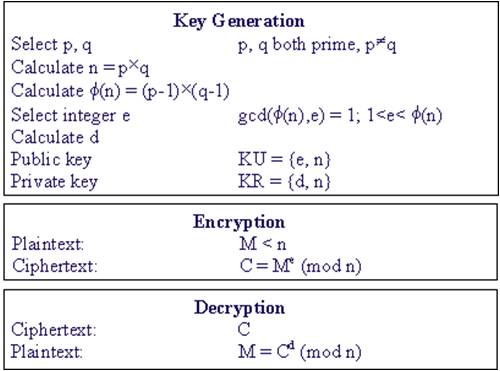
Figure 1. The RSA algorithm
The RSA system is widely employed in networking applications for good performance and high security. It supports the multiple key sizes like 128 bits, 256 bits, 512 bits. In this paper, The authors use Verilog code to implement a 16-bit RSA block cipher system. Therefore it can easily be fit into the different systems requiring different levels of security. The whole implementation includes three parts: key generation, encryption and decryption process. The key generation stage aims to generate a pair of public key and private key, and then the private key will be distributed to receiver according to certain key distribution schemes. The memory usage and overhead associated with the key generation is eliminated by the proposed system model. The cipher text can be decrypted at receiver side by RSA secret key. Verilog code is synthesized and simulated using Xilinx-ISE 12.1. It is verified that this architecture supports for multiple key of 128bits, 256bits, and 512 bits. Net list generated from RTL Compiler will be used to generate the IC layout. In this work, they have also developed an algorithm using LabVIEW 2010. LabVIEW (Laboratory Virtual Instrument Engineering Workbench) is a graphical programming language that uses icons instead of lines of text to create programs. Unlike text based programming language, LabVIEW uses the data flow programming, where the flow of data determines the execution. The flexibility, modular nature and ease to use programming is possible with LabVIEW, making it less complex.
Cryptography plays an important role in the security of data. It enables us to store the sensitive information or to transmit it across the insecure networks so that unauthorized persons cannot read it. The urgency for secure exchange of digital data resulted in large quantities of different encryption algorithms which can be classified into two groups: symmetric key algorithms (with private key algorithms) and asymmetric key algorithms (with public key algorithms) [1]. The asymmetric key algorithm requires two different keys, one for encryption and other for Decryption. The most common public key algorithm is RSA, named for its inventors Rivest, Shamir, and Adleman (RSA). The RSA algorithm is a secure, high quality, public key algorithm [2]. It can be used as a method of exchanging secret information such as keys and producing digital signatures.
However, the RSA algorithm is very computationally intensive, operating on very large (typically thousands of bits long) integers. It uses two numbers, e and d, as the public and private keys, and the two keys e and d have a special relationship to each other [7]. This paper describes the implementation of RSA encryption/decryption algorithm on FPGA using 128 bits key size.
The RSA algorithm was invented by Rivest, Shamir, and Adleman in 1977 and published in 1978. It is one of the simplest and most widely used public-key cryptosystems. Figure 1 summarizes the RSA algorithm.
The system architecture for key generation is shown in Figure 2. A random number generator generates 512-bit pseudo random numbers and stores them in the rand FIFO. Once the FIFO is full, the random number generator stops working until a random number is pulled out by the primality tester. The primality tester takes a random number as input and tests if it is a prime. Confirmed primes are put in the prime FIFO. Similarly to the random number generator, primality tester starts new test only when prime FIFO is not full. A lot of power is saved by using the two FIFOs because computation is performed only when needed. When new key pair is required, the downstream component pulls out two primes from the prime FIFO, and calculates n and Ф(n). n is stored in a register. Ф(n) is sent to the Greatest Common Divider (GCD), where public exponent e is selected such that gcd ( Ф(n), e) = 1, and private exponent d is obtained by inverting e modulo (n). e and d are also stored in registers.
Once n, d, and e are generated, RSA encryption/ decryption is simply a modular exponentiation operation. Figure 3 shows the RSA encryption/decryption structure in hardware implementation.

Figure 1. The RSA algorithm
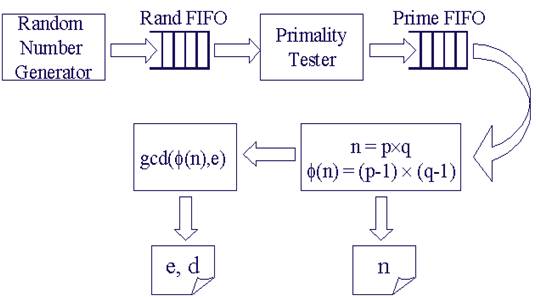
Figure 2. The System Architecture for RSA key generation
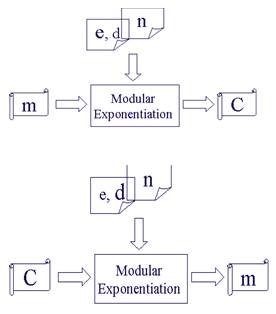
Figure 3. The RSA encryption/decryption structure
Anyone who needs to send a message to Bob can use n and e. For example, if Alice needs to send a message to Bob, she can change the message, usually a short one, to an integer. This is the plaintext. She then calculates the cipher text, using e and n.
C= Pe(mod n)
Alice sends C, the cipher text, to Bob.
Bob keeps φ and d private. When he receives the cipher text, he uses his private key d to decrypt the message:
P= Cd (mod n)
For RSA to work, the value of P must be less than the value of n. If P is a large number, the plaintext needs to be divided into blocks to make P less than n.
Choose p = 3 and q = 11
Compute n = p * q = 3 * 11 = 33
Compute φ(n) = (p - 1) * (q - 1) = 2 * 10 = 20
Choose e such that 1 < e < φ(n) and e and n are coprime.
Let e = 7
Compute a value for d such that (d * e) % φ (n) = 1.
One solution is d = 3 [(3 * 7) % 20 = 1]
Public key is (e, n) => (7, 33)
Private key is (d, n) => (3, 33)
The encryption of m = 2 is c = 27 % 33 = 29
The decryption of c = 29 is m = 293 % 33 = 2
[7]. This paper describes the implementation of RSA encryption/decryption algorithm on FPGA using 128 bits key size.