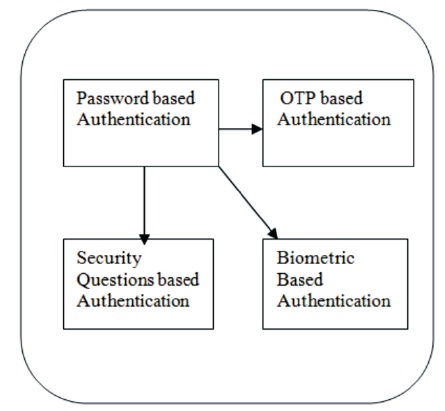
Figure 1. Framework of the Authentication Techniques
Cloud Computing is an advance technology that provides different services to the users on the rental basis. The main issue associated with the cloud is cyber attacks that are performed on the cloud services due to the improper security mechanisms especially authentication. In this paper, a multi level security using hybrid multifactor authentication methodologies based on the security questions, mobile OTP, and biometric authentication in addition to password based authentication to protect the data/services from the cyber attackers is proposed. The hybrid methodologies provides strong and secure authentication due to the two layer security. The biometric authentication includes face image as an authentication factor and the extraction of the face features are performed using VGG face model with the concept of transfer learning. The proposed work is implemented in the Google Colab cloud with python API and evaluated results show the proposed scheme providing privacy, confidentiality, integrity, and resistivity against the collision resistance attack, replay attack, tampering of the data, etc.
Cloud Storage is a prioritized service offered by the cloud providers to store vast amount of the data in the cloud database/cloud storage space. Cloud stores unlimited amount of user's data in the cloud database with the limited cost (Abu-Libdeh et al., 2010; Zeng et al., 2009). It offers scalability, rapid elasticity, on demand access features that attract users to utilize the services from anywhere, any time. Cloud services have much vulnerability that is exploited by the various outside attackers and inside attackers (Bowers et al., 2009). The most challenging issue faced by the storage cloud users is security and privacy (Feng et al., 2011). Nowadays most popular cloud service providers like Azure, Google, Amazon, Last Pass offers their 7services to the users (Rimal et al., 2009), on the basis of utility computing that attracts the users more flexible to utilize all these services. Some of the provided services are like Office 365, Gmail, Drop Box, storage services and these services are availed by the users based on the userID and password credentials are considered as default authentication mechanism. Recently, so many attacks were done on user's cloud database and stole their userID, hash passwords, and email's (ARN, 2020; Kim et al., 2014). Salck's data base, Last Pass are some cloud databases that faced the cyber attacks and have lost their user's information. To protect the data from the cyber attacks proper authentication, encryption mechanisms are required along with the firewall configuration rules, virtual private networks, and enabling the multifactor authentication.
Microsoft cloud experienced the breach that was by unauthorized users accessing their employee information. Microsoft claims that the customers has accessed the information and it was solved with-in two hours. Even single minute also makes severe loss of the organization.
In 2012 Drop Box announced the security attack against the file based sharing and also lots of userIDs, passwords, and emails hacked. Data is very important and the stolen data was made available to the dark web market place.
2016 cyber criminals performed attacks on LinkedIn users data. The cyber attackers stolen the users email addresses, and passwords. Nearly 167 million LinkedIn users emails and passwords were stolen and made available to the dark web market place.
Apple icloud users lost their photos due to the poor passwords. The Apple providers announced to their users to change the passwords with stronger passwords and introduced notification system if any malicious activity is initiated.
According to International Standard Organization (ISO) 7498-2, information security covers different concepts. The Cloud computing security should also suggest this way to become a secure and effective technology. The following are security mechanisms highlighted in the context of cloud computing (Dooley et al., 2018; Soni et al., 2016).
Enable the multifactor authentication methods to identify the users in addition to the userID and password. It made the alert system for notification to the users if any malicious activity is identified. The maintenance of the log file for the records of the unauthorized users that facilitate on how to improve the secure mechanisms against the cyber attacks.
Authorization decides what type of roles and permissions the user can perform and access in the services. Based on the type of subscription the administrator assigns the authorization permissions to the users for accessing cloud resources.
Cloud Developers needs to implement modern cryptography algorithms to provide the confidentiality of the data. The data must be encrypted before uploading into the cloud, at transit and at the rest.
The integrity requirement ensures whether the data which is stored in the cloud is modified. Traditional integrity mechanisms are not suitable for the cloud domain due to more computation. Special types of integrity mechanisms are required in cloud computing to preserve integrity.
Non-repudiation in cloud means the applications and services provided by cloud will not be changed by other cloud providers or users. Cloud computing uses the concepts like digital signatures, time stamps etc. for supporting non-repudiation.
Availability is one of the important requirements in the cloud. The data which is stored in the cloud must be available at all the time. Attacks on availability service are denial of service, distributed denial of service attack etc. The cloud provider needs to design proper security algorithms for preventing these attacks.
In this paper, a hybrid multifactor authentication algorithm based on combination of more than one methodology that is security questions, OTP, and biometric face verification as a second level authentication in addition to userID and password is proposed. In the security questions based authentication, the security question are defined by the user or randomly generated by the cloud service provider based on the user choice. The privacy preserving the security questions are performed by encrypting the security questions using public key of the user before uploading in to the cloud database. The answers of the questions are stored in the hash format. In the biometric authentication, cloud service provider captures user face image as an authentication factor. The extraction of the biometric features is performed using VGG face model.
Banayl et al. (2013) proposed multifactor authentication using encrypted value for the captcha as a user authentication factor. The strength of the scheme is based on the captcha.
Lee et al. (2010) proposed two factor authentications for accessing the cloud services based on the PKI, and mobile out of bound. The scheme provides the strong security but if the mobile device is stolen then the scheme is failed. Mashhadi (2015) proposed authentication in the mobile cloud computing based on the OTP password token. Biometric authentication techniques like finger print authentication, palm authentication, face-recognition are popular authentication techniques (Padma & Srinivasan, 2016; Pawle & Pawar, 2013, 2017). Devkota et al. (2015) proposed MIST authentication algorithm for the cloud users based on the custom security questions. The authors were not specified on how the answers and custom security questions are stored in the database.
Authentication is the process of identifying and validating the individuals for the access of the cloud services. Traditional authentication includes userID and password to verify the authenticity but due to modern hacking tools this type of the mechanism is not sufficient to identify the authorized users. Some cloud providers still uses userID, password as authentication method to identify the users of the cloud server. Recent cyber attacks on the cloud shows there is a need of multifactor authentication even for the simple SAAS services. Multifactor authentication that includes more than one factor of identifying the users are considered as mOTP, email OTP, text message, image captcha, security questions, etc., The proposed frame work includes four types of the authentication methodologies. The user may have the choice to choose any authentication technique in addition to password based authentication shown in the Figure 1.

Figure 1. Framework of the Authentication Techniques
The password based authentication is mandatory methodology for the other authentication techniques. If the user has made the request for accessing the services from the thin device, the user must prove them as an authenticated user by combing one of these authentication techniques along with the password based authentication. The proposed techniques are very simple to use with the flexible interface. The need of including multiple authentication methodologies are due to the following problems.
So, considering all these factors, the hybrid authentication methodology for the cloud user authentication is proposed. The password based authentication is the traditional authentication technique that requires the userID, and password chosen in the registration phase. The strong password rules are insisted to choose the secure password. The enforced rules of the password are combination of the alpha numerical characters with special symbols and minimum length is 8 characters. In the mobile OTP authentication technique, the double data type OTP is sent to the registered mobile. The user need to enter these value in the login form with in 3 minutes. For the security questions based authentication the user has an option to setup own security questions or predefined questions generated by the cloud service provider. The privacy of the security questions is achieved using the encryption algorithms and privacy of the answers is gained through hashing methodology. The biometric based authentication uses face image as an authentication factor. The extraction of the face image features are done using VGG deep learning model (Serengil, 2018). The necessary simulation parameters are listed in Table 1.
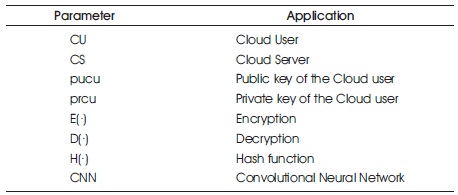
Table 1. Simulation Parameters
The CU who wants to avail the services from the cloud, he/she must be registered with the CS by providing all the required credentials for all types of authentication methodologies. In this phase, initially the user chooses the userID, and password and submits the mobile number, email id for the mobileOTP and emailOTP for the OTP based authentication. Next, the user setup the security questions by choosing the setup Questions option to enable the other type of the security. The user manually enters the security questions and the corresponding answers. The strength of the questions, i.e., strong or weak will be verified by the CS and it generates the message if the mentioned security questions are weak. The strong enforce rules of the security questions are defined by the CS. If the user entered question is not matching with these rules then there will alert message generated and it will not be accepted as security question. The CS verifies the strength of the questions and does not store any questions directly in the cloud database. If the questions strength is strong, then the questions are encrypted using the public key of the user and uploaded into the cloud database. The answers for the corresponding questions are converted into hash value using SHA-256 hash algorithm [] and the result hash value is uploaded into the cloud database. In this way, the privacy of the security questions and answers are preserved. The Figure 2 shows the security questions and answers setup in the cloud database.
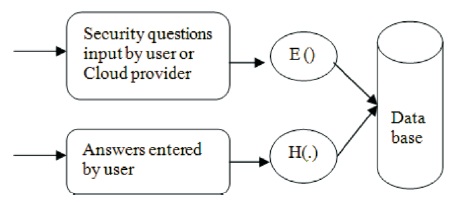
Figure 2. Security Questions Setup
The user submits face images and the application trains the image using the transfer learning technique by applying the VGG face model for the purpose of the biometric authentication. The procedures of the registration of the CU with the CS and the exchange of the credentials are performed in a secure environment described in the Algorithm 1.
Input: userID, Password, Security Questions, biometric factors, mobile no
Output: Registration Status
userID ← (userID)
password ← H (password∥salt)
mobileno ← (userenteredmobilenumber)
SQ [] ← (Questions setup by cloud user)
cloudDatabase ← E_pucu (SQ[])
AS[] ← H (answers)
cloudDatabase ← (SQ[])
cloudDatabase ← (AS[])
biometricfactors [] ← (images[])
train_VGG (faces)
The CU who wishes to avail the services from the CS must login and get authenticated. Initially, the CU submits the userID, and password. If the both credentials status is true, the CS generates second level authentication methodology which is chosen by the CU. If the authentication methodology is security questions based authentication, the CSP generates the encrypted questions to the CU. The CU decrypts the questions using their private key and enters the answers for the security question and then submitted to the CS. The CS applies the hash algorithm on answers and compares the generated hash value with the value available with the cloud server. If the both values are same then the CU is allowed for accessing the cloud services. Algorithm 2 describes the detail steps of the Login and Authentication using Security questions.
Input: UserID, Password, answers for the security questions
Output: Status of the user Authentication
userID←(userID)
password←(password)
CU←send(E_pucu (SQ))
Decrypt(D_prcu (SQ) )
AS[]←H(answers)
CS←send(AS[])
CS verify(AS[])
if equality holds
CU allowed for access the cloud service
else
Service denied
The strength of the security questions are based on the type questions and answers setup by the user and how easily it can be answered by the user themselves and not known to others.
To increase the strength of the scheme, the following rules will help to strengthen the methodology.
The strength of the methodology is based on how strongly defined are the security questions with the easy remembrance of the answers. But sometimes the user defines the questions which are easily answered by the others. The answers of the questions are shared by the user through the social websites leads to problems.
By using this information the hackers can easily login to our account within few minutes. Some of the weak security questions are shown in the Table 2.
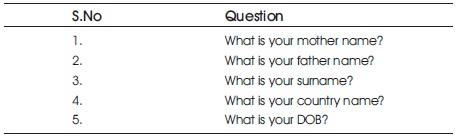
Table 2. Weak Security Questions
The mentioned questions are easily answerable questions by anyone who knows about the user. So, these type of questions are not allowed to be set as security questions.
In the OTP based authentication, the double type random number is sent to the registered mobile number and registered email. The user must provide two OTP's within the limited amount of the time. If the both OTP's are true then the user is allowed for accessing the services. The need of considering double type random value is typical for the attacker to identify.
In the absence of the mobile device or if forgot to answer the security questions, the CU may enable another technique for the authentication, i.e., using face verification technique. The captured biometric face image features are extracted using VGG CNN model. The process of the biometric face image is shown in the Figure 3.
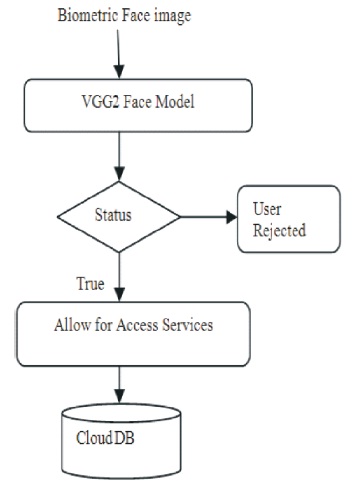
Figure 3. Biometric Face Authentication
The VGGFace2 model is created with pre-trained weights ResNet50 and the classifier is set as a false value, and pool layer type is maxpooling. The pooling layer converts the input features into reduced features by considering the maximum value. The Multi-Task Cascaded Convolutional Neural Network, or MTCNN, for face detection is used in this face detection to find and extract faces from the photos (Zhang et al., 2016). The face detection is identified using distance of the original image and the test image. The distance of these two vectors is calculated using Euclidean distance or cosine distance. Here, the cosine distance measure is applied to find the similarity of the two face images. Cosine distance is equal to one – cosine similarity. The measured threshold value is set by the provider. If the newly calculated cosine measure value is less than the predefined threshold value then the person is matched other wise the person is not authenticated. The input image is pre-processed before fed into the model. The model expects the image size as 224 x 224 x 3 where the dimensions are 224 x 224 and colour channels are three.
The implementation of the proposed algorithm is executed in Google Colab with python3 API (Bisong, 2019). We executed the authentication algorithm in Google cloud and evaluated the results. For the encryption of the standard questions standard asymmetric algorithm RSA (Zhou & Tang, 2011) is applied. SHA-256 (Appel, 2015) is used for generating the hash digest for the security answers. During the execution of the security questions based authentication, 1000 replay attacks are initiated and later the replay attacks are activated for the next session. The attack failed in all the cases due to the random question generator. The CSP generates random security question to user which is not generated in the previous login session that reduces the vulnerability of the replay attack which is shown in Figure 4.
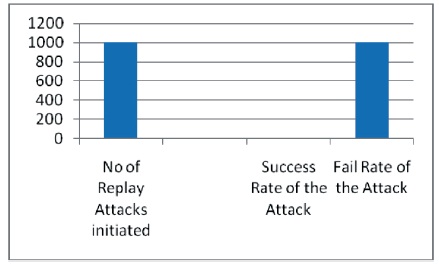
Figure 4. Man in the Middle Attacks Initiation
The biometric face images are collected from the different users of the organization. We applied the model for the users of our organization and labeled faces in the wild dataset. Even we applied the model with the less number of images and the model got 98.78% accuracy for labeled faces in the wild dataset. The dataset contains 13K images of 5K people. The researchers fed 2.6M images to tune the model weights.
The Figure 5 shows the sample image data set (Brownlee, 2019).

Figure 5. Images Dataset
We applied comparison of two face images using cosine distance measure and the results shown in Figure 6. The two face images are match with cosine similarity 0.000 <= 0.500. Even the test images that are covered with the makeup shows the accurate results as in Figure 7 & 8. In Figure 7, the two face images are match with cosine similarity 0.260 <= 0.500, even when the second face image is covered with the makeup. In Figure 8, face images are match with the cosine similarity 0.302 <= 0.500, in which the first image is with makeup and second image is normal image.

Figure 6. Face Verification Test with Two Different Angles

Figure 7. Face Verification Test with Normal and Makeup Image

Figure 8. Face Verification Test with Makeup and Normal Image
2000 authentication requests initiated during the execution of the application. Among the 2000 requests, 1500 requests are generated from the authorized users and 500 requests from the fraud users. The application accepts only 1500 requests from the genuine users and the remaining requests are denied as shown in Figure 9.
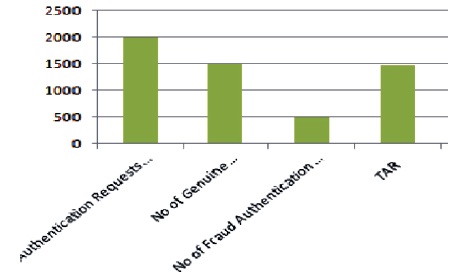
Figure 9. Authentication Requests Initiation
The analysis of the proposed model for the security of the credential parameters is stored in the cloud database and is verified by performing the attacks like replay attack, collision resistance attack, information hacking, image spoofing attack. The proposed scheme with stand against all these attacks.
In this, the attacker pretends like legitimate users and access the services from the cloud service by capturing the credentials in the previous session. The proposed scheme against this attack is by answering the different security questions every time which is randomly generated by the cloud providers. Even if the attacker captures the hashed credentials, it will not be useful in the next session and if the user two times wrongly enters the answer the account is blocked immediately and alert notification is sent to registered mobile and email. If the user wants to revoke the account he/she must send the revocation request to the CS by submitting the userID, and password. If these details are true then CS sends the OTP codes to the registered mobile and email. The user needs to submit these codes to the CS and if the both codes are valid then the account is revoked and again the user is allowed for updating or generating new security question along with the answers.
A collision attack means that two different types of the messages generates the same digest. SHA-256 is hashing algorithm to secure against the collision attack.
Cloud server and employees of the cloud provider is not a trusted entity. There is a chance of theft of the security questions and answers. Even if the cyber attacker stole the security questions, the information is useless due to the data in the encrypted format. The confidentiality of the security questions are satisfied using asymmetric encryption algorithm and the strength of the algorithm is based on the large key size.
Allows the user to guess the credentials of the users in the trail and error. In our application, even the cyber attacker knows the answers, he/she does not know the random value. The random value is considered as double type which is very complex to be identified by the attacker.
It allows the attacker to capture the sensitive information from the CS without proposed authentication. In this, the insufficient authentication is not possible due to the information which is not in the plain text format at the cloud server.
The proposed hybrid authentication enables strong security to the cloud users who are accessing the services from the cloud service providers. The proposed work is implemented in the Google Colab cloud using Python API. The password based authentication technique is implemented with a strong secure password rules. The security based question privacy is performed using RSA algorithm and the privacy of the answers are implemented using SHA-256 hash algorithm. The OTP based authentication generates OTPs to the mobile number and email. These two OTPs will be entered by the user within a reasonable amount of the time. The biometric face authentication is implemented using VGG and VGG face 2 model that is considered as a transfer learning, and cosine distance measure is considered to find the similarity of the two face images. The combination of the techniques enables strong security and are easily used by the users.