Figure 1. Process of Blockchain
Data or any kind of information is an important resource. Storing the data and securing it is one of the main concern of nowadays. Everyday, the industry is dealing with major privacy issues. The common user want a solution for these issues so that they can protect their data from third party or from any kind of data hacking; And this problem is solved with the involvement of cloud technology. Nowadays, everyone is familiar with cloud environment and cloud environment has also ruled over the market whether anyone from technology side or non-technology somewhere is storing their data on cloud; Because storing data into memory is also a very tedious task and even requires lots of maintenance. So, everyone is bound to store data in cloud storage to free from these burden. Blockchain has recently emerged as fascinating and innovative technology to face data integrity problems in the environment like cloud. In this literature, usability of Blockchain in cloud has been discussed and shown how it can be used to make cloud more secure. Major threats have came to an end after the participation of technology like blockchain.
Cloud computing is one of the greatest inventions. It is the need of today's generation. It freed mankind from storing the large quantity of data on physical hardware. It helps the users to access their data online from anywhere and at any time. Today, whether an individual or group of organization everyone is bound to use this technology. Many organizations have shifted their whole data centre on the cloud and are free from maintaining it physically. But with many benefits and advantages, it has some implications (Rohith & Anand, 2018).
As we all know, today everyone's data (audio, video, documents, texts, bank data, etc) is somehow stored on the cloud because no one wants to waste their time in managing those data but with this, a major threat to data integrity is increasing day by day. Current cloud computing market is at risk. Many cyber attacks are happening every day. Data are the major target for the cyber attacks, which undermines the fundamental properties like confidentiality, integrity, authenticity. Compromising confidentiality discloses private data and compromising with data integrity is harmful as it totally tampers the data by deleting some of the important files or alter it in order to produce an unauthorised effect. Once the data integrity is compromised it is difficult to retrieve data as it is lost forever. Due to all these problems the new concept has arrived, the concept of blockchain (Hashmi, et al., 2018).
Blockchain is also one of the best inventions of today. The reason many digital currencies, cryptocurrencies have made a great impact on the market. This technology is not just for digital currency but on many other sectors as well. It also made a great impact on the cloud market. Many problems of the cloud have come to end by using blockchain technology. Many big organizations have started implementing and practising this technology on the cloud to remove a major threat to data on the cloud and make it smoother for users to use. Blockchain is based on a peer-to-peer network, which means that there is no head or a boss, everyone participated in the network has equal importance and responsibilities (Esposito et al., 2018). The data is divided between all the users. It stores data and uses a hash function to keep the data secure. The hash code of previous data and current data is attached to the file, so if any third party ever try to modify or alter data the hash code also gets changed, which flagged that the data modification has been done and after that instantly that person gets blocked by all the user and original data is again retrieved.
Blockchain cloud storage takes the users data and breaks up into tiny pieces of data. It then takes these pieces of data, encrypts them to add an extra layer of data and distribute them throughout the network. This is done by blockchain features such as cryptographic hash function, public/private key encryption. Hash of previous data and current data both are attached with the block so if any third party able to change any data the hash value changes as a result hash value of all the blocks changes, which shows that someone has tried to tamper or alter the data. The data that is being stored throughout the blockchain ledger is split up and hashed a significant number of times. The different pieces of hashed data are not stored in the same storage device. They are split randomly throughout the network. This ensures even if a hacker is able to decrypt the data, he is not able to get the entire file. The node is not able to figure out the owner of the data so that the owner remains anonymous. As a final safety precaution, when a user goes to take back their data those copied shreds are compared to make sure they are all identical as shown in Figure 1. If something gets flagged indicating that the node has tried to manipulate or alter the data that node immediately gets blocked by other users (Alansari et al., 2017; Zyskind, Nathan, & Pentland, 2015).
In the first discussion, the author has given the brief introduction of blockchain in different areas related to bitcoin, cryptocurrency and electronic cash. Furthermore, this paper discussed about how blockchain provide data security. In the literature part, the author started with discussing blockchain technology and its working like how the technology works, what different techniques the technology uses to keep the data secure same as discussed earlier in the introduction part. Moving ahead the author given a quick introduction of bitcoin (a digital currency, invented by Satoshi Nakamoto) and how it uses blockchain technology. The author has mentioned some of the blockchain based case studies on the security of bitcoin like how the users have loose their bitoins due to hacking (Sai et al., 2019). The case study that they discussed are that Mt.Gox (a Tokyo, Japan based bitcoin exchange) lost USD 8.75 million in June, 2011 and later in February, 2014 lost another USD 470 million. Another study that mentioned is how Instawallet (a bitocin based wallet) lost USD 4.6 million and how a anonymous sheep marketplace shutdown after the loss of USD 100 million. The author in the next section discusses the authentication process that how it became important to strengthen the authentication process and how two-way authentication process based on ECDSA is important to stop the attackers from hacking the bitcoin. In the next section, the author discusses about the secure blockchain solution for cloud computing putting the light on how storing data on cloud storage is risky now and how user data is not secure in cloud platform and any disclosure to the data can tamper the data and undermines CIA properties- confidentiality, integrity and authenticity. Due to these all problems how blockchain can be a life changing experience if merging cloud with blockchain technology.
In the second paper, the authors discusses about the threat to data in cloud and how disclosure to data tampers the overall data and once the data is lost it could be retrieved. The paper discusses what are the cryptographic tools that can be used to keep the data secure. It discusses that in 2015, kasperky lab has lost the amount of USD 1 billion due to cyber attack. Moving ahead the author told that these all problems have only one solution the blockchain technology and how it gained pace in all these years and how blockchain technology can be helpful to keep data secure. The paper also discusses a case study the European sunfish project based on federation as service and how the data can be revolved only among the participants of the network securing the information of the user, No outsider can access the data stored in the network providing full confidentiality, integrity and authenticity. In the next section, author discusses about threat to data integrity like how malicious alteration of data has been done, how one member updates the database without informing the other members. The author discusses about stability and performance of blockchain technology. In the paper the author thrown light on some of the open research questions like how to improve performance, measure data integrity, enhance stability and given the answer to these questions. The author also proposed their own idea of effective blockchain database. Then at the end the author discussed some related works. In this section they mentioned that it is always be a challenging task for the user to check integrity of its data and for this purpose some studies provide the first model that allow the user to check the data integrity. For cloud, Remote Data Auditing (RDA) is an answer for empower auditability of redistributed information through a trusted third party, which eases the calculation trouble on the client. Various RDA methods have been proposed to improve both efficiency and security. These all based on trusted third party but if any malicious attacks happen then all will go invain and data can never be retrieved if lost and for this problem blockchain is the solution (Sharma et al., 2018).
In the third paper, it discusses the same; the introduction of blockchain technology and different IT markets has uses this technology due to better stability, performance etc. This paper goes same as all the paper discussing about the security issue of data in cloud and blockchain is the solution. The paper started with discussing the methodology of blockchain technology as we have discussed above in this paper and furthermore moving ahead author discusses how Bitcoin uses the blockchain technology. Same as the first paper the author discusses about the same case study that the first paper discusses. The paper also discusses the ECDSA two party signature. Moving ahead the author has mentioned about 51% attack. The author gave the idea of improved blockchain and what it discusses is as follows. As the present payment framework is mind boggling and transaction moderators are dispersed, many security assaults are expanding. A client proposing to exchange cash will recompense a yearly participation charge to get a token and utilize it to buy merchandise or put into administrations. The users bank and the shipper's bank cooperate with one another rectifying the expense and a market expecting to utilize the token gets it from a bank and utilizing it to buy merchandise and ventures. A disentanglement of exchange is needed as more individuals are on cell phones to buy products or administrations. Concerning the advantages of performing a regular transaction as a distributed transaction utilizing blockchain, the transaction isn't just dependable and obvious yet in addition cost proficient since there are no outsiders included. Likewise, transaction utilizing blockchain can be finished in all respects rapidly since separation does not influence the exchange, while customary exchanges over the outskirt can be extremely moderate. Also, centralized transactions are helpless against holes of significant information when the overseeing server is hacked since all the profitable information is overseen in the local server. Conversely, making it extremely hard to assault blockchain based exchanges since all significant information is disseminated and an attacker have to hack and modify 51% of the shared exchanges. Subsequently, the improved blockchain must be utilized for exchanges to take care of the issues of traditional exchanges. In last section the author discussed about secure blockchain solution for cloud computing putting the light on how storing data on cloud storage is risky now and how user data is not secure in cloud platform and any disclosure to the data can tamper the data and undermines CIA properties confidentiality, integrity and authenticity. Due to these all problems how blockchain can be a life changing experience if merging cloud with blockchain technology (Gaetani et al., 2017).
Stability: Data on a cloud includes a central server where all the data are stored but in the blockchain technology all the participants stores the copy of data. This decentralized concept made blockchain stronger than any other technology. As all the participants stores the copy of shreaded data, if anyone try to erase the data the original data can still be retrieved saved within database of other participants.
Many banks, big companies spend lot of money to keep their data secure but still lasted with many cyber attacks. With the involvement of blockchain technology the company can keep their data secure and can establish stable and unbreakabale system (Kumar & Anand, 2017; Zyskind et al., 2015).
Accessibility: Storing large quantity of data on a physical hardware can be a threat if contains some confidential items. Anyone, at anytime can access the information and all the secrets can be revealed and even anyone can try to forge the data without our knowledge, which can be a life shaking. By appling blockchain technology no one can access the data without our knowledge. When we encrypt our data we get two type of keys-public (for viewing files) and privates (or modifying, updating the files). These two keys are only remain with the owner and owner can give this key to a particular person to see or modify the files.
Better Security: Blockchain technology in cloud provides better security. As in cloud, the data stored is at risk all the time. If the third party somehow manages to get the users encrypted data it compromises with confidentiality of the data. Data can be altered and modified in order to produce unauthorised effect. But by appling blockchain technology the security get strengthened and no third party can access the users data as data is encrypted using the hashcode of previous and current data file and hash codes are generated using the concept of hash function. So if any third party users somehow try to change the data then hash code changes and all the participants of peer to peer network can identify the change that has done and can validate wheather the change that has done is valid or not and can block instantly if it is not valid. If third party user get access to the user's data then he can get only one part of the data as data are divided and distributed among the network and the data is kept secure (Tosh et al., 2018; Wang et al., 2018). So blockchain technology plays a pivotal role in providing a powerful security in cloud environment.
Faster Settlement: Traditonal system always take lot of time to check wheather a transaction or information provided is true or not and in order to validate those informations, the systems often takes huge time. Using new blockchain concept these works can be done in a nick of time and saves lot of time of the instituitions and the users (Wang et al., 2018).
Resiliency: Traditional systems are prone to attack as they are centralized, which means they have single point of failure. This implies that any type of external attack on data stored in cloud storage can be devastating as it leads to total loss of data and these problems can be devastating even for a organization or a economy. Blockchain technology is risilent to these types of attacks as all the nodes has the copy of original data so any type of changes or modification can be easily detected and flagged and original data can be retrieved at the event of data loss (Wang et al., 2018).
Siacoin: Launched in 2015 and considered among leading blockchain cloud storage platforms. It first checks the amount of storage capacity using its protocols and after that send it to their network for creating data market place. It works on proof-of-work. IT does not require any third party, NO sign ups, No servers etc. Sia is 90% cheaper than many other cloud providers. 1 terabyte storage of Sia costs $2 per month which is cheaper than $23 per month of Amazon S3 (Sai, et al., 2019).
Filecoin: It is based on interplanetary file system protocol which is peer to peer protocol based on bitcoin blockchain, which allows user to share online content. Storage providers to Filecoin network is the miners. One need to download the filecoin software to be a miner and can provide their storage and can earn some file coin (Li et al., 2019).
Maidsafe: The main aim of the organisation is to provide security, privacy and freedom to the user. They Designed a data network called Safe Network, which is fully autonomous and decentralized. Being autonomous and decentralized it can never be shut down, blocked and controlled. Safe network encrypts the user data by default and divide it into pieces and distribute it across the world which cannot be detected and even the user access is untraceable (Li et al., 2019).
Storj: It allows their clients to lease stockpiling from their peers on the network. All organized exchanges are led in storj's crypto assest storj, a token propelled on the ethereum blockchain. It provide full security and privacy to the data. It provide the private key to the users, which give the full confidence that only the users can able to access their data and no one else. Even it allows their client with the benefit of renting their extra storage space to their peers (Li et al., 2019).
Initial Cost: Blockchain technology is the innovation that has invented to bring certain problems to an end. The technology provide certain benefits related to timeliness, productivity, reduced cost but putting this technology into reality is expensive as it requires certain software on which it works, is difficult to acquire, purchase or produce inhouse. So, bringing this technology into reality will be a dream for many small sized business as they can't afford to establish the technology due to high cost (Tosh et al., 2018; Wang et al., 2018).
Processing Speed: Whenever a new data or information is to be added in the public ledger it needs to be validated by the miners. Miners spent a time on finding a right key for each transaction in order to add it into a ledger, which requires some time to approve and validate each transaction and maintain a ledger. Tens and thousands of data is required to validate and processing time is less to validate each transaction (Wang et al., 2018).
Public Exposure: Blockchain is a common name for the people involved in technology but still a nightmare for general public. Public still don't know the use of blockchain. In order to bring this technology into mainstream, public exposure to this technology is required. Blockchain has revolutionized many big industries but still a puzzle for public. Public always correlates blockchain with bitcoin and thinks about black market or some illegal activities. There is a confusion between bitcoin, cryptocurrency and blockchain and it is necessary to bridge the gap between these all things to remove misconception.
Computational Power: Since, blockchain concept requires a proof-of-work mechanism to validate a transaction. Validating a transaction requires a computation power to solve complex mathematical problems and algorithm in order to process a transaction. Solving such a complex algorithm requires high computation power to provide to computers and equal amount of power is required to cool it down.
Quantum Computing: Since it is impossible for a single party to challenge blockchain technology in terms of security but with the quantum computers (in future) it will be easy to crack cryptographic keys with brute force attack approach in a nick of time so it is necessary to build a strong cryptographic key so that it is hard to break.
Different leading giants are using blockchain technology for solving there big problems in different ways. Microsoft allows the end user to design and develop there own blockchain environment with there own speciality. European Union's Horizon 2020 research and innovation programme sponsors the sunfish platform, which allows to design cloud fedration platform which will be designed, democratic and distributed by nature. Peer ledger was founded in 2016 for using the great benefits of Blockchain in different area. The details mentioned in the Table 1 shows, big Companies like IBM, Oracle and Government Organization like iEX are also using the benefits of Blockchain technology to facilitate the society.
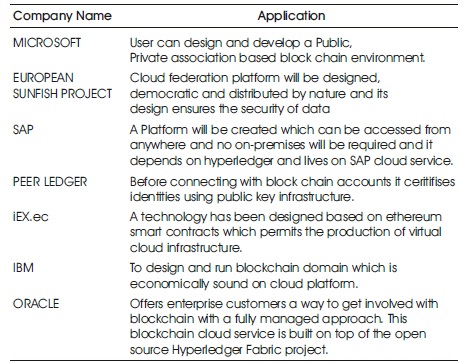
Table 1. Different Blockchain Application used by Different Companies
The difference between centralized and decentralized cloud ownership technology is shown in Table 2.
As discussed earlier, the advent of blockchain technology has solved many problems. Many organizations are now using blockchain technology in their system to make it much better and easier to operate. With the emergence of this technology, many new projects are in line, which are going to happen in future.
The organization like ConsenSys has taken a major step in the cloud market. It recently partnered with Semiconductor producer AMD and Halo Holdings an Abu-Dhabi based investment management firm and working together on a new project called W3BCloud (cloud computing infrastructure based on blockchain). The objective is to create an upgraded data centre solution for increasing blockchain job through the production of W3BCloud. Utilizing ConsenSys' blockchain programming aptitude, W3BCloud plans to create enhanced arrangements governed by AMD that are fit for supporting an assortment of blockchain job and business ventures, just as quicken the selection of decentralized applications (Tosh et al., 2018).
Cloud computing is incredible in light of the fact that it allows the organisation to increase infrastructure support for their advancement. The administration invalidates the need to purchase costly hardware forthright while likewise guaranteeing simple adaptability in the event that an item becomes famous quicker than anticipated. The odd reality about the cloud market is that it is a market that can be upheld by the figuring force and capacity limit of any gadget. Each family has unused capacity or computational power at different occasions of the day. This is an unbelievably terrific botched chance as there's a bounty of supply of profoundly looked for after assets, yet the supply can't achieve the asset purchasers. Another startup expects to merge the two most significant advances of today, AI and blockchain, to build up a decentralized cloud that can give anybody the chance to adapt unused computational power and capacity while controlling the savvy economies of things to come.
Deep Cloud AI is building up the innovation to gather overabundance computational power and storage and after that distribute it to purchasers. This will give ordinary individuals a scaffold to ignore their overabundance assets to asset purchasers. Such an advancement opens up a list of advantages, which incorporate more noteworthy market rivalry and higher nature of administration. Deep Cloud AI, can assign assets from hubs that are immaculately near the physical area of the information source. The startup's coordinating calculations will inherently interface asset suppliers with ideal asset purchasers. The improvement in edge processing accomplished by Deep Cloud will bring down the inertness issues looked by IoT gadgets (Mishra et al., 2018; Tosh et al., 2018).
At present, we store our information on either on location servers or cloud servers. All the cloud servers are most likely be claimed by one organization in a specific area. This is called brought together cloud computing.
Swarm Computing is decentralized distributed computing. Nobody possesses the whole framework. Rather, information is put away crosswise over many PCs, each using their extra limit. Swarms of PCs cooperate to provide everybody's information needs. Every PC turns into a capacity unit in a gigantic blockchain empowered system. Swarm computing is profoundly effective, assuming swarm like torrent peers. A swarm is distributed over the earth. This implies in case you're recovering your information, it's originating from the hub nearest to you instead of from the opposite side of the world. So, it will come as quick as would be prudent. Also, in case you're recovering information from various swarms in the meantime, it's all going to come together simply like a torrent when you're downloading information from companions. This is how decentralized cloud can have endlessly better execution, unwavering quality, versatility than a centralized one. It can reliably offer a similar presentation during pinnacle times. When utilization is low, it doesn't require a similar measure of equipment to be submitted. This system can work smoothly and provide business requirements so it doesn't need to physically oversee servers and pay in advance for pinnacle equipment costs (Gaetani et al., 2017).
Google joined hands with Digital Asset, to look at the company's blockchain platform and development tools made accessible on the Google Cloud Platform, and with Ethereum venture blockchain startup BlockApps, to have their fast sending blockchain as a service arrangement stage for undertakings, called STRATO, made accessible on the Google Cloud. This will diminish the specialized boundaries to DLT application improvement by conveying progressed appropriated record stage and demonstrating language to Google Cloud. The users would now be able to investigate ways they may utilize DLT structures on Google Cloud Platform with dispatch accomplices including Digital Asset and BlockApps, and attempt open source combinations for Hyperledger Fabric and Ethereum (Kumar et al., 2016).
Information processing mammoth iExec and driving vitality supplier of France, EDF have met up to keep up the last's cloud based foundation. EDF will fabricate another decentralized application on Ethereum naming this application GPUSPH. GPUSPH will supposedly profit by the decentralized cloud. The Dapp will deal with Ethereum's adaptability issues by ensuring that all substantial computing is performed under direct supervision. Ethereum has been a standout amongst the most favoured decisions for dapp engineers, particularly in the section of the cloud (Kumar & Anand, 2017).
The decentralized concept made blockchain stronger than any other technology. As all the participants stores the copy of shredded data, if anyone try to erase the data the original data can still be retrieved saved within database of other participants. The blockchain is the key, the big companies are using it keep their data secure. Blockchain has solved many difficult problems of the cloud and yet to solve many. The blockchain provide certain benefits like better stability, performance but blockchain have to deal with certain challenges and cope up with all challenges in order to stand stronger in the market. One of the major challenges of blockchain is quantum computing. With the quantum computers (in future) it will be easy to crack cryptographic keys with brute force attack approach in a nick of time so it is necessary to build a strong cryptographic key, which is hard to break. Major blockchain cloud platforms-Storj, Maidsafe, filecoin, siacoin taking a major step to make better blockchain cloud platform. It is good to see that many works based on blockchain cloud is on track whether it's DeepCloud AI or swarm computing. These projects in future even change the complete scenario of the cloud market. Discussing about Google joined hands with Digital Asset, to look at the company's blockchain platform and development tools made accessible on the Google Cloud Platform, and with Ethereum venture blockchain startup Block Apps, to have their fast sending blockchain as a service arrangement stage for undertakings, called STRATO or Information processing mammoth iExec and driving vitality supplier of France, EDF have met up to keep up the last's cloud based foundation. EDF will fabricate another decentralized application on Ethereum naming this application GPUSPH. These are some projects on which everybody has eye on.
At last, we want to say that we have tried to help the readers so that they know all about the blockchain cloud computing, all the aspects related to the technology, benefits, challenges, many related works has also been discussed so that the reader get the complete knowledge regarding the technology and ongoing woks in the market.