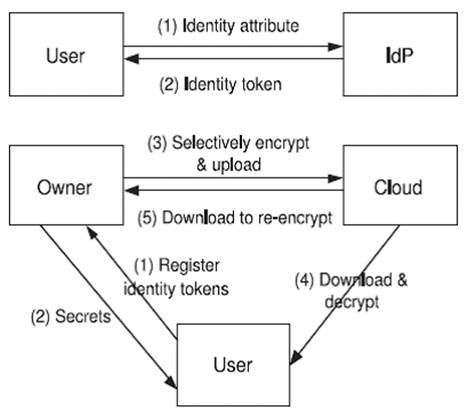
Figure 1. Single layer encryption
The two layer encryption is to enforce the fine-grained access control on confidential data hosted in the cloud, based on fine-grained encryption data. Under this scenario, data owners are encrypting the data before uploading them on the cloud and re-encrypting the data whenever users change to an alternate. Here the owner is communicating with clouds and users. The better approach used is to minimize the overhead work at the data owners. So, the authors have proposed an approach by using multi layer encryption, whereas the cloud performs a fine-grained encryption. A challenging issue is how to decompose Access Control Policies (ACPs) such that the multi layer encryption can be performed. In the present context, the authors have used novel optimization algorithm and KeyGen algorithm. Also, an efficient group key management scheme, that supports ACPs to work efficiently, is also used.
Cloud computing is a major challenging issue in providing security and privacy authentication of cloud technologies for data storage. An approach to mitigate these concerns is to use encryption. Encryption is the assurance of confidentiality data to the cloud and enforcement of fine-grained access control policies (ACPs). Nowadays many organizations having the ACPs are regulating that, what information the user wants can be accessed from the cloud. The ACPs are expressed in terms of the properties of the users, referred to as identity attributes. In this approach, an attribute-based access control (ABAC) is referred which supports fine-grained access control (FGAC) for high assurance of the data security and privacy control.
These approaches based on encryption have been proposed for fine-grained access control to the encrypted data and group data items based on ACPs to encrypt each group with different symmetric key. Then the users decrypt and download the encrypted data from the cloud, by using symmetric key. There are several limitations on single layer encryption and two layer encryption. So, the authors have proposed encryption process known a multi layer encryption, by reducing the communication and computation cost and to provide privacy authentication of multi keys for user registration.
It permits to access the data items and attributes for registered customers only. It depends on the specification as per the content based access only. It exhibits unique ways of performing access rights to the set of users and the individual users.
Very recently, in ref [1], the authors studied Attribute Based Group key management scheme which supports expressive access control policies. This is an attribute based access control mechanism based on broadcasting approach. This process is used to access control policies specifying the targets and users can access with the help of documents or subdocuments or data items. By using these ACPs, one can implement broadcasting encryption and segment into multiple subdocuments, each encrypted data with a different key. Broadcasting approach is to provide a privacy preserving in that users are accessible to a specific document or subdocuments. In ref [1], they have developed an attribute-based access control mechanism[1], where the users are able to decrypt the disseminated contents if and only if its identity attributes satisfy the user policies, then the content provider learns nothing about the user's identity tokens to identity attributes. That is why they have proposed a flexible key management scheme.
In ref [2], the authors studied privacy preserving attribute based encr yption approach, which is used for enforcement to the cloud. Attribute based encryption approach is based on a recent key management scheme that allows users whose attributes satisfy a certain policy to derive the data encryption keys to access from the cloud. Mohamad Nabeel proposed an approach which preserves the confidentiality of the data and the user privacy from the cloud, then the delegating of access control enforcement to the cloud. It reduces the cost of re-encryption required whenever the access control policies change using these approaches, which uses incremental encryption techniques.
In refs[3], [6], the authors studied the sharing of the data in public clouds based on fine-grained attribute-based Access Control Policies (ACPs). They also used an approach to encrypt documents satisfying different policies with different keys using a public key cryptosystem such as attribute-based encryption and re-encryption. By using this approach, they formalized a new key management scheme, called Broadcast Group Key Management (BGKM). The main advantage of their approach gives high security and privacy of BGKM scheme called ACV-BGKM (Access Control Vector- BGKM).
Further, in ref [4], the authors studied an attribute based group key management system, which gives fine-grained access control among a group of users in each group by managing this system by a set of attributes. This process was used to run collaborative applications and to distribute the group of user keys. The main advantage of this system is to support any monotonic expression of access control policy over a set of attributes. Even group changes doesn't affect the private information of existing group member by using the re-keying operation.
Also, in ref [5], the authors studied group key management schemes, which are not well designed to manage group keys based on the attributes of the group members. To overcome these drawbacks, M. Nabeel and E. Bertino proposed novel key management schemes that allow users, whose attributes satisfy certain access control policies to derive the group key management. These schemes efficiently support rekeying operations when the group changes due to joining or leaving of group members. In this process, data must be encrypted with the new keys, available only to the members of the group. The main advantage of these attribute based group key management schemes is, it provides keys and efficiently works on ACPs.
In ref [7], the authors studied the encryption process as well as accessing the delegated data. In another ref [8], the same authors studied broadcast encryption. The encryption process is to select encrypted data in public clouds and the data is used to encrypt the process of broadcasting.
Further, in refs[9] and[10], the authors studied secure sharing of the encrypted data. They have provided the privacy preserving for encrypted data and used attribute based encryption data to share security and privacy selectively.
Also, in refs [11] and [12] the authors studied an attribute based encryption and re-encryption. They referred these approaches as single layer encryption and two layer encryption approaches; they require the data owner to do the encryption process through clouds, encrypting the data before uploading them on cloud and re-encrypting the data whenever user credentials change.
In the sequel, the authors use the following notations from ref [1]. The ABE-based approaches rely on asymmetric cryptography; the authors two approaches rely only on symmetric cryptography which is more efficient than the asymmetric cryptography. The key issuance of Attribute based encryption approaches is that they do not support resourceful user revocations unless they use additional attribute based encryption.
It should be well-known that the ABE based approaches and our SLE approach (Figure 1) follow the data owner encrypting data before uploading the cloud. Here the Two Layer Encryption approach (Figure 2) provides the limited management of users and data in the cloud itself while assuring confidentiality of the data and privacy of users. After that, comparison can be done between SLE approach and TLE approach, and the data owner has to expose partial access control policies to the cloud of the identity attributes of users.

Figure 1. Single layer encryption
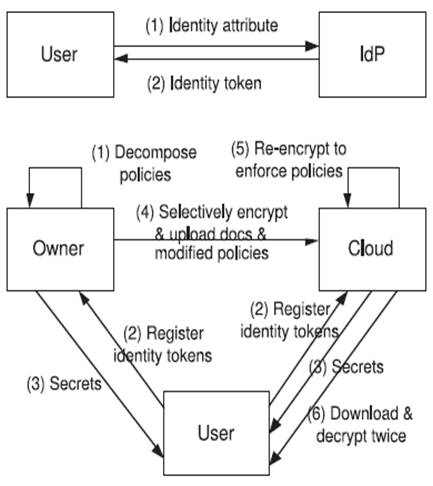
Figure 2. Two layer encryption
Attribute condition C is in the form of: “nameattropl”, here nameattr is the name of an identity attribute attr, and op is an operator such as >, <, ≤, ≥, ≠, =.
Access control policy: An access control policy (ACP) is the tuple (u, l), here the l denotes set of documents {d1 , . . . , dt }, and u denotes monotonic expression.
The following approaches - Single Layer Encryption (SLE) and two layer encryption have data owner on the basis of encryption performance, which shows the needed information on retrieving data access control. The SLE approach is to still require the data owner to enforce all the ACPs by fine-grained encryption, credentials change users added/revoked. These encryption activities have to be performed at the owner that thus incurs high communication and computation cost. For example, if a user is revoked, the owner must download it from the cloud, the data gets affected by this change which generates a new encryption key. Re-encrypt the downloaded data with the new key, and then upload the re-encrypted data to the cloud.
The two layers of encryption are applied to each data item uploaded to the cloud. Under this approach referred to as Two Layer Encryption (TLE), the data owner performs a coarse grained encryption over the data in order to assure the confidentiality of the data from the cloud. Then the cloud performs fine-grained encryption over the encrypted data provided by the data owner based on the ACPs provided by the data owner. The two layer encryption can be performed at novel approach of coarse grained and fine grained encryption, then the better solution of single layer encryption.
The TLE approach is to decompose the ACPs, such that there is fine-grained ABAC (Attribute based Access control) enforcement to the cloud. Each ACP should be decomposed to two sub ACPs such that there is conjunction of the two sub ACPs. The two layer encryption should be performed such that the data owner first encrypts the data based on one set of sub ACPs and the cloud re-encrypts the encrypted data using the other set of ACPs. The two encryptions together enforce the ACP as users should perform two decryptions to access the data. MLE approach which performs fine-grained ABAC enforcement can be delegated to the cloud, while at the same time, the privacy of the identity attributes of the users and confidentiality of the data are assured.
A new approach of privacy preserving attribute based group key management scheme can be developed by using the broadcast encryption and oblivious commitment based envelop protocols. In BGKM scheme, they perform rekey operation, by using private communication channels. BGKM scheme contains five algorithms.
3.1.1 Setup (l, N, Na)It takes the security parameter l, the maximum group size N, and the number of attribute conditions Na as input, initializes the system. It invokes BE:Setup (l, N), (l) and ACVBGKM:: Setup(l, N) algorithms.
3.1.2 SecGen (g)The secret generation algorithm gives an Usr , 1 ≤ j ≤ N a set of secrets for each commitment com € γ, 1 ≤ i ≤ m. It i invokes BE::GetSecGen and OCBE::GetData algorithms.
3.1.3 KeyGen (ACP)The key generation algorithm takes the access control policy ACP as the input and outputs a symmetric key K, a set of public information tuples PI and an access tree T. It invokes BE::GetCover () and ACV-BGKM::KeyGen algorithms.
3.1.4 KeyDer (b, PI, T)Given the set of identity attributes b, the set of public information tuples PI and the access tree T, the key derivation algorithm outputs the symmetric K only if the identity attributes in b satisfy the access structure T. It invokes BE:KeyDer and ACV-BGKM::KeyDer algorithms.
3.1.5 ReKey (ACP)The rekey algorithm is similar to the KeyGen algorithm. It is executed whenever the dynamics in the system change.
To provide a privacy preserving for data encryption algorithms, we are using multi layer encryption approach. In this approach, we are providing the security with multi keys by using Triple Data Encryption Standards (3DES) algorithm. Triple DES algorithm takes three 64-bit keys. Then the overall key length is 192 bits, such that the data is encrypting with the first key of DES and decrypting with the second key, finally is encrypting with third key again.
Triple DES uses a "key bundle" that comprises three DES keys, K1 , K2 and K3 , each of 56 bits (excluding parity bits).
The encryption algorithm is:
Cipher text = EK3 (DK2 (EK1 (plaintext)))
DES encrypts with K1 and decrypt with the K2 finally K3 encrypt with DES.
Decryption is the reverse:
Plaintext = DK1 (EK2 (DK3 (cipher text)))
Decrypt with K3 , encrypt with K2 and decrypt with K1 .
The technologies which are used for uploading the encrypted data incurs high cost because it manages the respective keys. Users can change credentials or modify policies, maintaining the work is burden to the data owner, which becomes critical. To reduce the overhead on the data owner, the authors have proposed a multi layer encryption based approach. This process is based on access control and reduces the burden on data owner and provides security to the cloud. Based on decomposed Access Control Policies, the authors also proposed a novel approach to privacy preserving attribute based encryption and fine-grained access control to the public clouds. Here, this approach is based on a privacy preserving attribute based group key management scheme that protects the privacy of users while enforcing attribute based Access Control Polices. Further the algorithms and experimental results are also explained in detail.