Figure 1. Conceptual Framework of the Cloud Encryption System
Cloud computing is defined as the delivery of on-demand computing resources ranging from infrastructure application to datacenter over the internet on a pay-per-use basis. Most cloud computing applications does not guarantee high level security, such as privacy, confidentiality, and integrity of data because of third-party transition. This brings the development of Blowfish cloud encryption system that enables them to encrypt their data before storage in the cloud. Blowfish encryption scheme is a symmetric block cipher used to encrypt and decrypt data. Microsoft Azure cloud server was used to test the proposed encryption system. Users are able to encrypt their data and obtain a unique identification to help them retrieve encrypted data from the cloud storage facility as and when needed.
Cloud computing generally refers to data being stored centrally in cloud and are accessible to clients through thin clients and lightweight mobile devices. Cloud computing infrastructures over time have provided a way for data to be stored and accessed by customers easily given the availability of internet connection. Cloud computing maintenance and technical services are provided by cloud provider who must ensure the quality of services. Cloud computing has offered better storage facilities to schools, organizations, financial institutions, traders, and government offices. Data stored in cloud computing applications serve as backup in case of loss of data in an unlikely event (Latiff, Abdul-Salaam, & Madni, 2016; Xia, Wang, Sun, & Wang, 2016; Rittinghouse & Ransome, 2016).
Cybercrimes or internet crimes are unlawful actions carried out using the internet or cyber environment by loopholes, weaknesses, and vulnerability of a system (Internet Crime Complaint Center (IC3)). The need for information security increases as technology advances, which also allows for free information obtaining tools online such as whois lookup. Data retention therefore needs a more secured platform for storage of data. Note that the accessibility and availability of this data to potential authorized users must be made easy. Data owners are motivated to outsource their complex data management from local sites to commercial public cloud for great flexibility and economic savings bringing about the advent of cloud computing, which has by far provided the best platform for authorized users.
Encryption is used to convert data into a form that is not comprehensive to unauthorized users with unauthorized access to data stored or on transit. Encryption is a method used in ensuring privacy, confidentiality, integrity, and authenticity of data (Abdullahi & Ngadi, 2016; Said, 2005) Over time, encryption have been used to hide or protect information of high secrecy and since the advent of cloud computing which provides a pay-per-use platform to outsource our data. Human have referred back to the way of hiding data back in 1500 BC, which is now known as encryption. Encryption or the ability to store and transmit information in a form that is unreadable to anyone other than the intended person is a critical element of our defense to these attacks (Kaur & Singh, 2013).
Blowfish encryption scheme is a symmetric block cipher designed by Bruce Schneier in 1993. It includes a huge number of encryption product and was designed as an alternative to replace the obsolete Data Encryption Scheme (DES). Blowfish takes a variable length of 32 bit to 448 bit with a default of 128 bit. Blowfish is unpatented and license-free, which allows for its free availability to users (Schneier, n.d.). Blowfish is fit for applications whose key does not change often for instance an automatic file encryptor or a communication link (check for more instances). It is relatively faster than DES when implemented on a 32-bit microprocessor with huge caches such as Pentium and PowerPC. The blowfish algorithm consists of two parts; a key-expansion and a data-encryption part. The key-expansion part refers to the conversion of a key into many sub-keys. Data encryption occurs through a 16-Feistel Network. Each round consists of a key dependent permutation, a key, and data dependent permutation (Xia et al., 2016; Krishnamurthy, Ramaswamy, Leela, & Ashalatha, 2008).
The main contributions of this research manuscript are chronicled as follows:
The aim of this research paper is to developed Blowfish encryption scheme for secured data storage in public and commercial cloud computing environment.
Cloud computing applications are designed for clients to outsource their data, access their outsourced data over the internet, and also serve as backup for individuals ranging to organizations, schools, and financial systems. Cloud applications which includes Cloud App, Waze, Box.net, AudioBox.fm, Jouku, icloud does not ensure absolute security in terms of privacy, integrity, and confidentiality of the data because of third-party intervention. This brings about the development of blowfish encryption scheme application to properly secure user's data in both public and commercial.
Thakur and Kumar (2011) conducted simulation of commonly used symmetric encryption scheme which involves Data Encryption scheme (DES), Advanced Encryption Scheme (AES), and Blowfish algorithm. The simulation was put into practice using Java programming language and the types of encryption/decryption mode. The encryption/decryption mode is Electronic Code Book (ECB), Cipher Block Chaining (CBC), Cipher feedback (CFB), and Output Feedback (OFB). In EBC, data is divided into 64 bit block with each block been divided are encrypted once at a time. CBC involves an already encrypted block to be XORed with the next plaintext making each block dependent on previous blocks. CFB mode enables encryptor to handle plaintext that is not up to 64-bit by adding dummy byte to enable encryption of the plaintext. OFB is same as CFB, but less secure than CFB because it requires only the real ciphertext to find the previous plaintext. Java Cryptography Extension (JCE) and Java Cryptography Architecture (JCA) contain java.cypto and java.security that manages wrappers for DES, AES, and Blowfish. The algorithm setting shows that the plaintext is divided in small block size (bits) and key size (bits). The simulation was conducted more than once to achieve accurate result necessary for comparing the different algorithm, and the AMD sempron processor with 2 GB RAM was used. Compilation of the simulation program was made possible with the use of 1.7 development kit for java in its default settings. Result of these comparison with different data load and the mode of encryption/decryption shows that blowfish has better performance than AES and DES in terms of processing time.
Chaplot (2015) used Matlab to design and implement Blowfish for encrypting and decrypting images. The paper includes the description of Blowfish algorithm as involving a 16 round feistal network for encrypting data. A feistal network refers to means of changing functions to permutation. Akshit et al. further gave steps of how the feistal network works. The fiestal network first splits a block of divided message into two equals. It then swaps the halves of the divided message. A function and a key is applied to the other half and then XORed. It further shows that Blowfish algorithm consists of two parts; data encryption and key expansion parts. The advantages of blowfish stated here includes; been accepted as one of the strongest techniques, unpatented and license free and highest speed algorithm known. The disadvantages include being vulnerable to attacks on weak keys, cannot be used for files more than 4 GB because of its small bit block size and blow fish has successors. The simulation shows how Blowfish can be implemented on a different platform (Matlab) and used to conceal an image.
Gahi, Guennoun, and Khatib (2000) listed a few security issues that the cloud service encompasses and possible solution to the listed problems. In a case of loss of physical security, secure data transfer was proposed. To ensure data integrity during transfer, storage and retrieval, a secure software interface is a possible solution. Data separation ensures the privacy of data from being shared to other parties. NetBeans IDE with Java was used to implement AES, DES, RSA, and Blowfish algorithms. The implementation of multiple algorithms gives users an opportunity to use the security algorithm of their preference. Comparison of the algorithm was further carried out in terms of platform, key size, key used, scalability, initial vector size, security, data encryption capacity, authentication type, memory usage, and execution time. Different parameters used for comparison for the different encryption schemes so far show that AES execute in less time. Blowfish memory requirement is as low as 5 kb, more encryption time being used by DES and RSA use the longest memory size and execution time.
Curino et al. (2011) introduced a hybrid technique of security algorithm, a combination if RSA and Blowfish. The consideration of such combination was based on the fact that Blowfish is effective and unpatented, which makes the cryptosystem cost effective and RSA which is almost always considered for its digital signature. The proposed technique can be used for cloud computing on FPGA network.
Symmetric and asymmetric features of the chosen algorithm allow the use of small key size for the asymmetric technique. The symmetric technique always uses high key size to reduce the possibility of direct key substitution. The hybrid technique can be applied to the third layer of cloud computing. FPGA is easily used to implement the hybrid technique and it uses little resources out of the available resource. Analysis of the implementation response on FPGA shows that the combination of the two algorithms is better than any other technique. The proposed technique is further implemented using VHDL, hence, the algorithm is secured and ensures better authentication for cloud computing data.
Itani, Kayssi, and Chehab (2009) presented 'A performance based comparison of various symmetric cryptographic algorithms in runtime scenario'. The purpose of the paper is based on the detail analysis of the terms, concepts, terminology, and analysis of some of the cryptographic schemes (AES, DES, and Blowfish). Authentication, privacy, integrity, and non-repudiation were mentioned as the security requirement need for a secured communication. Cryptography is of three types, which are; symmetric or secret key cryptography, asymmetric or public key cryptography, and hash function. The secret key cryptography is of two classifications; stream cipher and block cipher. Encryption and decryption has models of operation, namely; Electronic Code Book (ECB), Cipher Blocks Chaining (CBC), Cipher Feedback (CFB), and Output Feedback (OFB). A detailed analysis of the few symmetric encryptions was given and also the performance result of the symmetric encryption scheme in the different models of encryption and decryption were given. It was deduced that asymmetric algorithm consumes more time than symmetric algorithm.
Li, Yu, Cao, and Lou (2011) proposed an Effective Privacy Protection Scheme (EPPS) to satisfy users privacy and also ensure performance of cloud systems in different environment. Cloud Data Protection System (CDPS) includes detailed EPPS and description of its content. Chuang et al. gave a detailed description of the CDPS architectural components, which are quantification models, privacy analysis, data protection procedure, and data division. Simulation environment used are; PC with Intel core 2 Duo E8400 3.0 GHz CPU and a CentOS 5.2 Operating System. The result of the simulation shows the scheme's total cost time is more than the other algorithms for the scheme being compared with. The security of the scheme is also found out to be effective despite a 46% subtraction to be able to compare it with other security algorithms. The scheme is said to be an effective means of protecting users' privacy and performance in the cloud environment with increasing performance overhead of the system.
Schneier (n.d) proposed the use of different encryption algorithms to increase privacy of data in the cloud. The cloud types and characteristics were discussed to give an understanding of what the cloud entails and its services that benefit owners of data. In a given analysis between RSA, DES, AES, and Blowfish, it was discovered that Blowfish key length is larger than that of AES. This is implemented using JDK 1.6 Eclipse IDE. Google app Engine SDK 1.6.0. The scheme allows a user to select an encryption scheme of their choice after authenticating into the cipher cloud. The data of preference is then sent to the cloud server, the sever then decrypts the request with a generated symmetric key and further encrypts it with RSA.
Hashem et al. (2015) proposed a cloud based architecture for owners of data to ensure confidentiality and privacy of their data. The architecture provides a user friendly framework that enables the selection of an encryption algorithm. The framework includes steps every user pass through to secure their data. A user will require a form of authentication, which requires Id and password. After a successful authentication, the user is presented with a list of options (view files, upload files, delete files, and download files). The upload files button will transmit the user's data to the cipher cloud through an encrypted connection using HTTPS and the file is encrypted using a symmetric scheme chosen by the user. Downloading of a selected file by the user will be decrypted with the previous selected scheme. A new user will be required to create an account using google account and other steps to successfully upload a file are displayed for the user.
Lee, Chung, and Hwang (2013) presented a detailed analysis of commonly used symmetric encryption system (AES, DES, 3DES, and Blowfish) and asymmetric encryption system (RSA). Symmetric scheme was found out to be faster than asymmetric key encryption. The analysis includes a table that shows the difference and similarities between the symmetric algorithms, which indicate the superiority of Blowfish as compared to another encryption algorithm.
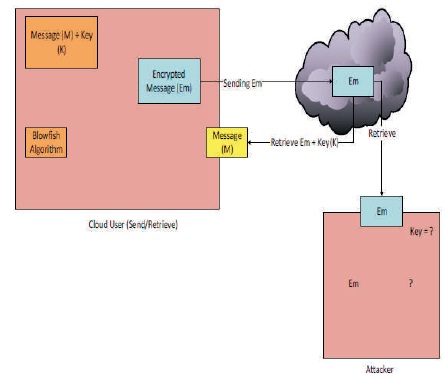
The research work is based on converting data into a non-comprehensible form using Blowfish encryption scheme. The scheme is a symmetric algorithm, which means that it requires same key for encrypting and decrypting messages. Individuals who intend to save their data in the cloud can adopt this method to convert data of their choice before outsourcing it to commercial cloud as shown in Figure 1.

Figure 1. Conceptual Framework of the Cloud Encryption System
Cloud user (send/retrieve) is the owner of the data that is supposed to be sent to the cloud environment. The cloud user has a message (M), which he or she wishes to encrypt. A key (K) is needed for encrypting the message. Blowfish is the algorithm used for the encryption and decryption process. Encrypted message (Em) is then send to the cloud via a secure communication protocol HTTPS. The cloud service knows the message to be Em, which is not comprehensible to an attacker given the possibility that the cloud system is compromised. Em would be retrieved, but the key remains unknown to the attacker. These gives an owner of data stored in the cloud an edge or another level of security over other owners using same cloud system.
where
k ∈ K is a secret key from a set of keys in K
m ∈ M is a set of possible embedded messages in M
c ∈ C is a set of audio containers in C
s ∈ S is a set of stegos generated by embedding m in c
Therefore, audio steganographic system for information hiding can be divided into two stages: an embedding transformation stage and extraction of information stage.
Let embedding transformation be represented as EmT
Extraction transformation be represented as ExT
Therefore,
EmT : C x K x M → C
ExT : C x K → M
Such that
for m ∈ M, c ∈ C, and k ∈ K
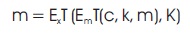
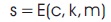
Let Pc represent the distribution of probabilities of steganographic containers c or Pc(C)
Ps represents the distribution of probabilities of embedded stego - object s or Ps (S)
Using relative entropy, it shows that the distribution (D) of Pc and Ps are compared
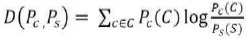
Interpretation of model expressed in equation (3)
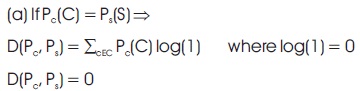
This shows that the stegosystem is absolutely secured. The attacker cannot differentiate between the stego-audio and the container
(b) D(Pc, Ps) ≤ ε, where ε is a non-negative value, which c s implies that the stegosystem is ε -secured. The smaller the value of ε, the more secure the stegosystem.
The flowchart diagram analyses problems in other to achieve a possible solution as shown in Figure 2.
In Figure 2, x is a 64-bit plaintext to be encrypted, where dummies are added to a plain text that is not up to 64-bit. X is divided into two equal halves, that is 32-bit; leftmost plaintext (xL) and rightmost plaintext (xR).
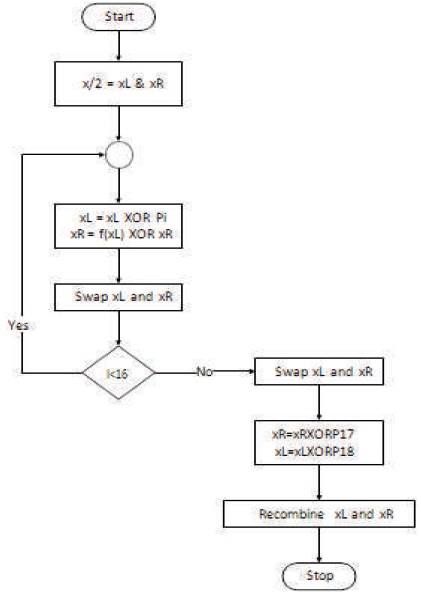
Figure 2. Blowfish Encryption Flowchart
p is an array of 18, 32-bit subkey, which is XORed with the leftmost 32-bit of plaintext and the result is passed to the f function of Blowfish.
The result becomes the rightmost 32-bit for the next round, and the output of F function is XORed with the original rightmost 32-bit of plaintext becomes leftmost 32- bit and so on as shown in Figure 3.
The database design which was done in Microsoft Azure's cloud platform consists of a table with four fields which are ID, unique ID, username, and ciphertext. This allows user information to be stored and retrieved when needed.
The software is developed using C#, Visual Studio, and Microsoft Azure platform due to the characteristics they possess and how they are closely associated. C# is referred to as a modern, object-oriented programming language. Microsoft's cloud computing platform Azure has been existing for 5 years. In 2011, Scott Guthrie took over the Azure team Application Platform team. The Azure user interface was then rewritten from a silver-weight application to a lightweight HTML5 web portal. During the evolution of the Microsoft Azure in 2014, it became a comprehensive, robust cloud platform for not only IaaS, but also Platform-as- a-service (PaaS) cloud computing models (Cao, Wang, Li, Ren, & Lou, 2014; Madni, Latiff, Abdullahi, & Usman, 2017; Latiff, Madni, & Abdullahi, 2018; Hoang, Katz, & Malozemof, 2015).
The software requirement used to develop this system includes C#, Microsoft Azure cloud server, Microsoft Visual Studio. The algorithm used is Blowfish algorithm which is a symmetric key cryptography, which encrypts 64-bit block with a variable length of 128-448 bit.
The system requirement for designing the encryption and decryption application are; 500 GB hard disk, 4 GB RAM, and Core i3 processor.
The encryption system was implemented using Microsoft Studio 2015 platform that has a Microsoft Azure sdk linked to the Azure's cloud server. The Azure cloud server allows a database to be created. The database and its tables are created on the Azure's platform with a strong internet connection. The encryption system cloud encrypt startup page has four buttons, the first requires a new user to create an account, the second allows a previous user to access a previous message, the about button gives a short description of the system (as shown in Figures, 4 and 5).
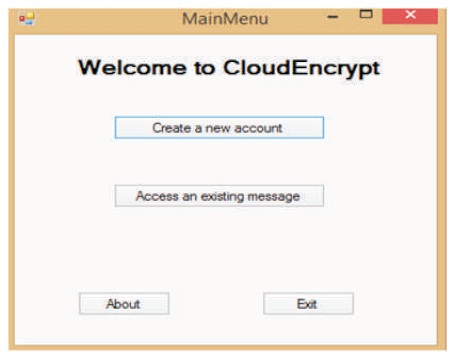
Figure 4. Login Page
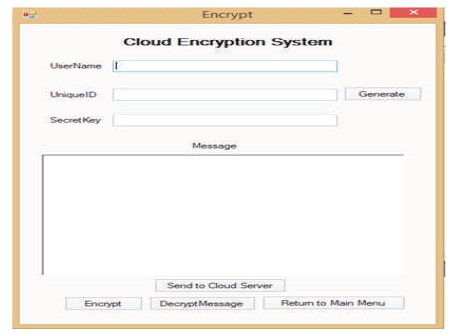
Figure 5. Encrypt Page
A new cloud user is required to register with a username and password of preference, the unique Id which serves as an extra form of authentication is generated by the system. The unique ID is required anytime the user wants to save the work in the cloud server as shown in Figure 6.
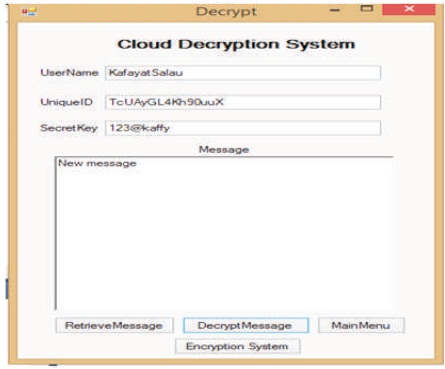
Figure 6. Decryption Page
Upon retrieval the message can be decrypted with the unique Id. The unique after been generated in the first step is required to be kept safe by the use because the system cannot provide an already generated unique ID for decryption purpose. The database of the cloud encrypt system in the Microsoft Azure's platform indicates a table of IDs, username, unique Id, and ciphertext. The system was first tested with a plaintext message and used to encrypt another message before it is stored in the database.
Throughput indicates the number of transactions per second or a ratio of an application handling, and its amount of transactions produced over time during a test. In data transmission, network throughput is the amount of data moved successfully from one place to another in a given time period, and typically measured in bits per second (bps), as in megabits per second (Mbps) or gigabits per second (Gbps) (Madni, Latiff, & Coulibaly, 2017).
Encryption/decryption time defines the amount of time used to encrypt information from a sender point and the time used for decryption of same information at the receiver point (Singh & Singh, 2013).
Channel utilization refers the channel efficiency and packet drop rate in percentage are less ambiguous terms. The channel efficiency, also known as bandwidth utilization efficiency, is the percentage of the net bit rates (in bit/s) of a digital communication channel that goes to the actually achieved throughput (Madni et al., 2017). Figure 7 presents the results of the experiment.
The result of the encryption system shows data in kilobyte that can be encrypted and stored in a database created in Microsoft Azure (cloud) platform. The Blowfish algorithm helps the user to generate a unique Id for encrypting message (m) and same key is used to retrieve data from the cloud. The unique Id serves as a form of authentication used for retrieval of data. The application ensures that no two party can have same unique Id and each user must keep the unique Id secret along with the chosen secret key by the user. The unique Id further helps a user in accessing stored data and decrypting it upon retrieval.
Cloud environment has provided an on-demand, payper- use storage services for users, which enables users to access data stored in the cloud from any part globe over the internet. The cloud environment also has with it some demerits, which includes loss of governance, lock-in capabilities, isolation failure, compliance, management interface failure amongst others. The developed application enables a user to incorporate an extra level of security by encrypting the data before sending it to a cloud environment. The application enhances ease of use of the encryption algorithm and guarantees efficiency of the encryption.
The developed system in its entirety is designed to encrypt message and sent to the cloud server and it also enables decryption upon retrieval. The system can be used by individual user to encrypt text message of choice before sending to the cloud environment. This paves way for easy storage data and encryption of the stored data.