Table 1. Comparison of Hash Algorithms
Voting is a democratic process to make a decision from among the available choices. Paper ballot is the most popular voting system in practice, though electronic voting machines are also gaining popularity. Both systems have integrity issues and security threats by manipulation of votes, voting by an imposter, rigging the ballot boxes, etc. are possible. The aim of this paper is to propose a concept to implement blockchain technology for a digital voting system by improving the security. The paper analyzed the existing voting practices, and finds a solution to use blockchain technology as this technology is evolving with better security measures. It also explains the implementation of existing digital voting systems and the problems faced by the developers. The detail of the proposed design is presented along with the potential flaws and threats in the design. The design concept uses SHA256 and RSA algorithms will be implemented through blockchain, with scope for improvement in future implementations.
Voting to elect the government is a process in any democratic country. Voting in an election is conducted by voters physically visiting the polling booths (Swamy, 2010). This process has several drawbacks like, lack of security and possibility of tampering the ballot boxes. It has been a challenge to convince legislators and people in building an electronic voting system for a long time. This paper proposes online voting system by implementing available and proven technologies. Using blockchain along with Distributed Ledger Technology (DLT) is one of the advancement in the information technology on replicating synchronized and shared digital data across geographical locations. Yavuz et al., (2018) mentioned that based on their trials immutable hash chains used in blockchan in improves the security of the casted vote in polls and elections.
Hao and Ryan (2016) presented various technologies and designs that can be implemented in any distributed electronic voting system. They also presented evaluations on blockchain technology for the design of electronic voting systems.
Cetinkaya and Cetinkaya (2007) discussed the requirements for the designing electronic voting systems and they define the legal and technological limitations on the use of blockchain as a service for the implementation of such systems. This paper also defined some common frameworks called as V & V frameworks (verification & validation frameworks) that have to be defined in designing e-voting system using blockchains. Wu (2017) used these concepts in designing the electronic voting system where blockchain technology was used along with ring signature algorithm.
Moloja and Mpekoa (2017) used d Cloud Intrusion Detection and Prevention System (CIDPS) to design a electronic system to be used through mobile phones. They used signature detection, anomaly based detection, and hybrid detection method to secure the system from any misuse. The study was successful in the simulation environment and needed o be tested in a real life situation to evaluate the performances of devices and network load.
Yi (2019) designed a secured e-voting system implemented on P2P network using blockchain technology. The system was designed by synchronized model of records based on DLT to prevent any fraudulent or forged votes. To authenticate the voter, the author used Elliptic Curve Cryptography (ECC). The study showed the possibility of practical implementation of the model on a large scale.
In a discussion in Hao and Ryan (2016), one vote is considered as a transaction. A peer to peer network is created as a private blockchain that used DLT for each vote. The application is designed in such a way so that the intricacies of the underlying architecture are hidden from the user.
In Yang et al. (2017), each voter is uniquely identified with a code. The application makes use this code to make sure that each voter gets only one chance to vote. When the vote gets submitted as a transaction, then all the peers in the network gets synchronized. Since each peer is associated with a public and private key, votes are encrypted, hashed, and added to the blockchain to enhance security and form the blockchain.
Voting is a very crucial part of any election to elect a government or decision making process by a group of people. It is the right of an individual and a power to exercise. Currently, various researches are being conducting in order to make secure and reliable electronic voting system, to tack issues of anonymity, fairness, reliability, and availability. Through the use of blockchain, the focus is on making the voting process fair and secured, without any third party intervention.
Privacy of a vote means, no other person should be able to tell how a voter voted. Even bulk statistics such as correlating vote with language should not be exposed. The only acceptable information disclosure is the final vote total for each precinct.
The voter should not be able to prove to anyone how they voted. Together with the privacy condition, this prevents selling a vote and coercion. If there is no way to assure a third party of which way a vote has been cast, bribes and threats are ineffective.
Each qualified voter should be able to vote exactly once and no other persons should be able to vote. The system must verify the identity of each potential voter and determine their status, but must not allow this information to become associated with their vote.
From the analysis of the previous works, we find that blockchain as a service has been implemented in many electronic voting (e-voting) systems. Further findings are listed below:
The need for a new system is arrived based on a few disadvantages found in the existing systems.
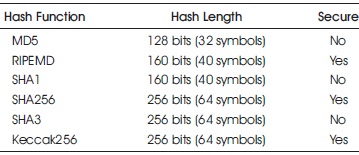
Hashing is the process of changing the arbitrary and variable size input to a fixed size output. There are different functions that perform hashing of different level. A few Hash functions and their basic properties are mentioned in Table 1.

Table 1. Comparison of Hash Algorithms
Race Integrity Primitive Evaluation Message Digest (RIPEMD) is a family of hash function developed by Hans Dobbertin in the year 1996. The algorithm was designed to be used as a cryptographic hashing algorithm, but it faces some problems that reduce the production of a unique hash value and hence it faces some vulnerability. MD5 is the latest in the MD2, MD3 and MD4 series.
The Message Digest 5 (MD5) algorithm is widely used for hashing purposes and provides a hash value of 128 bits or 32 characters. The algorithm was designed to be used as a cryptographic hashing algorithm but it faces some problems that reduce the production of unique hash value and hence it faces some vulnerability. Race Integrity Primitive Evaluation Message Digest (RIPEMD) is a family of hash function developed by Hans Dobbertin in 1996.
This was designed to overcome drawback in MD5 as a more secure alternative. It has few variations that have emerged over time including RIPEMD128, RIPEMD160, RIPEMD256, and RIPEMD320. SHA (Secure Hashing Algorithm) is another cryptographic hash function that yields 160 bit hash value consisting of 40 hexadecimal characters. The algorithm could not resist the collusion attacks against it and its usage has declined after 2005.
Several new algorithms have also been proposed, including SHA3, and SHA256. The SHA2 set of algorithms is designed by the US's Nation Security Agency. Among the new algorithms, SHA256 and SHA512 are functionally very secure. The flexibility of the algorithm, in contrast to its other counterparts, is that it accepts any length of input and yields an arbitrary length of output, while all other algorithms produce a fixed length output.
The system proposed system is based on the following technologies:
Permissioned blockchains is a layered additional blockchain security system. They maintain a layer of access control by allowing only certain identifiable participants to perform predefined actions. There are many benefits in the permissioned blockchains.
When we compared permissioned blockchains with public blockchains, they offer better performance. The reason behind is the limited number of nodes in the platform. Unnecessary computations required to reach consensus on the network are removed, improving the overall performance. Validation of each transaction is done using permissioned networks.
Permissioned networks do come with an appropriate structure of governance. This means that they are organized. Administrators require less time to update the rules over the network, which is considerably faster when compared to public blockchains. Blockchain network which is public, suffers from the consensus problem as not all nodes work together to get the new update implemented. These nodes might place their self-interest above the needs of the blockchain, which, in return, means slower updates to the whole network. In comparison, a permissioned blockchain has no problem as the nodes work together to move updates faster.
Proper use of blockchain is done in permissioned networks including utilizing its decentralized nature for data storage.
The architecture of the proposed system is shown in Figure 1. It consists of a registration module, a voting module and hashing phase.
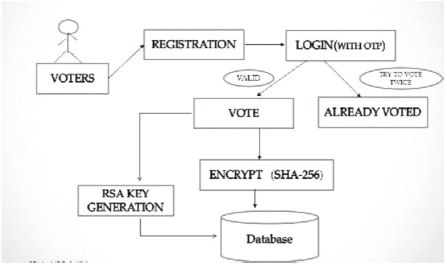
Figure 1. Proposed Architecture
To cast a vote, the voter has to follow the following steps.
In the Hashing phase, the algorithm used is SHA256 as it has better encryption and security. This algorithm has the following advantages:
SHA256 algorithm has been preferred for this project based on the following properties:
The proposed system is at its hypothetical stage. The SQL database is created as shown in Figure 2. Prototype development will be the next stage of the project where the effectiveness of the system will also be studied.
This paper reviewed some of the existing electronic voting systems that used blockchain technology. The proposal of a new system using the underlying concept of blockchain implementing security keys is the highlight of the proposed system. The system will be developed based on Internet technology, so that the voters will not need to election booths or stations, which will be a cost saving exercise for the large democracies.
Applications to cast a vote from cell phones will be considered as future scope of the project. There are two stages should have been considered to create them: Android and iOS. Appropriately, voters should download the casting a ballot application and use their cell phones, at that point they will most likely vote. It is substantially more helpful in light of the fact that at the present, the vast majority use cell phones.