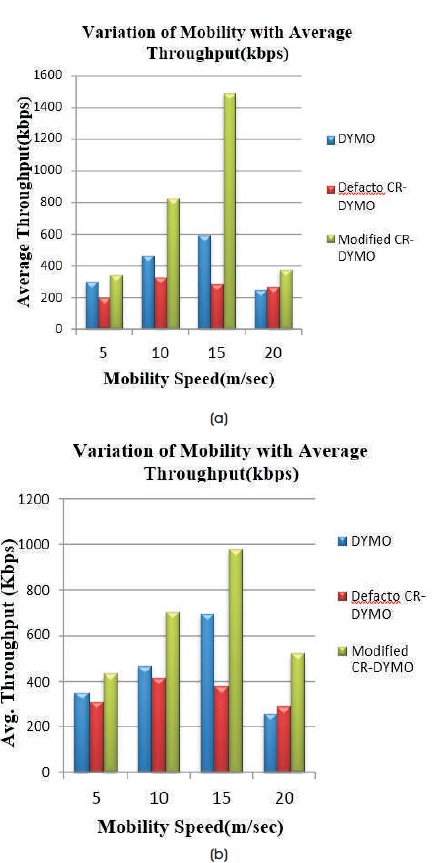
Figure 7. (a) TCP (b) UDP
Average throughput increases as the mobility speed increases and reaches the highest value at 15 m/s and ATP is decreased at the mobility speed 20 m/s since the mobility speed causes the link breaks and route changes happen regularly so the throughput decreases in case of TCP as well as UDP. From the graph, it is observed that at all mobility speeds Modified CR-DYMO routing protocol achieves the highest value of ATP when compared to DYMO and Defacto CR-DYMO routing protocols for TCP as well as UDP.
At mobility speed 15 m/s, Average Throughput for DYMO with TCP is 595 kbps and incorporating defacto CR-DYMO, ATP decreases to 286 kbps and after modifying CR-DYMO, ATP increases to 1494 kbps. In case of UDP for DYMO, at mobility speed 15 m/s, Average Throughput is 697 kbps and ATP for proposed defacto CR-DYMO decreases to 381 kbps and after changing CR-DYMO, ATP increases to 980 kbps.
Figure 8(a) shows Packet Delivery Ratio with a variation of mobility on network size 20 using TCP agent. Figure 8(b) shows Packet Delivery Ratio with a variation of mobility on network size 20 using UDP agent.
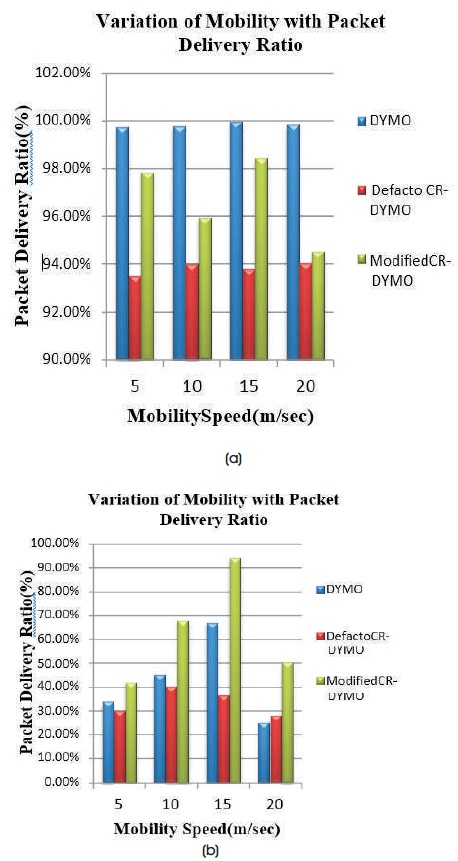
Figure 8. (a) TCP, (b) UDP
Packet Delivery Ratio is high with respect to TCP when compared to UDP at all mobility speeds. Since TCP is an assured delivery whereas UDP is a best-effort delivery. The PDR for DYMO is greater when compared to defacto CR-DYMO and Modified CR-DYMO with TCP agent. The PDR grows as the mobility speed increases and reaches the highest value at 15 m/s and PDR declines at the mobility speed 20 m/s since the mobility speed causes the connection breaks and path changes frequently so the PDR decreases in case of UDP. From the graph, it is conferred that at all mobility speeds Modified CR-DYMO routing protocol attains the maximum value of PDR when compared to DYMO and defacto CR-DYMO routing protocols for UDP.
In the case of UDP for DYMO, at Mobility speed, 15 m/s, PDR for traditional DYMO is 67.08% and PDR for defacto CR-DYMO decreases to 36.7% and after configuring CR-DYMO, PDR increases to 94.33%.
Figure 9(a) indicates Average End-to-End Delay with a variation of mobility on network size 20 using TCP agent. Figure 9(b) indicates Average End-to-End Delay with a variation of mobility on network size 20 using UDP agent.
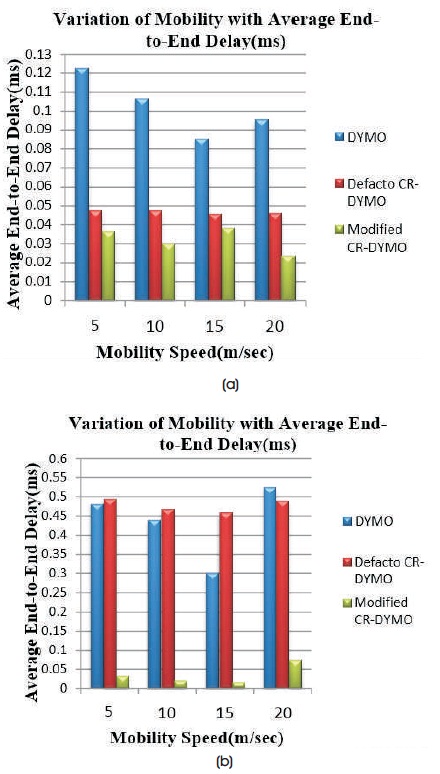
Figure 9. (a) TCP, (b) UDP
Average End-to-End Delay is high in case of UDP when compared to TCP at all mobility speeds. The AEED for DYMO is higher when compared to Defacto CR-DYMO and Modified CR- DYMO with TCP agent. From the graph, it is observed that at all mobility speeds, Modified CR- DYMO routing protocol achieves the lower AEED when compared to DYMO and defacto CR-DYMO routing protocols for TCP as well as UDP.
For DYMO with TCP, at mobility speed 15 m/s, AEED is 0.085 ms and including defacto CR-DYMO, AEED decreases to 0.046 ms and subsequently altering CR-DYMO, AEED further decreases to 0.038 ms. With UDP for DYMO, at mobility speed 15 m/s, AEED is 0.03 ms and AEED for proposed defacto CR-DYMO increases to 0.45 ms and after modifying CR-DYMO, AEED decreases to 0.015 ms.
Figure 10(a) shows Routing overhead with a variation of mobility on network size 20 using TCP agent. Figure 10(b) shows Routing overhead with a variation of mobility on network size 20 using UDP agent.
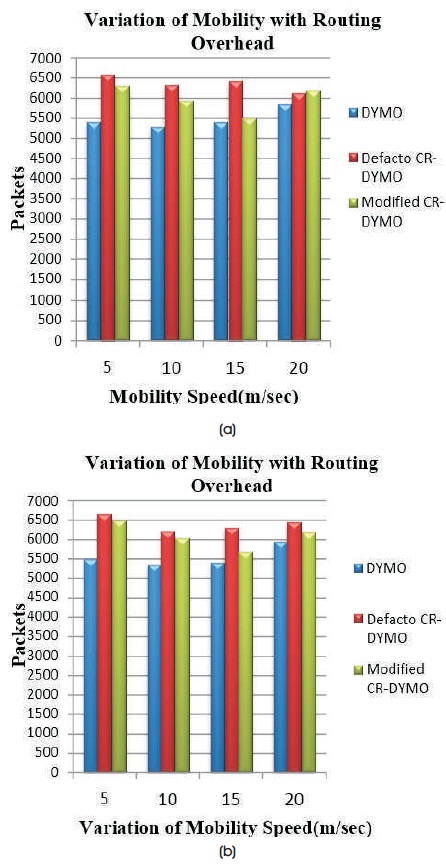
Figure 10. (a) TCP, (b) UDP
From the graph, it is observed that Routing Overhead is higher for defacto CR-DYMO and Modified CR-DYMO when compared to DYMO and Modified CR-DYMO has slightly lower Routing overhead when compared with defacto CR-DYMO for TCP and UDP at all mobility speeds except at 20 m/s in TCP due to the addition of cognitive radio capabilities.
With TCP for DYMO, at mobility speed 15 m/s, RO is 5401 packets and incorporating defacto CR-DYMO RO increases to 6435 packets and later altering CR-DYMO RO decreases to 5506 packets. With UDP for DYMO, at Mobility speed 15 m/s, RO is 5399 packets and RO for designed defacto CR-DYMO increases to 6307 packets and next changing CR-DYMO, RO decreases to 5694 packets.
Figure 11(a) indicates Normalized Routing Load with variation of mobility on network size 20 using TCP agent. Figure 11(b) indicates Normalized Routing Load with variation of mobility on network size 20 using UDP agent.
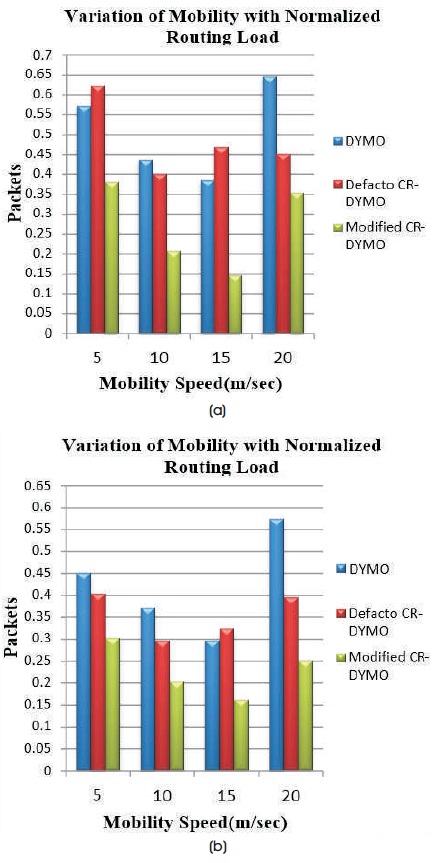
Figure 11. (a) TCP, (b) UDP
From the graphs, it is observed that Normalized Routing Load is high in case of TCP when compared to UDP at all mobility speeds. The NRL for Modified CR-DYMO is lower when compared to DYMO and Defacto CR-DYMO with TCP and UDP agent at all mobility speeds. NRL is high at the mobility speed 20 m/s in TCP as well as UDP as more number of control packets is required when the mobility is high due to link breaks and route changes.
For DYMO with TCP, at Mobility speed 15 m/s, NRL is 0.38 and NRL for proposed defacto CR-DYMO increases to 0.47 and after altering CR-DYMO NRL decreases to 0.14. At mobility speed 15 m/s, for DYMO with UDP agent, NRL is 0.29 and including defacto CR- DYMO, NRL increases to 0.32 and after modifying CR-DYMO, NRL decreases to 0.16.
Figure 12(a) shows Energy consumed with variation of mobility on network size 20 using TCP agent. Figure 12(b) shows Energy Consumed with variation of mobility on network size 20 using UDP agent.
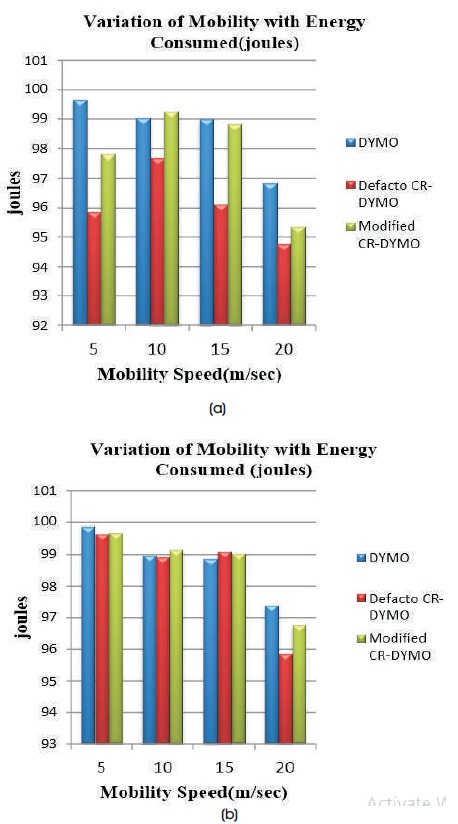
Figure 12. (a) TCP, (b) UDP
From the graphs, it is observed that Energy consumed is high in case of TCP and UDP except for the mobility speed of 20 m/s. The Energy consumed is higher in DYMO and Modified CR-DYMO when compared to defacto CR-DYMO in TCP and Modified CR-DYMO has less Energy consumed when compared to DYMO.
For DYMO with TCP, at mobility speed 20 m/s, Energy consumed is 96.84 joules and including defacto, CR-DYMO Energy consumed decreases to 94.79 joules and after altering CR-DYMO Energy consumed slightly increases to 95.34 joules. With UDP for DYMO, at mobility speed 20 m/s, Energy consumed is 97.39 joules and designed defacto CR-DYMO Energy consumed decreases to 95.86 joules and after changing CR-DYMO Energy consumed slightly increases to 96.75 joules.
Figure 13(a) indicates Energy Left with a variation of mobility on network size 20 using TCP agent. Figure 13(b) indicates Energy Left with a variation of mobility on network size 20 using UDP agent.
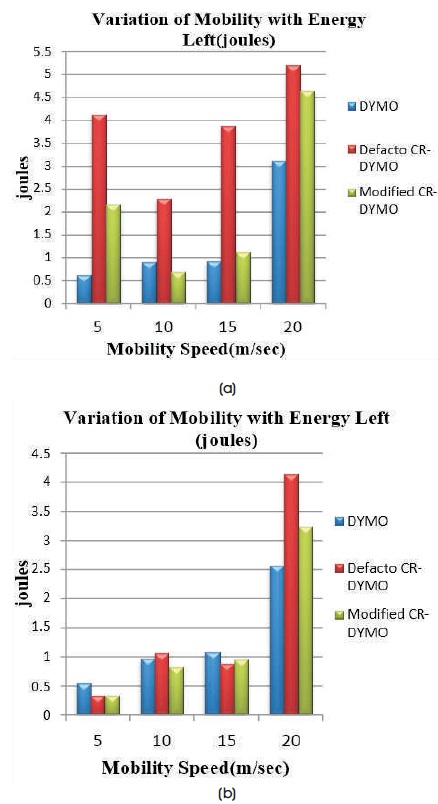
Figure 13. (a) TCP, (b) UDP
From the graphs, it is observed that Energy Left is high in TCP and UDP at the mobility speed 20 m/s. The Energy left is higher in defacto CR-DYMO when compared to DYMO and Modified CR-DYMO in TCP. Also, Energy Left increases as the mobility speed increases and achieves highest at the 20 m/s in UDP.
At mobility speed 20 m/s, for DYMO with TCP, Energy left is 3.12 joules and Energy left for designed defacto CR-DYMO increases to 5.2 joules and after modifying CR-DYMO Energy left slightly decreases to 4.65 joules. In case of UDP for DYMO, at Mobility speed, 20 m/s, Energy left is 2.56 joules and Energy left for designed defacto CR-DYMO increases to 4.13 joules and after modifying CR-DYMO Energy left slightly decreases to 3.23 joules.
Figure 14(a) shows Mean Jitter with a variation of mobility on network size 20 using TCP agent. Figure 14(b) shows Mean Jitter with a variation of mobility on network size 20 using UDP agent.
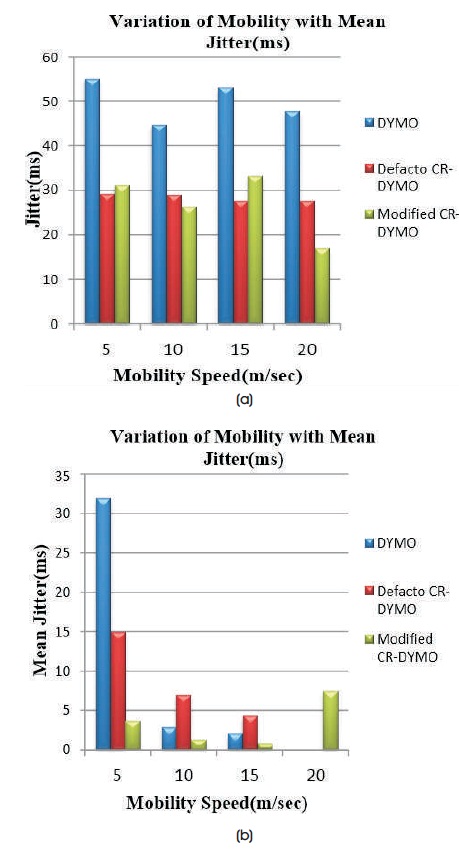
Figure 14. (a) TCP, (b) UDP
From the graphs, it is observed that Mean Jitter is high in case of TCP when compared to UDP at all mobility speeds. The Mean Jitter for DYMO is higher when compared to Defacto CR-DYMO and Modified CR-DYMO with TCP agent at all mobility speeds. Mean Jitter is lower at all mobility speeds except at 5 m/s in case of UDP.
For DYMO with TCP, at Mobility speed 20 m/s, MJ is 47.74 ms and incorporating defacto CR-DYMO MJ decreases to 27.58 ms and after changing CR-DYMO, MJ decreases to 16.99 ms.
Cognitive radio networks are the most promising technology for the effective utilization of spectrum in wireless networks. Among many research areas in CRAHN, routing is a challenging issue. In this paper, CR-DYMO routing protocol for MANETs incorporating cognitive abilities is proposed using CogNS simulation framework. The simulations are carried out and evaluated using the various performance metrics in Table 3. Average Throughput, Packet Delivery Ratio, Average End-to-End Delay, Routing overhead, Normalized Routing Load, Mean Jitter, Energy Consumed, and Energy Left through responsive (TCP) and non-responsive (UDP) traffic agents for FTP and CBR application traffics, respectively were studied. The table shows the results obtained at mobility speeds for optimum performance metrics in original DYMO, proposed defacto CR-DYMO, and Modified CR-DYMO.
The experimental results clearly indicate that Modified CR-DYMO routing protocol outperforms when compared to DYMO and defacto CR-DYMO with respect to the mentioned performance metrics under FTP and CBR traffic. The simulation results are statistically validated using ANOVA tool. Enhancing the QoS of DYMO routing protocol is a time series problem which can be also solved using Soft computing techniques. The work can be extended further with other routing protocols considering different traffic agents and physical layer settings.