Figure 1. History of Cloud Computing
Cloud computing has gained momentum and people are now migrating their data to the cloud as data is growing in size and requires access from a variety of devices. Therefore, Cloud-based data storage has become the standard. However, there are several concerns about data storage in the cloud, starting with virtual machines, which are used to share resources in the cloud, resulting in cloud storage issues. This study identifies cloud data storage concerns such as data storage, data backup, data privacy and integrity, data recoverability, and cloud data recycling. Finally, we provide possible cloud-based solutions to the above-mentioned issues.
The cloud computing age started in 1960s and is continuing throughout the twenty-first century. Amazon launched AWS (Amazon Web Services) in the mid-2000s, perhaps around 2006, and also announced its Elastic Computing Cloud (EC2). By 2008, Google had released a beta version of its search engine as well. Microsoft Azure, a cloud computing service for testing, deployment, and management of applications and services, was first launched by Microsoft in 2008. Google compute engine was first introduced in 2012, but by the end of December 2013, it had been handed out to the general public. Oracle launched Oracle Cloud, which includes three main business services (IaaS, PaaS and SaaS). According to records, Linux and Microsoft Azure now share the majority in parallel. Figure 1 shows the evolution of Cloud Computing.
Cloud computing is the delivery of various services through the Internet. These resources include tools and applications such as data storage, servers, databases, networking and software, among other things.
Figure 2 describes the working principles of cloud computing. There are a variety of reasons why cloud computing is becoming more popular among individuals and organisations, including cost savings, enhanced productivity, speed and efficiency, performance and security.
Cloud computing may be used in both public and private environments. Public cloud services are those that supply their services via the Internet in exchange for a charge. Private cloud services, on the other hand, are limited in their ability to serve a certain number of individuals. These services are comprised of a network of networks that provide hosted services. There is also a hybrid option, which incorporates components of both public and private services in a single package.
The fundamental cloud computing architectural framework is described in this section, as seen in Figure 3. To understand security challenges, it is necessary to first understand the basic concepts and cloud computing framework. The National Institute of Standards and Technology (NIST) has three service models, and four deployment models.
This cloud model is composed of five essential characteristics:
On-demand self-ser vice: Consumers may help themselves by deciding which services to subscribe and how much to invest, all with a credit card swipe or an online payment system. An IT department may buy extra resources on demand to handle unexpected increases in user traffic.
Broad network access: Resources hosted on a private cloud network (operated inside a company's firewall) that are accessible from a wide variety of devices, such as tablets, PCs, Macs, and smartphones, are referred to as "broad network access." These resources may also be accessed by different places through internet.
Resource Pooling: When cloud providers provide provisional and scalable services to a large number of clients or customers, this is referred to as resource pooling. In other words, space and resources are pooled to service a large number of customers at the same time. Depending on how much a client consumes in terms of resources, usage may be configured to deliver more or less at any moment.
Rapid Elasticity: Rapid elasticity is a cloud computing concept that refers to scalable provisioning, or the capacity to deliver scalable services. Rapid elasticity enables customers to request additional cloud storage space or other types of services on an as-needed basis without having to do anything manually. Provisioning may be smooth for the client or user due to the deployment of cloud computing services, which makes it easier to manage. The fact that service providers must still allocate and de-allocate resources is frequently insignificant from the perspective of the client or user. This is a very important feature of cloud computing technology.
Measured Service: Measured Service Cloud systems automate the management and optimization of resource use by taking advantage of the capacity to metre at a level of abstraction suitable for the kind of service being provided (e.g., storage, processing, bandwidth, and active user accounts). Resource consumption may be tracked, regulated, and reported, ensuring transparency for both the service provider and the end-user of the service.
Figure 4 shows the cloud deployment models which may be classified into many varieties, with each form being distinct from the others.
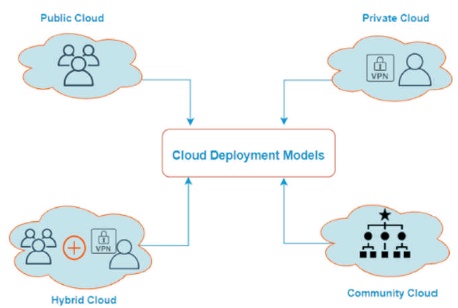
Figure 4. Cloud Deployment Model
The most common cloud computing services are described in Figure 5. Infrastructure As A Service (IAAS), Platform As A Service (PAAS), and Software As A Service (SAAS). These are many degrees of abstraction that cloud services offer.
This is the most fundamental abstraction. In these types of services, the user is given the option of selecting the underlying infrastructure, such as the operating system, the RAM and memory configuration, the quantity of memory, and the type of antivirus. This enables users to configure their own virtual computer on a pay-as-you-go basis. This implies the user will only pay for the resources he or she consumes. Amazon Web Service, Microsoft Azure, and Google Compute Engine are just a few examples.
Software-as-a-Service is the one in which everything is handled by a cloud service provider. The user just has to connect to the programme over the Internet. The cloud provider hosts the application's data centre, and the user subscribes to it. The user does not need to bother about updates or hardware compatibility. He/she just needs an internet connection in order to utilise it. For instance, Google Apps, WebEx, and Salesforce.
Platform as a service is a term that refers to a cloud service in which a user has no botheration regarding the underlying infrastructure but may have a variety of web and mobile applications supported by the cloud. It functions similar to a framework onto which programmes may be built. It streamlines the creation, testing, and deployment of applications.
Cloud security is a collection of rules, controls, procedures, and technologies designed to protect cloud-based systems, data and infrastructure. Cloud computing, is the delivery of information technology services through the internet. These security measures are designed to protect cloud data, ensure regulatory compliance, safeguard the privacy of consumers, as well as to establish authentication criteria for particular users and devices.
Cloud provider is an organisation that delivers cloud-based IT resources, responsible for making cloud services accessible to cloud users, as per agreements upon SLA guarantees.
Organisation that has a formal contract or agreement with a cloud provider to utilise IT resources made available by the cloud provider is a Cloud Consumer. Cloud service consumer access a cloud provider. Figure 6 shows how a cloud consumer (Organization A) interacts with a cloud provider's service (that owns Cloud A). The cloud service consumer is utilised by Organization A to access the cloud service.
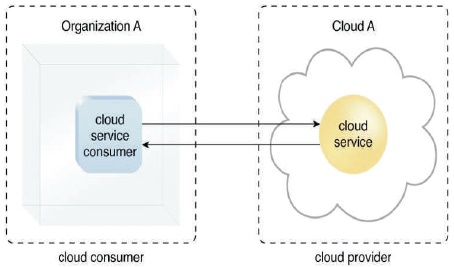
Figure 6. Interaction between and Cloud Provider (Erl et al., 2013) Cloud Consumer
The person/organisation that legally owns a cloud service is termed a cloud service owner. The cloud service owner might be a cloud customer, or the cloud provider that owns the cloud inside on which the cloud service sits. A cloud customer that owns a cloud service hosted by a third-party cloud does not necessarily need to be the user of the cloud service. A cloud service owner is not a cloud resource owner. Figure 7 illustrates that when a cloud consumer launches its own service in the cloud, it becomes a cloud service.
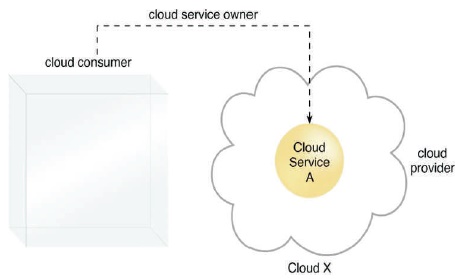
Figure 7. Cloud Consumer as Cloud Service Owner (Erl et al., 2013)
A cloud service administrator is the person or organisation responsible for managing a cloud-based IT resource (including IT services). The cloud consumer or cloud provider, or even third-party entity might be a cloud resource administrator. A cloud resource administrator may work for a cloud consumer organisation and manage the cloud consumer's remotely available IT resources, as shown in Figure 8.
Figure 8. Functions of Cloud Resource Administrator (Erl et al., 2013)
Physical limits that surrounds a collection of IT resources that are owned and regulated by an organisation, is the Organisation Boundary.
Trust Boundary is the logical boundary that generally stretches beyond physical limits to show the degree to which IT resources are trusted.
Common roles linked with cloud-based engagement and interactions include the cloud provider, cloud consumer, cloud service owner, and cloud resource administrator.
Cloud computing requires the uploading of a massive volume of data to a cloud computing centre. Users are increasingly worried about privacy security as a result of the loss of complete control over resources (Islam et al., 2015). Due to the complexity and real-time nature of cloud computing service models, the multi-source heterogeneity and perception of data, as well as the limited resources available to terminals, traditional data security and privacy protection mechanisms are insufficient to protect the massive data generated by cloud computing (Mollah et al., 2017).
Ali et al. (2015) provides a brief overview of cloud architecture and current security problems. The author focuses mostly on contemporary cloud security concerns. The report discusses a variety of security concerns, including communication security, architectural security, compliance and legal security. However, in this work, authors identified just three distinct categories of cloud security concerns. Additionally, this paper discusses how to enable secure authentication, authorisation, and integrity in online services. Additionally, the paper examines the security concerns associated with mobile cloud computing, and also various unresolved issues.
Zhou et al. (2010) provides an in-depth examination of cloud security and privacy for cloud service providers. The author defines the terms "security" and "privacy" independently. To begin with security terms such as confidentiality, integrity, access control, availability, and auditing characteristics, and commonly utilised privacy methodologies are discussed. Additionally, the study presents a solution to the problem of multi-location storage servers.
Takabi et al. (2010) discusses various cloud security issues, including data and application outsourcing, resource sharing, virtualization and hypervisors, heterogeneity, authentication and authorization, access control and identity management, trust and secure service management and data storage security and privacy. However, the authors could not provide a solution.
Rong et al. (2013) analysed all aspects of cloud computing security. The authors' main objective is to describe cloud computing and the associated cloud security challenges. However, this paper's primary drawback is that it does not address cloud security vulnerabilities. Additionally, the authors are not concerned with the open concerns that exist in the cloud environment.
Pearce et al. (2013) does a thorough analysis of virtualization security issues in a platform-independent way. The authors begin by discussing the fundamentals of cloud virtualization and then demonstrate a liberal framework for cloud system virtualization. The paper explored secure system isolation and analysed the challenges that develop as a result of strong virtualization qualities and a lack of core virtualization implementation.
Vaquero et al. (2011) discussed challenges relating to IaaS's three primary categories - virtualization, networking and physical infrastructure. They analysed risks related with these three domains and associated solutions presented in various publications and concluded that access control and encryption methods are the primary levers for assuring the overall security of infrastructure components.
Xiao and Xiao (2012) reviewed five security and privacy features (confidentiality, privacy protection, integrity, availability, and accountability), as well as security vulnerabilities, threat models, and defensive techniques, but did not provide a precise performance comparison description.
This section mainly focuses on several different security challenges and their solutions. Attacks, configuration issues, faults, damage, loopholes, and weaknesses in the system are all examples of security issues. There is a significant distinction between a cloud-specific problem and a generic one. The cloud-related problem arises as a result of the NIST-defined features of cloud computing, which make it far more difficult to deploy security solutions in a cloud context.
Cloud data storage is a cloud computing model in which data is stored on the Internet and managed and operated by a cloud computing provider. It's on-demand, with just-intime capacity and pricing, and it saves money by not having to acquire and manage own data storage infrastructure.
Data is a vital part of cloud computing. Customers cannot access data stored in the cloud, since it is isolated and incomprehensible.
The biggest issue with remote storage or third-party storage is that the consumer has no idea what happens to their data once it is stored in the cloud. The data owner is unaware of the location of the cloud storage facility, as well as the security services and processes employed to protect cloud data.
The importance of service quality in cloud storage cannot be overstated. To store data in the cloud effectively and reliably, a cloud storage provider requires the right approach and procedures. Two circumstances occur before and after data computation.
There are various cloud data storage issues in cloud computing
Loss of control over data is a fundamental concern in the cloud computing model since it does not allow complete control over the data and makes it more difficult to ensure data integrity and confidentiality. Cloud computing users are physically separated from their data, storage, and computing server. A server pool is provided by cloud computing for storing cloud data. The server pool's location is unknown; however, it is under the ownership and management of the cloud service provider. The virtual layer's abstraction makes it more difficult to locate the storage server's physical location. The user data is stored in cloud data centres. The data is extremely redundant and is kept in many locations. Cloud space may be effectively utilised with the use of an appropriate space allocation system. Data redundancy is a technique for backing up data to another cloud server to ensure data availability. In the case that one of the data centres fails, the supplier will use a backup data server. Various data servers are used by Google and Amazon in different regions. These organisations store their data using a multi-location feature, which might introduce additional security risks and legal issues since data kept throughout the globe are subject to various rules.
Another important issue in cloud computing is cloud data backup, which is a relatively new concept. It is necessary to have a frequent data backup procedure in place to guarantee that data is always available. When a data backup method is performed on the service provider's end, it ensures that data can be recovered in the event of a natural or accidental disaster. The most prevalent dangers, such as illegal access and data tampering, have the potential to destroy backup storage. As a result, when it comes to data backup, this sort of hazard is taken into consideration.
Cloud computing offers the advantages of resource pooling and elasticity. This feature gives the cloud the ability to allocate dynamic and on-demand resources to the user who has requested them. Data recovery and confidentiality may be undermined by this feature. The resources that are provided to a requested user may be assigned to another user at a later time if the requested user does not accept the resources that were granted to him. The malicious user may be able to access the data recovery mechanism and get the previous user's data. This has the potential to have several serious effects for sensitive user data.
Even though cloud computing is less expensive and requires less resource management, it poses significant security risks. Because of its simplicity, cloud users are growing at an exponential rate, and the number of applications hosted in the cloud is expanding rapidly. As a result of these circumstances, cloud customers are exposed to additional security risks. If an attack on a data entity is successful, it will result in a data breach, which will allow unauthorised access to the data of all cloud customers. As a result of this integrity breach, cloud data loses its multi-tenant capability. Particularly SaaS providers, who may also lose their technical data, face a significant risk of data loss due to data storage. Additionally, data processing is a great risk when data is being converted across various tenants, in addition to these hazards. The use of virtualisation allows numerous physical resources to be shared across a large number of people. As a result, malicious insiders initiate attacks against the Customer Service Provider (CSP) and/or organisation. These circumstances may provide an opportunity for a malicious user to launch attacks on stored data of other customers while processing their data. When a CSP outsources data storage to a third-party storage facility, there is an additional significant risk. The key generation and key management processes in cryptography for cloud computing are not yet fully standardised to meet industry requirements. However, the absence of a standard and safe key management system for the cloud prevents the typical cryptography methods from performing effectively in a general cloud computing architecture. As a result, cryptography may also help to mitigate the hazards associated with cloud computing.
An insider threat may be posed by workers, contractors and /or third party business partners of a company. In cloud environment i.e., at Cloud Service Provider (CSP) side threats leads to loss of user's information integrity, confidentiality, and security. This leads to information loss or breaches in both environments. This attack is valuable and it is widely known to most of the organisations. There is variety of attack methods done by insiders because of sophistication regarding internal structure of a organisation’s data storage structure. Most companies ignore this attack because it is very hard to defend and difficult to discover the complete solution for this attack. This attack results in high danger in terms of data breaches and lost confidentiality at both organisation and cloud levels.
Attacks that originate from external sources are termed outsider attacks. Data security is one of the main concerns in cloud computing, since service providers do not have authority for access to the physical security system of data centres. But they must depend on the infrastructure provider to obtain complete data security. In a virtual private cloud environment, the service provider can only define the security setting remotely, and we do not know exactly those are properly applied. In this process, the infrastructure provider must achieve the following objectives:
Once the data had been correctly utilised and transferred to trash, it is a good decision to reuse the cloud space. However, it must be assured that the prior user's data is not exposed to the following user. Sanitization is the process of cleansing or deleting a specific piece of data from a resource. After the data has been sanitised, it is made accessible to others in a distributed way. In order to correctly dispose of data and pick the data that is delivered to the trash, data sanitization is a key activity in the distributed system. Because the hard drive may be erasing some vital data, incorrect sanitization leads in data leakage and data loss.
Malware is intrusive software that is designed to damage and destroy computers and computer systems. Malware is a contraction for “malicious software.” Examples of common malware includes viruses, worms, Trojan viruses, spyware, adware, and ransomware.
The key difficulty behind this is, if one system contains malware then due to inheritance, the malware gets spread across the cloud. Additionally, malware is very harmful to cloud devices since it may be able to remove or damage the cloud data. Incase for protection of such sort of devices, we assign antivirus agents, when the malware enters in the system, first antivirus agents compare the malware signature and by chance if the signature is matched data is damaged or deleted. But probability of such thing occuring is very low. If the agent discovers such virus first time, it is good, else undoubtedly the malware may generate more serious trouble. So a monitoring system is required that can identify and reveal such viruses. Malware spreads to all the files which are synchronised with the files attached to it. The malware even when cleansed by anti-virus at the end-point of agent software clings to the device in cloud environment. So, there is great need to deal with dynamic malware.
Wei et al. (2014) introduced SecCloud, which is a storage security protocol for cloud customers' data that not only protects the stored data but also offers security on computational data. For secure data storage, the SecCloud protocol employs encryption. Key generation for cloud clients, CSPs, and other business partners or trusted third - party is done using multiplicative groups and cyclic additive pairing. The encrypted data is delivered to the cloud data centre, together with the verified signature and the session key. For both bilinear groups, the Diffie-Hellman method is employed to generate the session key. When the cloud receives encrypted data, it decrypts it, validates the digital signature, and saves the original data in a defined place in the cloud. The SecCloud validates whether or not data is saved at the given location. SecCloud protocol uses the Merkle hash tree for computation security. The verifying agency will validate the computational results generated by the Merkle hash tree.
In Tang et al. (2012) the File Assured Deletion (FADE) protocol allows key management while maintaining data integrity and privacy. The File Assured Deletion protocol (FADE) developed in (CSA, 2011) ensures key management as well as data integrity and privacy. FADE is a light-weight technique that employs both asymmetric and symmetric key data encryption. To foster confidence in key management, the Shamir system protects both symmetric and asymmetric keys. The FADE protocol employs a group of senior managers who serve as a trusted third party. The key k is used as an encryption key for the client's file F, while another key is used for data key encryption (k.). The policy file keeps track of which files are accessible. As a result, to upload data, the user must request the key pair from a third party by delivering policy file p. Using the policy file, the key management delivers public and private keys to the user. The upload file is encrypted using a randomly generated k, which is then encrypted with a symmetric key. That encrypted file is decrypted using the public key of the produced key pair, and a MAC is generated for integrity verification. The receiver will use the reverse method to recover the original data.
Tang et al. (2012) suggested a technique that uses timebased re-encryption with the ABE algorithm to provide secure data exchange among members of a group with access control. This technique guarantees that forwarded data reaches group users securely and that user revocation is maintained. In this approach, a time period is assigned to each user, and upon expiry, the Cloud Service Provider immediately revokes the licence (CSP). This timebased encryption approach enables users to exchange keys with CSP in advance, and CSP generates reencryption keys depending on the user's request. The ABE protocol guarantees access control by checking a collection of qualities rather than an individual's identification. This approach provides data privacy and availability among group members but does not focus on data integrity. Instead of reconstructing the whole tree from scratch, probabilistic sampling is employed to eliminate computational duplication. The Computer Security Alliances (CSA, 2011) have made many essential suggestions for data security and appropriate key management, which are included below. The key's scope should be maintained by the organisation or person. Standard encryption techniques should be utilised, whereas weak algorithms should be avoided. The finest standards for key management and encryption software products should be implemented; it is preferable to employ genuine software technologies to assure storage security. Effective key management should be maintained by the client, companies, and/or a trustworthy third party. If an ineffective auditing protocol is used, the encryption process may control the data flow to third parties during the auditing process. However, encryption does not block data transmission to other parties; rather, it might decrease it to a certain degree. However, it necessitates a wide variety of key management processes and overheads for key production while storing data. However, exposing the encryption key results in data leakage, which is still an issue in the cloud context. Combining the homomorphic authenticator with the random masking method solves this issue (Fu & Lin, 2013).
Previously discussed cloud security concerns allows understanding that the cloud has not just certain security difficulties, but a large number of security issues that may occur as a result of the adaptation of innovative cloud technologies.
Some classic difficulties that are present in the beginning of cloud computing are security issues connected to cloud communication, network, data privacy, application, and web services. Security difficulties that arise as a result of multi-tenancy, virtualization, and shared pool resources are examples of creative security concerns. Several services and resources are available in a cloud computing environment, however the security degree of the resources are determined by the sensitivity and value level of the resource. For example, cloud computing data security is increasingly critical, and it is harder to deal with such issues since the data owner loses control over the data when it is transferred/stored on the cloud.
Several studies have been conducted in order to overcome security issues in a cloud setting. However, there are several unresolved concerns that must be addressed in order to provide a secure cloud infrastructure. One of the most important open issue is the development of a comprehensive and integrated security solution capable of addressing all major security requirements in the cloud.
Each researcher focuses on a specific security problem and solves it in their own unique manner. The study and resolution of a given problem may result in several security solutions to a specific issue. Multiple security remedies for a single problem are not practical in a real-world setting. The use and configuration of various security systems may be hazardous in and of itself. A more integrated and common security solution is more safe and easier to apply in security tools.
Cloud computing offers the advantages of quick deployment, cost effectiveness, large storage capacity, and easy access to the system at any time and from any location. As a result, cloud computing is a very obvious and quickly emerging technology, and generally recognised computing environment all over the world. However, there are several security and privacy issues that are limiting cloud computing adoption. All cloud users should be wellversed in the vulnerabilities, threats, and attacks that exist in the cloud. The understanding of security dangers and attacks will assist organisations in implementing cloud adoption at a fast rate. Many classic as well as unique technologies are used in cloud computing. Many cloudspecific security vulnerabilities may arise as a result of these new technologies. The cloud's multi-tenancy and virtualization features allow users to access the same physical resources from several places. The lack of sufficient isolation between VMs can risk system security.
In this paper, we explored the fundamental characteristics of cloud computing as well as the security challenges and issues. This study identifies cloud data storage concerns such as data storage, data backup, data privacy and integrity, data recoverability and cloud data recycling. Finally, we discuss possible solutions for data storage and cloud-based solutions for the data storage concerns raised before.