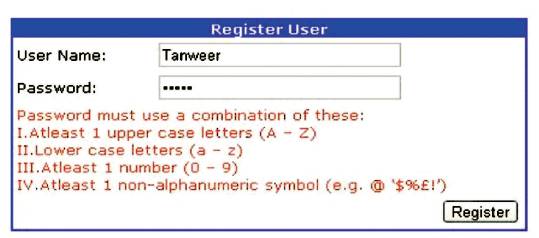
Figure 1. Complexity of Password
In the current digital technology world, all the applications are moving into cloud environment. The biggest challenge is to maintain the security and privacy of the application in cloud. One of the basic security features that normally applied in any application is Authentication of Users using valid user id and password. Authenticating users only on these two parameters will not assure that the user who had entered these details is an actual user. Recently most of the applications are using two factor authentications (OTP's) over the user id and password. In cloud computing environment we can use different authentication functionalities depending upon the customer requirements. In this paper we will explore eight authentication functionalities and discuss their pros and con's in implementing them in the applications. For strong level of security, two or more functionalities can be combined and implemented in the application to validate the credentials of the user.
Authentication is the process of validating the truthfulness of each user's identity, to prevent unauthorized user to access the System/applications or its data. Each user need to enter the valid user id that is given or created at the time of registering and password to login in to the system. This process is done each time a user logs in.
Adaption of Cloud computing has increased drastically in all industries. All the applications are migrating into the cloud based applications. The major service that is always focused by the customers is security and privacy. Privacy of information through authentication is being considered as imperative. Providing security requires more than user authentication with passwords or digital certificates [1]. Customers can get trust in cloud vendors if they address how they are handling the user's action/activities in the cloud. This raises the question of privacy of data when sharing the data in the cloud environment.
Privacy means protecting user information from intruders. A privacy breach is not acceptable in cloud environment, it may lead to a great loss to the cloud vendors. Privacy control allows the person to maintain a degree of intimacy [2]. Privacy is one of the aspects that need to be dealt in cloud computing, both in terms of legal compliance and user trust, and privacy needs to be considered at every phase of design [3].
Users must guarantee for feeling that privacy of data has been ensured in cloud environment [4]. One of the processes to ensure the user about the privacy of data is through multiple levels of authentication.
General authentication procedure may be prone for attacks and easily hacked by the hackers. If multiple levels of authentication is used it makes more complex for hackers to decode or hack the user identity.
In the next section, the different authentication functionalities that can be used for validating the user's identity have been discussed.
The following functionalities can be used for authenticating user's identity and assuring that only the valid user is using the system/application.
1) Password policies
2) CAPTCHA
3) Two Factor authentication (OTP's)
4) Image selection
5) Questionnaires
6) Grid based
7) Setting Network restrictions & login hours
8) Session Security.
The basic element of any authentication procedure will be password. The password must be very strong so that it should not be hacked or guessed easily. As many of the users are novice, they tend to keep the password simple and those can be predictable or hacked using trial and error method.
To make the password strong and secure for all the users, the administrator can impose some constraints while creating the password. As an administrator, he can create password policies, lockouts, expiration times, reset procedure, etc.
The following are some of the password requirements in the password and login policies that can be used to make the password strong.

Figure 1. Complexity of Password
Figure 2. Number of Invalid Attempts
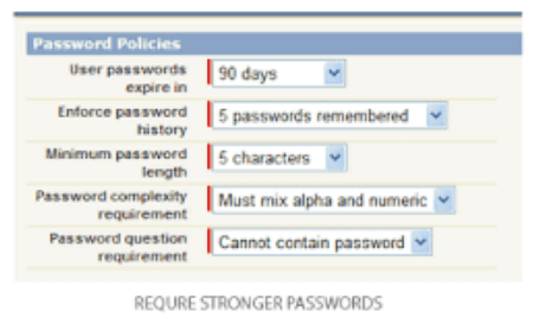
Figure 3. Login Policies (from salesforce.com)
CAPTCHA is a type of security which is used in network based system. It stands for “Completely Automated Public Turing test to tell Computers and Humans Apart”. It is a text-entry validation that helps in preventing malicious programs from getting access into the system. It also reduces the risk of automated attacks done by hackers. To pass the CAPTCHA test, users must type the text displayed on an overlay's text box field, if the entered text is matched with the text that has been displayed, user gets the access into the system or else user is assumed to be invalid. This technology is provided by reCaptcha to verify that the text is typed by person, as opposed to an automated program. Figure 4 shows the sample CAPTCHA codes.
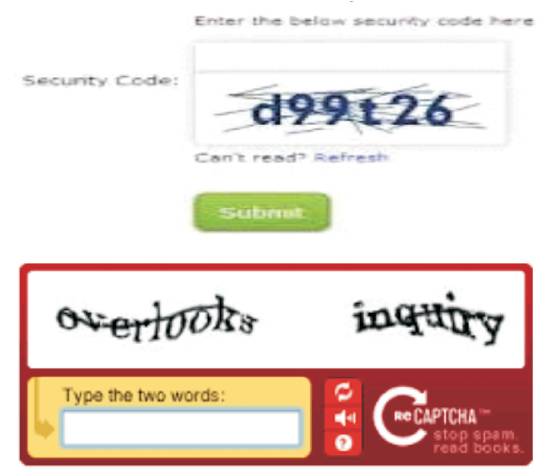
Figure 4. Sample CAPTCHA Codes
In the present trend most of the transactions are done through digital mode. Transactions such as banking, retail orders, transportation, etc. and doing transactions over a digital medium has become a natural phenomenon; this has brought huge challenges to the organizations that are providing the services. Stakeholders are expecting transactions to be secure and provide privacy for their data.
Secure Logins with a Unique Code (Two-Factor Authentication- TOTP has come in to picture; it has been used as one of the authentication level in doing the transactions. OTP has gained huge popularity and almost all applications are using OTP as additional level in authentication process.
One-time password is a key value pair that is created every time a user logins or requests any transaction which require valid user authentication to complete the transaction[7]. OTP are used only for digital systems and these are valid only for one transaction or login session. OTP's are incorporated in a number of applications and also used in two factor authentication.
By implementing authentication, it can ensure that system's resources are not obtained fraudulently by illegitimate users [5].
Various approaches are available for generation of OTPs, some of them are:
Figure 5 shows the sample OTP generated for a transaction.
There are some electronic security tokens that are used to generate OTP's such as gadgets with small display, these gadgets are embedded with software to generate random tokens and these tokens are already liked with user in the application servers.
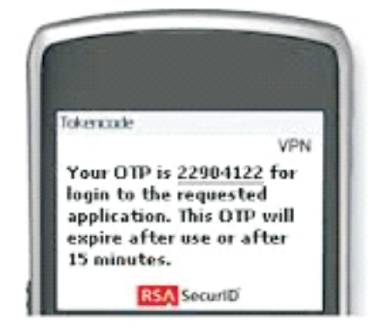
Figure 5. Sample OTP Message
Other systems consist of software's that runs on mobile phones, and some systems generate OTP at server side and send them to user using SMS messaging. And some systems earlier used are OTP's printed on papers.
Using OTP alone is not safer; it must be used in combination with a password or any other user identity functionality. In general, one-time passwords are representation of two-factor authentication (2FA) or (T-FA). It forms an extra layer of security, where attackers cannot hack the application with just user password or using only one type of attack. One-time password technology is often used with a security token.
As text-based passwords continue to be the dominant form for user identification today, services try to protect their customers by offering enhanced, and more secure, technologies for authentication[6].
Administrator can enhance security in authentication with 2FA as second level for every login. We can also set 2FA as requirement for certain criterias, such as attempting to do financial transactions in banking applications.
The advantage of OTP is generating dynamic password in contrast to static passwords, and these code cannot be used for replay attacks. Even if hackers or intruders capture an OTP that was already used for some transaction, that same OTP is not valid for other transactions, so they cannot use it again, since it will no longer be a valid OTP. OTPs has become mandatory for almost all transactions which are done through online or digital medium. Every person is equipped with a digital gadget which can receive text messages and also these have replaced to remember the password to login into the systems.
Considering the cloud based application that is implemented on Salesforce, when user logs in, Salesforce considers the geographic location and browser of users. If they're not recognized with the last time login, Salesforce prompts the user to verify the user identity by using the highest-priority verification method available for that user. Figure 6 shows the 2FA verification process. The following is the order of priority for verification methods.
1. Verification code is sent via SMS to the user's verified mobile device.
2. Verification code is sent via email to the user's email address.
The user enters the code as a secondary verification of their identity. After verification, the user doesn't need to provide this information again, unless they log in from a browser or location that isn't verified by Salesforce.
In addition to user id and password validation, another level of security is applied using the images and text associated to the image. It will make the system more secure to the users. The user identity is validated if user enters valid user id, password, select image related to user and the message associated to the image as shown in Figure 6. This multi level authentication will make the application more strong and secure. It prevents the hacker from predicting the image and text associated with the user identity.
Figure 6. 2FA Verification Process
Image and text mapped to image can be selected at the time of registration. Application will have a set of images in their database, among those images the user needs to select one of the images and type the text which will be mapped to the selected image. The text entered will be known only to the user who is registering for the first time. Later if the user wants to change the text or image, he can do after the login. Figure 7 shows how users are validated using image and text.

Figure 7. Image and Text used for Validation of User Credentials (from HDFC Bank)
In order to protect the information and ensure that only valid user is accessing the account, an additional level of validation is given, i.e., answering security questions. Set of security questions are created at the time of first time registration of a user account. The user needs to select some security questions from the predefined set of questions and answer them. Select the security questions that are difficult to guess and easy to remember.
While validating the user, application will prompt one or more questions from the selected list of questions each time user the wants to log in into account. Figure 8 shows how security questions are created. Figure 9 shows identity validation by prompting one of the questions to get access of application.
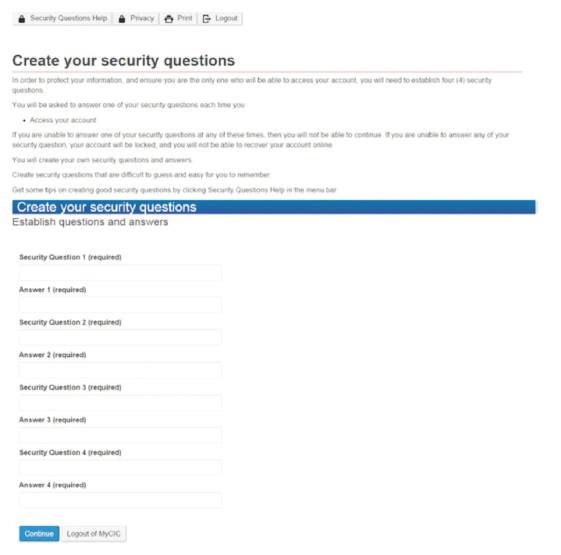
Figure 8. Create Security Questions (from cic.gc.ca)
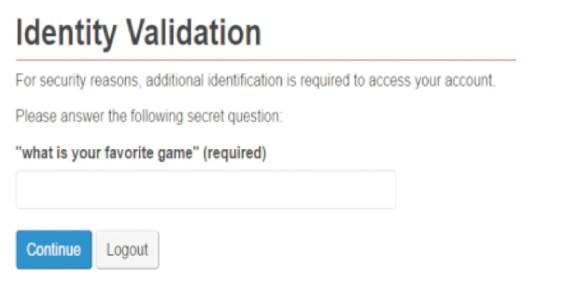
Figure 9. Identify Validation using Security Question
We can prevent the frauds at the initial stage itself by using more levels of authentications. One of them could be a Grid based authentication. Each user is allotted with a grid as shown in Figure 10 after successful registration. Each grid has a set of alphabets and two digit numbers are paired for each alphabet. Each time the user wants to login into the system, it prompts randomly three alphabets among the grid and the user needs to type the associate.
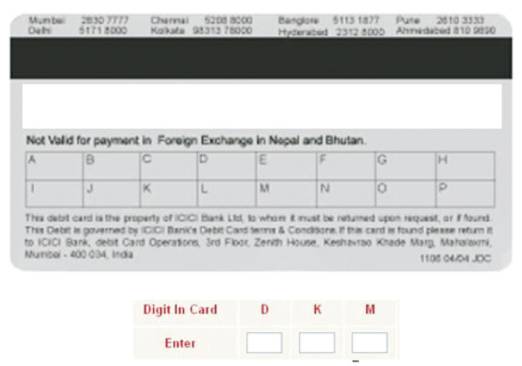
Figure 10. Grid Card (from ICICI Bank)
The procedure for authentication is as follows:
Step 1:The customer submits his/her credentials along with the respective Grid Characters on the grid card associated with the user account. Like A =21, B= 66, C = 35 ……..
Step 2: Application receives the secure transaction information along with the Grid codes and passes it to the authentication process.
Step 3: The user is valid or invalid based on the user's authentication credentials and grid card.
The above steps completes in about three seconds or less!
In Grid Based approach each user is associated with a Grid Card. Without the Grid Card, no one can login into the application. It helps in getting rid of intruders and hackers.
In general, the fraud or attacks on the systems will not be done within the organization. Attackers use different desktops/ laptops to get accessed into the application by getting the credentials of the user. In order to restrict the attackers from using the application, we can add extra credentials to the user in terms of enforcing login IP range in network and login hours.
For each user if we set the Login IP Range addresses from which users can login. Users outside of the Login IP Range set can't access the application. Along with IP range for users, we can also set trusted IP ranges from which users can access the application. Figure 11 shows the list of trusted IP ranges.
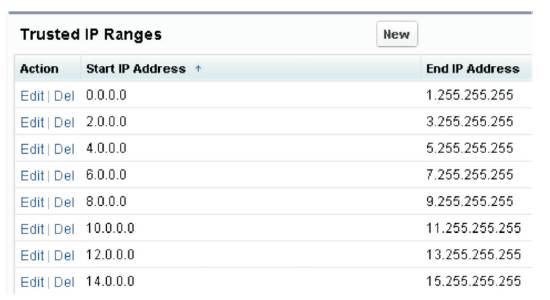
Figure 11. Trusted IP Ranges for Application
The IP restrictions can be done in two ways
Figure 12 shows how to set the IP ranges. For a single IP address, we need to enter the same address in both fields. For example, enter 128.23.3.0 as both the start and end addresses to allow logins from only single IP address. IP addresses ranging in both start and end address must be either IPv4 or Ipv6.
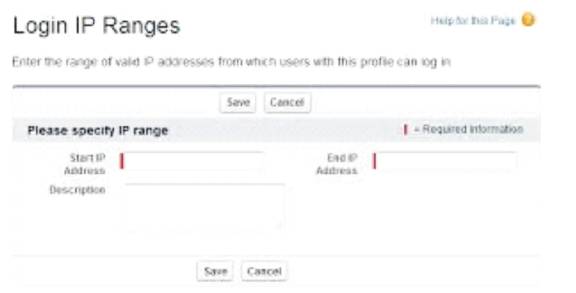
Figure 12. Setting Login IP Ranges
The process of authenticating a user using IP address range is shown in Figure 13. Assume a user logs in successfully from an IP address defined in Login IP Ranges. If user moves to a different location and has a new IP address that is outside the Login IP Ranges. When the user refreshes the browser or tries to access the application, the user is denied.
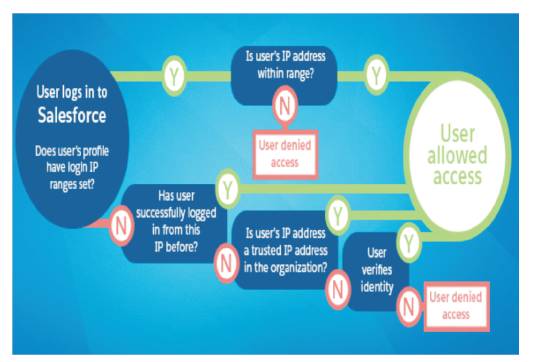
Figure 13. Authentication Process using IP Ranges
Advantage of using restricted IP range is that the users always log in without receiving a login challenge. These users can log in to your organization once they provide the additional verification.
We can even set the hours when users can login; this depends on the type of role and responsibilities the user is handling. We can restrict the user login by days and hours.
We can even set for specific day, set the start and end times to the same value. The Time Zone need to be updated depending upon the users’ geographical location. Figure 14 shows how to set the login hours restrictions.
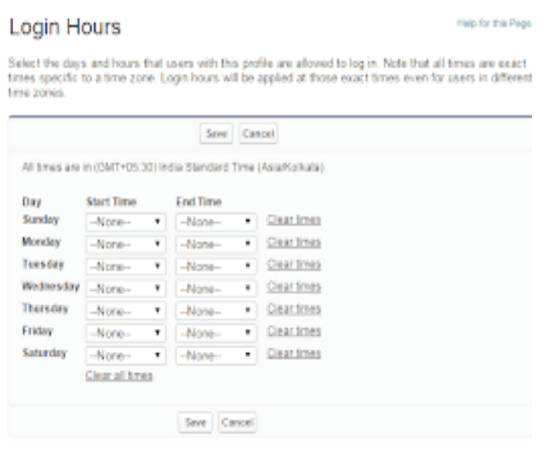
Figure 14. Login Hours Restrictions
If users are logged in when their login hours end, they can continue to view their current page, but they can't take any further action.
Even if user identity is validated, still we can validate the identity at every stage of application through sessions. Session and cookies can be used to record the authentication information for the duration of a specific session. The details are recorded in encrypted form and it doesn't include username and password. Instead a dynamic data in encoded form is stored, that data is called as SessionID's. This can be used when users leaves their computer unattended while still they are logged in. It also limits the risk of internal attacks, such as when one employee tires to use another employee's session.
The above discussed eight authentication functionalities Have both advantages and limitations in implementing them. The generic limitation would be an added functionality takes longer time to validated the credentials when compare to general login procedure.
If the password is more complex, the application will be secure as it is not easy to decode or to predict the password combinations even by applying different algorithms.
Difficult to remember the password with many combination of characters.
Reduces the risk of automated attacks done by hackers.
Sometimes the text displayed is not clearly understood and so should retype it. It takes a longer time to load the CAPTCHA image if the internet bandwidth is slow.
An OTP is sent to email and mobile phone, this service also make the users aware that he/she is trying to login into the system. This makes the user to take a proactive step in order to avoid attackers to get control of the application.
Asynchronous mode of communication is the biggest drawback of this functionality. If the OTP is not received due to some communication fault, then the user cannot login into the application.
Increasing the level of security by taking too many inputs from user in order to identify valid user.
The advantage itself becomes the limitation sometimes because humans tend to forget the text or image which has been opted while registering the account.
Answering random questions every time the user want to get access makes the system more secure. This process cannot be automated by the hackers.
User needs to remember the set of questions and the answers related to them.
It helps in getting rid of intruders and attackers as the grid is unique for all users.
Every user should have an associated Grid card which makes the user inconvenient at the initial stage. If Grid card are lost, then there is a chance for the frauds and the process to generate a new card takes some time.
Assuring that users are logged into the applications from trusted networks and even restricting the user's access depending on the roles and responsibilities.
If user frequently travels to different locations and works in different time zone, we need to change the settings every time.
A stealth process will be running behind the browser which keeps on checking for the user's credentials. It also limits the risk of intruders and attackers.
Session IDs are stored in cookies; this may provide some sort of useful data for the attackers.
Here the authors consider the Salesforce environment for testing some of the authentication functionalities that are mentioned in the section 1. In Salesforce, users log in to application, either via the user interface, the API, or a desktop.
Salesforce confirms that the login is authorized as follows:
Whenever a login is blocked, Salesforce verifies the user's identity by prompting to enter a token (also called a verification code) to confirm the user's identity. A security token is an automatically generated key from Salesforce. For access, users must combine their security token with the passoword to log in. For example, if a user's password is ‘mypassword’, and the security token is XXXXXXXXXX, the user must enter mypasswordXXXXXXXXXX to log in [8].
Protecting the applications from intruders and attackers require a prevention approach rather than detection. Applications need to provide strong authentication process. It can be achieved by applying multiple levels of validations at the entry point of application itself. Instead of checking only username and password credentials, we can opt for one of the eight validation functionalities that are also associated with the users’ credential details. This make the application more secure and also restricts the attackers and intruders from hacking the user accounts due to complex authentication process.