Figure 1. Class based Cloud
Security in Class Based Cloud Data is undoubtedly one of the challenging tasks in Cloud Computing. Class based Cloud structure is totally a new concept where the cloud can be divided into a number of classes. Through this, a protected cloud could be implemented in hybrid cloud which helps to reduce the time and cost of searching and maintenance. Normally, the classes can be divided based on the usage of the cloud and for each and every class, there is a key for data security. This paper explains about the key management to different classes and allows the authenticated users to use them.
In this generation, Cloud based technology is seeking attention in various fields. Normally, cloud technology helps to different sectors to store important data and provide a way to access that data as easy as possible. Now the question is about security, where dealing with huge and important amount of data stored in cloud is a challenging task.
Considering about data protection, there are many approaches that guarantee to do so. It depends upon which type of data that we are storing and which type of cloud we are using. We all well-known that public, private, hybrid clouds help to store data with its own aspects. In public cloud, there is no control on the technology infrastructure and the data can be accessed by anyone. In private cloud, as an organization provides advance security, but resources shared to other organizations are few Hybrid cloud is a combination of both [6].
In order to overcome this, a new concept is introduced called class based cloud structure. The cloud is divided into different classes. Each class can be used for different sectors, such as one class for education and another class for business, and so on. Implementing object oriented concept is an asset in this type of clouds [9].
In order to manage the data in cloud, the data should be divided according to the classes which is called data partitioning. Every class has their own public, private, and hybrid structure. When dividing the classes and assigning the data is completed, we need to next provide security to the classes. Based on the type of classes each class has their own problems as shown in Figure 1.

Figure 1. Class based Cloud
Considering all those problems, we need to create keys and manage them [4].
Normally there are two methods to share data with another user They are
The organization of the paper is as follows: Section 1 presents the literature reviewed. Section 2 presents the basic preliminaries required to escalate the proposed method. Section 3 presents the proposed approach. Section 4 is about Results and Discussions. Finally, the last section is concluded.
Cloud data security issues can be reviewed by many researchers and most of the security attacks to the clouds on networks will find their root solutions. Some of the security issues are,
Considering all the above security issues, many researchers have implemented some of solutions to overcome those issues. We all know that the two major concerns about cloud computing data storage is security and reliability. Clients can store the data in the specific cloud server only if they know that they can access the data at any time and any place. Client can check whether there is a assurance for his data in cloud so that, only he can access his data, but not others who are not authenticated.
The most preferred solutions or techniques (Table 1) for data security in cloud are,1) Preserving multiple keywords: In this technique using multiple keywords in the search request, we can achieve multiple matchings for single request and we have the ability to select the relevant document. This technique is more efficient compared to the single keyword searching. 2) FDE-Fully Disk Encryption: This technique maintains data security in the cloud, where when the entire machine is lost or disk loss happens, we may lost our data. So, in this situation, we can use this technique. It applies encryption transparently on entire disk or machine. 3) Hybrid cloud technology: This technology is for users trust about their data in cloud. This technique helps users to store private data at users end and public data at server. It helps to access the private data of user at any time because the data is at user area and there is no worry about data security [11].
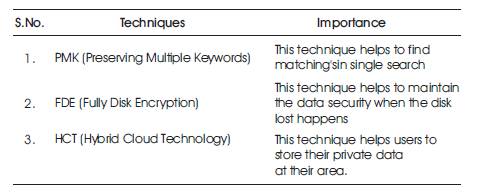
Table 1. List of important techniques
These days, moving the sensitive and important data into the cloud increases rapidly. Cloud service providers are struggling to manage the important data to be secured by using different techniques of data security. However, it is not easy to maintain the entire data safe and secure while the data is growing day-by-day and on the other hand, users are increasing [2].
The main difference between the key management in the cloud and non-cloud areas are leadership and management of the keys. In a non-cloud area, the keys are managed by the user and maintained by using suitable tools for data. In cloud area, there will be a shared model or the cloud service providers who can entirely manage the keys and maintain them.
Cloud Computing key management will largely depend upon various factors. First, the selection of key depends upon the type of the cloud service that users wanted to use. IAAS clouds will maintain internal key management based on digital signature concept. PKI is used for the API commands for gaining access for images and multimedia files. Here, the private keys must be stored by the user internally with the basic key management techniques [7].
In PaaS and SaaS clouds, the keys are managed by the cloud service providers. Private keys for accessing the important information or applications and systems can be handled by users of the cloud. Public keys can be shared in order to maintain the security, but any other internal key management can be managed by the service providers. In Hybrid clouds, keys are managed mostly by sharing and private clouds have tools to maintain the security of the data within the internal network of cloud.
This section discusses some preliminaries required for the proposed work.
Firstly, The service providers should explain the types of tools and products they have and the types of services that they are providing. They should also explain about the tools or products that help to maintain the keys and store them securely. The important key management infrastructure is hardware security infrastructure, which helps to allow a reasonable storage space with high performance key, accessing both operations like encryption and decryption.
Secondly, an organization need to enquire the service providers how keys are accessed and who can manage to access them. Keys must be in a safe and secure place and keys must not be controlled and managed by only one person who can maintain them. Key access of any cloud should be done jointly by two or more trusted and authenticated internal team members and must have a audit trail. When keys are lost at any cost, there must be an option to recover those keys. Recovery of keys is an important task while managing the keys. Many cloud service providers do not allow to recover the private keys under the control of the user. In this scenario, a user must request the cloud service provider in order to recover those private keys because private keys are the important keys for data in the cloud. Using only public keys is not safe for the important data in cloud because it never provides security for the data in the cloud.
Finally, there may be a chance of having multiple key access to the database or any application in the cloud. So, Service provider must provide the multiple key access facility and control each key. Service provider must provide an assurance that the keys are properly managed and each key is properly created, updated, and maintained.
In multi-user environment, each user have their own key to access the data and have the set rules to access the important data. Each key from each user is jointly managed. However, many service providers have an blueprint of maintaining the keys, one for each user. Management of those keys can be controlled internally by specifying the “access” patterns that should be carefully controlled and managed.
Now-a-days, the challenges of cloud key management are still a problem for storing sensitive data in the cloud environments. Cloud users and service providers are trying to solve this problem, however, key management is the major important area that needed to be focused on cloud security. With the help of authorized team and useful tools and services, we can easily manage the keys and store the important information in the cloud.
Organizations these days are going to migrate their most important databases and applications to the cloud without thinking of the security issues. With the concept of Cipher cloud platform and some security techniques, some of the security teams can encrypt the important information before it sends to the cloud. Cipher cloud platform provides a way for every organization to protect their important information before it sends to any cloud application by combining the concepts of tokenization, encryption, and some anti- malware activities [8].
Cloud can maintain and manage the encryption keys that are stored in the hardware. Service providers now have a solution that delivers high performance secure protection of cloud based applications. With this solution, the service providers can maintain the application functionality while the important data remains encrypted. These solutions have some of the capabilities which includes Key security: It is a key management platform which allows the service providers to manage the keys across different organizations. Next, HSMs are high performance appliances that maximize security among the data while the operations are done by the user. Finally, protect the application which offers the encryption and security of the data which is controlled by the enterprise applications. It provides the central key facility for large number of applications.
The majority of the service providers works on enabling the network encryption in default in order to protect the data. Most of the cloud service providers enable the encryption of the data which is not at use and helps to protect the files in the cloud. However, encryption of the data is only effective when the keys of encryption works properly and protected manually. When users move their data into the cloud, it is very difficult to manage and secure the encryption of keys.
Managing the encryption keys and maintaining the security of the important data in cloud is one of the difficult tasks for the cloud service providers when new organization is moved to the cloud. Multi-Cloud key management helps to overcome the problems which helps to select the right pattern to store the keys and manage them. This can also deal with creation of keys, where the keys are stored and managed, policies regarding how the keys are maintained, how to survive in dynamic environment, and how to integrate or migrate with each different cloud.
Symmetric key encryption uses the step by step approach. This process is useful for an encryption which has limited depths in hierarchies. The main security of the plan depends upon the pseudo codes. In this process, there is a center plan which can create useful keys for encryption inside the organization. So, owner can have the keys and he cannot depend upon the key manager who generates and manages the keys.
In Attributes based encryption process, cipher text is connected with attributes in the process. The main advantage of this encryption is that this process uses public key encryption and the size of cipher text is consistent and flexible. But, the major drawbacks are cost and storage space. It takes high cost of creating keys and it requires more space to store the keys.
For public key encryption, Identity based encryption is very important and flexible. Private Key generator is a trusted party in identity based encryption which has the ability to hold a master secret key. It can also hold the issues of the secret key with their identities. This encryption encrypts the plaintext not only with the public key, secret key, but also with more number of client identities. It is more expensive to transfer and store the keys in this type of encryption. All keys in this encryption is aggregated and that must originate from different identities [5].
We need to make the decryption key more flexible so that it can accept to decrypt the set of cipher texts. Data owner who manages to divide the files into classes, encrypts the data, and uploads the data in cloud interface. For any set of cipher text which data owner is about to share the information with others can send the information by doing aggregation to the key and the data. So, the user who is going to decrypt the key and the cipher text from the cloud interface only. For public key encryption, a class based encryption is used. Class based encryption does the work in three stages as shown in Figure 2, which is cloud server, data owner, and user. Data owner who can create keys public and master keys in the form of pairs. He can encrypt the file by public key and class through encrypted data. Data owner uses master secret key to create an aggregate key in order to arrange the cipher text classes. User can use the aggregate key and download the cipher text from cloud and decrypt the cipher text which contains that aggregate key in the particular class [10].
In the cloud area, the number of cipher texts increases quickly so that in order to control the cipher text, we are introducing the concept called class based cloud which can easily manage growing cipher text. We all know that information sharing is critical and important in cloud computing. We need to do the sharing very carefully by using encryption and decryption of the keys. Managing the keys is very important in terms of public cloud areas. In public clouds, all the information which is very important is visible to everyone so care should be taken not to copy the data and also to protect the data from frauds [3].
Cloud service provider plays a major role in information sharing. If he is trustable and loyal, we can share our information in cloud. Data loss need not be hiden from the user if there is a huge amount of loss for the user by trusting the servicer providers. Many cryptographic techniques are introduced in order to solve this problem. But all these techniques are not concentrated on cost optimization and storage issues. When a user A wants to send the data to user B, are several issues need to be identified, those are: A needs to encrypt the data before sending to B using one key and can share the corresponding decryption key to the B. The main issue here is data not meant to seen by B can also be visible once it is decrypted because all the data is encrypted by using only one encryption key. So, considering this issue, A can encrypt the data with different encryption keys and each can have its own decryption key. The problem with this method is sharing many decryption keys with their transmission and storage problems [5].
In this scenario, the decryption key allows more decryption of multiple cipher texts without considering or increasing the size of the data. In this the cipher texts are divided into different classes. Each class can have an identifier of the cipher text. So, the user can encrypt a message not only by a public-key, but also under the cipher text class in the cloud. The key manager has the master secret key by which the data owner can extract the keys and then create an aggregate key that can be considered as secret key for one class in a cloud [1].
The main advantage of this approach is the delegation of the decryption key that can be implemented through the aggregated key. The decrypted key is of fixed size and it also results in very large number of cipher text. It makes the key management very easy and also reduces the issues of storage and cost optimization.
A decentralized access control scenario with aggregate key encryption for storing the data in cloud has been introduced here. Many contributions are done here, those are: Accessing of cloud data such that only the authorized users allowed to do so, Authentication of users, Key management for important data, Encryption and decryption process of cloud data. Key management can be done managing the keys into the form of a tree so that we can eliminate key accessing problems. The data owner is allowed to classify the classes in the cloud that can be modeled as a graph. In that graph, intermediate node indicates the class. A user wants to use a particular class through deriving the keys from the parent or root class.
In class based cloud storage, data owners can allow to select users to view their private and important data. But the problem here is how to effectively maintain and share the private data to the specified users. In the existing system, there are many problems like: cost of sharing and transmitting the data, maintaining the cipher text data, increased storage cost, and cost complexities are increased. Limitation of predefined number of cipher text classes makes this scenario difficult. Since many of cipher text classes increases, preserving enough of cipher text classes is required based on the cloud data.
A decryption key has been made more flexible so that it can allow many cipher text classes. Many cipher text classes does not increase its size while converting into the decryption key. Firstly, the cipher text classes are divided with the identifier of the class. Thus the encryption is done by the user using not only the public key, but also using master secret key. Master secret key can be created by extracting the number of different classes that will be converted into an aggregate key for decryption. This can be used as a secret key for single class in cloud.
In the proposed scheme, the setup algorithm takes security level parameter as input and produces parameters like public key and master key as output. Encryption key algorithm takes public key and master key as input and produces cipher text class as output. Encryption algorithm will encrypt the message in the cloud and produce cipher text such that only the user who knows about the cipher text class can use that to decrypt the message or data in cloud. Key generation is an another algorithm in order to generate the keys for the data present in the cloud. Key generation algorithm takes master key and some of the attributes as inputs and produces private key as output. Finally, Decryption algorithm takes all the public parameters as input including that a cipher text that contains a policy and private key of the attributes which in turn returns the message in the cloud.
When a cloud user wants to send an important information to the another user in the cloud he can create a cipher text class which contains the selected information in the form of encryption data. During this process, the aggregated decrypted key is generated with the help of cipher text class. When any other user receives the cipher text class, he can also decrypt it by using aggregate decryption key which is created by the public key, master key and the identifier of the cipher text combination.
Mathematically, when a user enters into the cloud, an AES key and RSA key pair is generated for him. When the user wants to share a selected content to the another user, each file is encrypted with an AES key before uploading the file into the cloud. These files are added to the cipher text class. While sharing these cipher text class to another class member, he can use his RSA public key. Using these keys together with the file identifier of the cipher text class, one can decrypt and download the files from cloud.
As we can observe from above Figure 3, Class based cloud computing gives user an unambiguous way to share files among classes because cloud is classified and maintained into different classes. This makes easy to exchange files to another classes or clouds easily without any confusion.
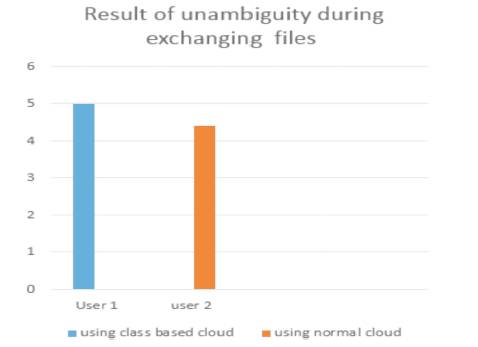
Figure 3. Exchanging Files in Class based Cloud
As this concept is technically new in the world of class based cloud computing, this paper explains about how to efficiently manage the keys for cloud which is divided into classes. This paper explains the main idea of managing keys in the conceptual way. As further discussion, we can implement the idea of this paper in many sectors as big data is also a booming concept these days. So, using this concept, we can apply the technique into different business sectors to manage data efficiently as well as secure the data by dividing into classes which helps to reduce unambiguity.
Cloud technology has evolved as a best storage space to store user data. A cloud is a separate storage area, where user or data owners can safely store and can use their data at any time. Today cloud computing is a more popular application and service. Though cloud computing is comfortable with its services and applications, it is facing some of the problems regarding integrity, trust, and security.
Normally in cloud computing, the data is maintained by the user in the cloud. Cloud server can maintain the data present in the cloud. In class based cloud data, different classes were divided based on domain. Maintaining each domain data in separate classes is one of the advantages.
The main disadvantage of cloud is maintain the keys while it may be for encryption or decryption. Class based cloud computing is undoubtedly one of the best enhancement techniques for cloud computing where cloud is divided in different classes. Key management for each class is one of the biggest issues.
This paper presents a scenario for maintaining keys for class based cloud data. A decentralized access control and aggregate key encryption scenario was also implemented here.