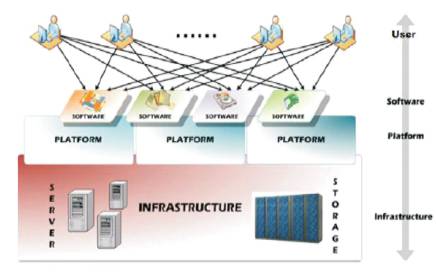
Figure 1. Architecture of Cloud Networks
Now-a-days Cloud Computing has become more popular in all Information Technology areas. Cloud computing provides a number of services like Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). All these cloud computing models share common resources with different customers to provide services. To provide services to the customers, cloud computing uses a technique called Multitenancy. When cloud uses Multitenancy to provide services, there are so many data and security problems. Cloud security is becoming a major issue in adopting the cloud, where security is considered as one of the major critical concerns for the large customers of cloud. Multitenancy is a technique of sharing resources of cloud commonly across different customers. In SaaS applications, same database is shared by different users. If a common database is shared among different customers, there are chances for so many data related security issues like data loss or leakage, Account or session hijacking, etc., to occur. In this paper, the author has proposed solutions for the problems that occur in cloud computing models with Multitenancy by implementing secure key mechanism using Software Defined Networks (SDN) in the cloud computing service model.
The term cloud computing is used as a symbol for the Internet, based on the standard use of a cloud-like shape to denote a network. A cloud computing is referred by a combination of networks, hardware, storage, interfaces, and services that helps in delivering the service of cloud. Cloud computing is a model for enabling on-demand convenient network access to a pool of shared computing resources that can grow provisioned and released with minimal management effort or service provider interaction. The cloud computing platform provides on demand services that are always available to the customers of cloud. The Architecture of cloud computing is shown in Figure 1.

Figure 1. Architecture of Cloud Networks
Providing security in cloud computing models is very difficult because of the wide utilization and availability of cloud resources. Cloud Computing resources are used by more number of users at any point of time and anywhere from the world. So the user may be a registered user or hacker. In case if the user is a hacker then they are always trying to hack the data of other users. In cloud computing SaaS model resources are shared by different customers with Multitenancy architecture.
In cloud, customers utilize the concept of “pay-per-use” for applications, storage resources and computing. Along with the pay-per-use concept, the scalability in upgrading or downgrading resources makes cloud computing a popular model for organizations. The cost effectiveness of cloud computing is encouraging its adoption; enterprises requiring a high level of scalability and about to decide whether to build up their own IT infrastructure or utilize cloud computing infrastructure, which may find that a cloud infrastructure will give a better computing balance between cost and scalability. Basic essential characteristics of Cloud computing is sharing of cloud computing resources of a shared data center by using virtualization mechanism, elasticity along with Ondemand and Pay-as-you-gO.
There are so many benefits with the cloud computing come along challenges to the model. One the most challenging issue of the cloud computing is security; Security refers to providing security for cloud data from unauthorized disclosure, use, disruption, access, modification, inspection, recording or destruction. A study done by a Cloud Security Alliance (CSA), reports there are seven most occurring threats that companies will face in adopting Cloud Computing [1]. They are Shared Technology Vulnerabilities, Malicious Insiders, Loss/Leakage, Account, Abuse and Nefarious use of Cloud Computing, Insecure Application Programming Interfaces (API), Data, Service and Traffic Hijacking, and Unknown Risk Profile. There is another study made by Gartner has also found seven Cloud Computing security risks, viz., Business Continuity and Disaster Recovery, Regulatory Compliance, Outsourcing Services, Data Location, Shared Environment, Difficult for prosecute Illegal Activity, and Long Term Viability [2]. The threat of data compromise increases in the cloud, because of the increasing number of customers leading to an increase in the number of points of access [3].
Software Defined Network (SDN) is a technology that implements more security for the Cloud Computing Databases. Software Defined Networks is a new way of seeing the network like how it is configured, functionality of the network and the way how it is operated. Software Defined Network will also provide more security by using firewalls. It facilitates indirect checking of security violation. By mixing up both cloud computing and Software Defined Networks, it provides more reliable security mechanism for the cloud customers and cloud data.
Multitenancy in cloud environment has been identified as a security risk by many researchers who conducted several surveys on cloud security risks in service delivery models and declare that Multitenancy is a major cloud security risk that leads to confidentiality violation [3],[4]. In addition, Wayne A. Jansen recognized Multitenancy as a new source of threats in cloud computing environment [5]. The view of David Teneyuca links between Multi- Tenancy as a form of shared environment and the interest of malicious activities in the clouds [6]. Intel IT center generates a research document on best practices of Multitenancy in cloud security risk in shared resource environment of cloud computing model [7]. Verizon Team proposed a layered security risk approach in virtualization mechanism implementing a common resource shared by multiple customers so it is the effect of Multitenancy [8].
Prasad and Ben refers that there are different areas found that are dangerous in cloud; In the governance of data, the writers highlighted that Multi-Tenancy Preparations in Cloud are raising questions about data isolation. While NIST prepared a report titled “Guidelines on Security and Privacy in Public Cloud Computing”; they identify that Multi-Tenancy is concerned as a security and privacy risk in the Cloud [9]. Again in [10], Multi-Tenancy is identified as one of the security issues.
Cloud Security Alliance (CSA) released a note titled by “Security as a Service” [11], where they tried to define types for services; they raised the question “How does one assure data isolation in a multi-tenant environment?”. Also, CSA in the same note stated that Multitenancy creates new ways for malware. Ruoyu Wu, et al. [12] stated that to determine the challenges of security and privacy in Cloud Computing; Multitenancy is identified as one of the unique implications of privacy and security in Cloud computing. In the same way D. Miloiicic [13] stated that Multitenancy is a major characteristic of Cloud Computing and a major direction in the Cloud security problem that needs a solution from the Infrastructure-asa- Service (IaaS) up to Software-as-a-Service (SaaS). Augusto [14] highlighted that Multitenancy may lead to information leakage and increased attack surface which affects the security of the Clouds. Also, [15], [16], and [17] considered Multitenancy among the serious issues in Cloud security.
Grandl, et al. [18] defined a system called Harmony that organizes aspects of storage, compute and networks for Software-Defined Cloud computing (SDCs). They proposed an architecture that considers these elements and also by taking security of data in cloud computing models. Baset, et al. [19] discussed how the concepts that compose SDCs can be leveraged to achieve efficient error recovering and improves understanding of what constitutes regular system operation a feature authors call “operational excellence”. The proposed system focuses on high level features that enable operational excellence, and therefore it complements the features proposed by their architecture that enable the realization of the concept of SDCs.
Multitenancy is a sophisticated technique to achieve economic growth in cloud computing by implementing virtualization and allow sharing of common resources [5] , [9]. As stated previously, multitenancy refers to the sharing of common resources in cloud environment, but it is still general in the context of cloud computing because cloud computing looks differently with different cloud computing models.
In the view of a Software as a Service Model, applications are provided as a service by the Cloud Service Provider (CSP); Here the users cannot view or monitor the low level infrastructure. In this context, multitenency means that more than one user utilizes the same type of applications provided by the CSP without referring low level resources [7]. In the same Infrastructure as a Service customers uses different services like storing, computing and networking resources and can control, but cannot manage low level infrastructure; Here two or more virtual machines share a common resource by using the concept called multitenancy.
Multitenancy has more benefits like over provisioning of resources, Separate hardware failure from the software; Easy of Management, Reduce power consumption and it maximizes the utilization of resources. Providing multitenancy increases the utilization of resources by sharing single service or application with more number of customers and it shares a common infrastructure like database, network resources and computing power. Managing the hardware and software infrastructure in cloud is simple because a single resource is shared by more number of customers. It reduces the power consumption by providing multitenancy model in cloud and it does not affect the working of software service even if the hardware failures occurs in cloud computing because of multitenancy feature.
Resource Sharing + Virtualization = Multitenancy
Multitenancy brings various bickering in cloud computing that software developers feel that it is a good opportunity for development and utilization of software resources. In the case of security, experts feel that it is a bad thing with respect to vulnerability [20], [21], [7], [9]. Eric Keller, et al., [21] describes that by eliminating virtualization, multitenancy is avoided in the cloud. Prasad, and Ben [9] suggested that the cloud service provider should disclose the risk of multitenancy to the cloud customers and do nothing. The first technique seems good but it removes the vital benefits to the cloud providers like Virtualization and Economic gains through resource sharing. By implementing Virtualization, the providers can relocate Virtual Machines to improve the resource utilization. Other hand second technique does not improve the cloud security to the providers as well as customers specifically the enterprise users invest money to implement their own security concerns even though they are using cloud computing [4], [5], [12].
In cloud computing multitenancy environment, both the attacker and customer use the same server infrastructure. This type of techniques may lead to security issues simply because penetrating inside server and monitoring techniques are very limited [12], [14].
Figure 2 describes the normal attacks in the internet. Here both the attacker and victim are normal internet users; To provide security against such type of attacks, they use traditional security techniques and efficient devices.
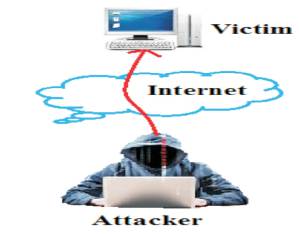
Figure 2. General Attacks in Internet
In Figure 3, both the Victim and Attacker are in the same cloud service provider environment, but each one placed in a separate server. This type of environment is provided to utilize virtualization mechanism in cloud models. To provide security in these type of networks, cloud providers implement network security models and techniques in cloud computing [14].
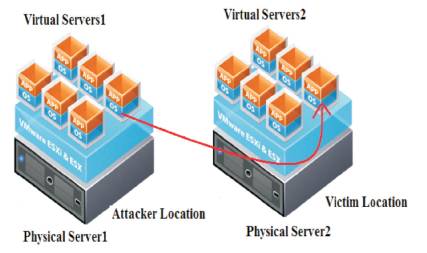
Figure 3. Attacks within the Cloud Provider
Figure 4 describes that both the attacker and victim are customers of same cloud, placed in the same server. This situation occurs due to implementing multitenancy in the cloud server. Providing security in such networks is not an easy task because of communication between the attacker and victims’ virtual machines are limited within the physical machine.
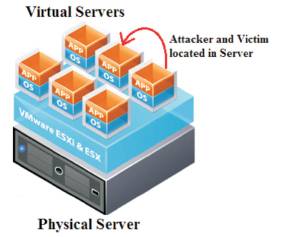
Figure 4. Multitenancy Attacks
Software Defined Networks (SDN) is a way of providing low level operational functionalities to the administrators. SDN Architecture is a manageable, dynamic, adaptable, cost-effective, making it ideal for the high- bandwidth, dynamic nature of today's applications. SDN Architecture has been illustrated in Figure 5. SDN Technology decouples the network control and forwarding functions enabling the network control to become directly programmable. It abstracts the underlying infrastructure for applications and network services. To build solutions for the SDN Application, OpenFlow is a fundamental protocol.
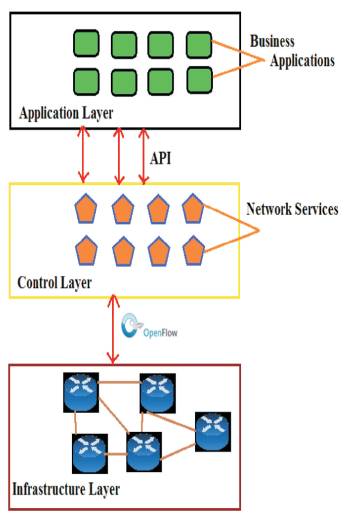
Figure 5. SDN Architecture
SDN Architecture is directly programmable because it decouples the forwarding functions. It provides agile free technology by providing the controls to the administrator for adjusting the network bandwidth to meet the wide network traffic changes. By implementing applications through programs it provides the network manager functionalities like provide security, manage, configure, optimizing network resources in a dynamic way and automated dynamic programs which they can interpret without depending on any proprietary software.
SDN provides network intelligence for logically centralized control to maintain a global view of the network and it appears as a single logical switch. It is implemented through the open standards so it simplifies the design and operation of the network because instructions are provided by SDN controllers instead of multiple vendor specific protocols and devices.
In current section, the proposed model and Attacker Model schemes are discussed. Figure 6 demonstrates the working process of system model for avoiding the multitenancy problems in the cloud computing SaaS model by implementing SDN network controllers.
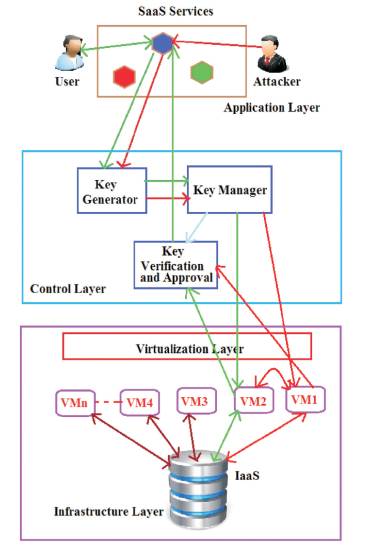
Figure 6. Proposed System Model
In the below diagram, top layer denotes the application layer and SaaS services where the users are logged in and access the services of the cloud computing. In the middle layer specifies the Control layer which contains functionalities like produce secret key, Key Management and validation of the key. Last layer is infrastructure that contains all hardware components of the cloud like Memory unit, CPU, etc.
In the proposed system model shown in Figure 6, the first layer contains all the services (SaaS) of the cloud and these services are accessed by different users. Normal users and the attackers both are logged in the same service by registering with the service in the same layer to access the services of the cloud that implements multitenancy technique.
In the second layer, it contains three modules for key management to organize the users and to grant access to the users. First module is key generator that contains the logic to generate unique keys by using secure random AES key generation algorithm for the user account and the virtual machine that is accessed by the cloud users. Second module is Key Manager that maintains a database of all active uses and secure keys of the user and the virtual machines. Third module is a key verification and Approval module that performs the validation of the user keys based on the virtual machines accessed. If the user attacks any other virtual machine within the same hardware to access the data of another user, then the verification module identifies the attacker and blocks the attacker from accessing the data. This is the main theme of the proposed system to avoid multitenency issues like data leakage or data losses, unknown risk policies, account or service hijacking, Shared technology issues, Malicious insiders, etc.
Third Layer contains the infrastructure of the cloud by implementing virtualization mechanism. When the user is logged in for accessing any service, automatically the virtualization mechanism creates a Virtual Machine for the user dynamically. For all the users it uses a common database to store the information of the users. In cloud computing, if one service use a multitenancy technique, it creates one table and that table is shared by all the users commonly by creating one id for each user. In this proposed system, first the authors provides access to all the users and rejects the attacker at the time of backing the data.
The Attack model used in the discussion is based on one of the scenarios utilized by Prasad, and Ben [9] to expose data leakage in Amazon EC2 public cloud. The behavior of data security for a defined vulnerability is that there could be a more number of attacks to exploit [9]. One successful attack against a system will analyze most of the possible vulnerabilities that can be utilized. These attacks vary in the sense of their behavior; for example, it is easy to identify any Distributed Denial of Service (DDoS) attack and any attack consisting of port scanning due to the sudden increase in traffic of the cloud. Also, it is easy to identify viruses due to their unique signatures; whereas it is very complex to detect iFrame attacks. An iFrame attack is an attack where an HTML code is inserted inside another HTML document as a frame in order to collect credit card information for instance.
The following are the list of attacks that could be used efficiently over the cloud infrastructure:
A side channel attack is any type of attack depending on data gained from the physical implementation of a system. There are different types of side channel attacks known in the field; some of the well known side channel attacks are power consumption attacks, timing attacks, and differential fault analysis.
Brute forcing is an attack mechanism applied over any type of attacks. This is one of the easiest method in order to build an attack, yet one of the most commonly used methods. For example, if an attacker wants to find out a password of a system by utilizing a brute force method, the attacker will try every possible combination until the correct password is found. Therefore, brute forcing can be stated as running an attack operation multiple times until a successful breach is achieved. Brute forcing is considered as one of the most used top ten attacks by the Data Breach Investigations Report (DBIR), where it forms 22% of the total data breach attacks [8].
It is a method used to find out the physical topology of a network that consists of servers and IPs connected in the network. Such data can be found to identify possible targets and to implement an attack for a subgroup in the network.
Multitenancy is a risk factor then we need to choose one of the well-known risk management techniques in order to manage and minimize its bump. These strategies are as follows:
Although, avoiding the risk is considered as the most efficient methodology as stated previously, most of the benefits are linked with multitenancy, where it is not possible to apply it on multitenancy.
To avoid risk of multitenancy, we need to remove the implementation of multitenancy in cloud. As defined earlier, multitenancy is a result of combination of the techniques like virtualization and resource sharing. In order to eliminate the multitenancy, we have to eliminate virtualization or avoid resource sharing mechanism in cloud computing. In either case it is not possible because most of the cloud computing advantages are linked with these techniques.
Multitenancy allows the benefit of resource sharing mechanism. This case is valid because of the side channel attacks defined as taking the benefit of the physical characteristics of the system. By the nature of side channel attacks, unlimited in number and time, it is not possible to eliminate all the attacks. However handling the known side channel attacks is very difficult because of their different form of side channel attacks. As discussed by Francisco Rocha, et al. [22], where they proposed a system to deal with shared memory attacks and they reached goal, but it is dependent on hypervisor and it works only on Xen hypervisor.
Another type of attack is timing side channel attack and Peng Li, et al. [23] proposed a method to eliminate three forms of side channel attacks. If they eliminate all timing side channel attacks, but it occupies 2/3 of cloud service provider infrastructure, the solution provided will not avoid all timing side channel attacks. By considering above two examples, it is very expensive and hard to eliminate all the side channel attacks. In some cases, two types of side channel attacks have relationship where it is not possible to avoid in the same time [10] that is if the side channel attack A is eliminated then the side channel attack of B is not possible to eliminate. If attack A is avoided, then B is a Success. So we cannot eliminate side channel attacks by eliminating major features of virtualization and resource sharing. So eliminating the risk method is not possible and it is not applicable when it deals with multitenancy.
Second method is mitigating the risk, where we try to balance between advantage offered by multitenancy, security and other factors like performance and cost. Figure 6 describes that without loss of any benefits of multitenancy, we avoid a risk. Here first it allows the risk by means of attacker and it blocks the attacker in the control layer by checking their security key of the virtual machine and the user what they accessed the database. Third method is transferring the risk from one CSP to another CSP having risk handling capabilities. But it is not a fair mechanism to handle the risk. Because no one accepts that the things have a risk. Last method is allowing the risk to provide multitenancy for cloud computing applications. In this paper, the author has provided a solution to the multitenancy problem by implementing secure key mechanism using Software Defined Network Layers.
Multitenancy is the asset of the cloud computing providers, even though it comes with a security risks. If security is the first concern, then it eliminates the risk of multitenancy. Eric Keller, et al. [21] proposed a method for eliminating virtualization mechanism in order to increase the security. If we avoid this feature in the cloud, then the cost of system increases, leading to performance degradation with low level resource utilization.
Another way [7] was presented that multitenancy is an opportunity implemented without considering any security risks. In these extremes [9] the cloud providers provide multitenancy to the customer without giving any solutions and at least mitigating the problem to the customers. This type of exposure to the customers leave from cloud providers.
In this paper, the author has proposed a model for avoiding the multitenancy issues by using a secure key implementation with Software Defined Networks. An approach is discussed to tackle multitenancy in both security and resource allocation techniques, and it introduces security as a requirement by implementing resource allocation without affecting performance, cost, and power consumption. Finally this method is not applied on rather for any of cloud models, avoiding multitenancy issues.