M. Chaitanya Kishore Reddy * Sunil Kumawath ** T. Gowtham Sai Krishna *** T. M. Sneha ****
* Assistant Professor, Department of Computer Science and Engineering, St. Peter’s Engineering College, Hyderabad, India.
**-**** Scholar, Department of Computer Science and Engineering, St. Peter’s Engineering College, Hyderabad, India.
Currently, distributed denial of service attack (DDoS) is a very serious threat in the internet. Large number of packets are send to a victim to jam the traffic so that the attacker can use the data of the victim. Various attack methods, its mechanisms, flooding attacks etc (Mirkovic and Reiher, 2005) are briefed in this paper. The scopes of DDOS attacks, measures and solutions to the attacks are hereby explored with effectiveness in various attack scenarios. A Distributed Denial-of-Service (DDoS) attack is an attack where the perpetrator uses more than one unique IP address, often thousands of them. Attacks may involve forging sender's Internet Protocol (IP) addresses (IP address spoofing) as an alternative or augmentation of DDoS, making it difficult to identify and defeat the attack. For specific targeted purposes, including disrupting transactions and accessing databases, an application layer DDoS attack is done, which requires less resource and often accompanies network layer attacks.
DDoS attack is the one where multiple systems attack a single target. This is done by causing Denial of service; whereas denial of service is defined as the attack that occurs when an attacker takes the action in such a way that it prevents the users from accessing targeted computers.
DDoS attacks are hard to detect and block, as the attack easily confuses the traffic; thus it becomes difficult to trace it. It is considered as the cyber-attack which slows down the access of a resource, network or systems (Dittrich, 1999). As DDoS attacks are powerful, the victim faces either corruption of files, loss of services or system shutdown. These attackers update DDoS tool kits which in turn increases the DoS or DDoS attacks. Compared to DoS attacks, DDoS attacks are difficult and very severe, as they have many-to-one dimension. DDoS attacks are termed as the launch of DoS attacks in large scale through a large number of distributed attacking host on the internet; these attacking programs have simple logic and need less memory for the process of implementing and hiding.
In 1998, a graduate student of MIT released a worm that rapidly spread throughout the internet due to which the DoS attacks infected all the systems; about 160,000 systems were affected in the United States. The student was sentenced to three years of probation, 400 hours of community service and were fined for $10,000.
DDoS means 'distributed DoS' because it arranges its weapons in such a way that, the damage occurs to the victim either by system shutdown or by corruption mechanisms (Figure 1).

Figure 1. DDoS Attack Architecture
These attacks are very frequent due to the internet architecture, which is designed to function not on security grounds.
Therefore, these security issues make the attack to spread to all other users. The following are the possible reasons for DDos attacks.
The Architecture of DDos attack is shown in Figure 2.
Figure 2. Architecture of DDoS Attacks
Attacker-Attempts to make the server unavailable
Zombie- The system that is compressed.
Handler- Allows sending and processing the message.
VICTIM-The user who is targeted.
The following are the classifications under DDoS attacks.
The attackers of the DDoS take different paths and strategies to confuse, block or deny a service (Cohen and Kuykendall, 2011; Leiwo and Zheng, 1997; Spatscheck and Peterson, 1999). This is done based on the source that is exposed to danger; hence it can also be called as the Vulnerability that is being targeted during the process of the attack.
The four main strategies involved in this area are:
The victim will contain protocol. The job of the protocol attack is to implement a bug where the protocols are present, so that the victim can make use of maximum resources.
At the first stage, the hacker or the attackers first chooses a target. They develop a code in such a way that they can trace the username and password. Once the correct password and username is achieved and if the combination is right then the hacker can access the secured data.
The attackers implement their task by using the User Datagram Protocol (UDP) and the Internet Control Message Protocol (ICMP) floods. This is done through packets, which is defined as the transfer of unit of data from the source to the destination [8, 9, 11]. Here, each packet transfer is connected to the main UDP service, in order to avoid this the system administrator should not allow any of the outside packets to enter his administrative domain.
ICMP is also called as, Ping Flood attack. This is used to send large number of ICMP packets to the server so that the server does not have time to respond to the other server.
Th e Classification of automation attacks is shown in Figure 3.
Figure 3. Classification of Automation Attacks
Here, the attacker manually scans and attacks the target system. It is a hard coded attack where the attacker cannot configure the agent whenever he wants.
Here, it leaves more space for the attacker to configure and types some new instructions to the agent.
It does not have space for configuration and communication with the agent.
It is divided into two types of communication factors which are as follows.
I n d i r e c t c ommu n i c a t i o n, a t t a c ke r s d i r e c t l y communicate with the handler or zombie to attack the victim so that each other can know their identities.
In indirect Communication, attack is done without any communication between the attacker and handler or zombie. Thus true identities are not known.
Attacks with gradually increasing rate, lead to slow exhaustion of the victims.
In this attack, attacker sends small packets to the victim's machine as fast as possible, with a constant speed. Therefore, the attacker will be in a trouble of revealing his true identity because small packets lead to large streams where the packets can be easily detected. Almost all the attacks use constant rate mechanism, as it is cost effective to the attacker.
In this, attacks the attacker sends the packets with various speeds so that there is no trouble of detection in his activity.
The variable rate is divided into two types.
It is briefed based on the behavior of the victim; the attacker sends the packets in a fluctuating manner to confuse the victim, so that the attacker can access continuously to lead the attack successfully.
Increasing rate is the rate at which the packet stream speed is gradually increased until the victim resources are exhausted, which leads to delay in the detection of the attack.
Impact means how the Attack is manipulating the victim out of his control to give his services to his clients. It is of two types, they are:
In this, the attacker makes the victim to deny the services to its clients completely; these are currently reported attacks.
Hackers consume some resources of the victim's system and degrades the services to its legitimate client or users.
The Degree of automation is shown in Figure 4.
Figure 4. Degree of Automation
For the detection of distributed denial of services (DDoS), there are two categories of network based detection system which are as follows:
Nowadays misuse detection system is mainly used. It mainly detects the DDoS attacks by monitoring the network-based activity and looking after the existing attack signatures. Even though it has high detecting and positive rates, they are easily exposed to new and existing attacks (Ferguson and Senie, 2000; Lau et al., 2000; Paxson, 2001). It is complicated because tasks need to be performed on signature database, which is a manual process.
The typical DDoS Attack has two main tasks such as:
In the first form of attack, the victim is selected first in order to get targeted, next the target command is sent to the zombies [2]. This is done to launch a bandwidth attack. In order to avoid this, when the packets are dropped they make sure that these packets contain some fake IP addresses in order to confuse the attacker if he wants the package to stop coming his way to achieve his target.
The second form of attack aims to crash a system by sending forge packets in order to make the server busy. These attacks cannot be prevented easily because any number of sources can attack at any time [Refer Figure 5].
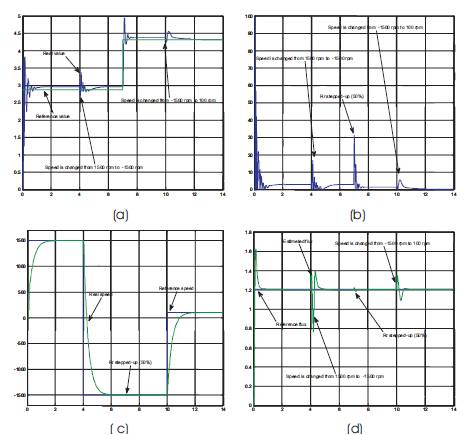
Figure 5. Attacker vs Victim
When multiple sources are used, defensive fight becomes more complicated. The main reasons are that the targets can be attacked easily because the internet is available for everyone to access publicly. Due to this, it can even cause minor problems to major problems such as financial losses for companies.
As DDoS attacks are very easy to implement, it is very important to detect them (Alomari et al., 2012). The detection of DDoS attack done by an algorithm which contains the following three stages:
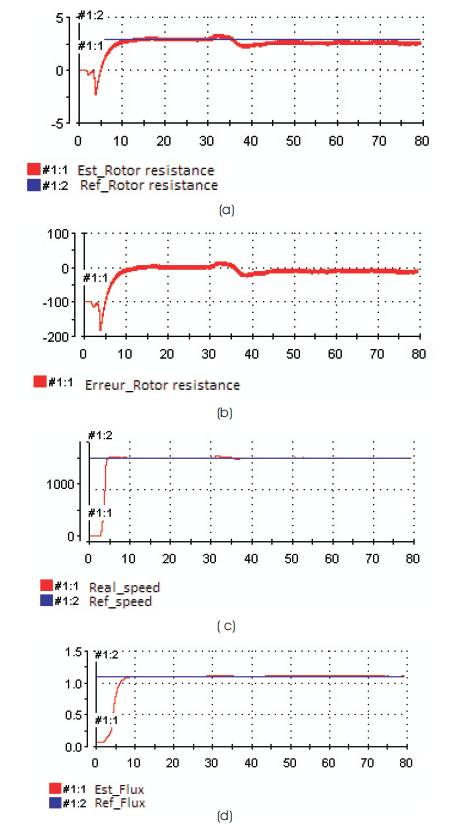
Figure 6. Flowchart of Detection Mechanism
Attacks have a trend in the network security field. These tools will define their current state Figure 6. There are several well-known DDoS attack tools in order to overcome the DDoS attack (Mirkovic and Reiher, 2004).
Trin00 is the first DDoS tool which came into the market in June and July 1990. DDoS attacks under this TRIN00 network can set up 1000 systems on the internet. They use a number of TCP-UDP ports.
TFN can generate UDP and ICMP echo request floods, TCP SYN floods and ICMP directed broadcast. Through ICMP_ECHO_REPLY, handlers and agent do packets communication.
Stacheldraht is the combination of Trin00 and TFN; Like TFN, it adds encryption of communication between the attackers, and Stacheldraht master, which adds an automatic updation of the agents.
Mstream tool is used to spoof temporary packets with acknowledgement (ACK) to confuse the attacker if he wants the packets to stop and set it to attack. It can be performed with UDP and TCP packets. Stream master can control unlimited zombies.
Code red was discovered in July 16, 2001, which is also called as self-malicious code. It achieves a synchronized attack by preprogramming onset and time per attack, method, and target.
In the defense mechanism, the defense algorithm drops the packets sent by the attacker, if the packets received by are larger than 100 packets/seconds [Refer Figure 7].
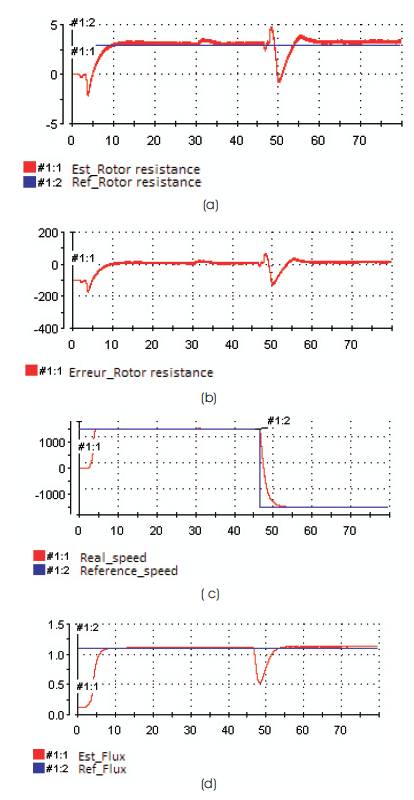
Figure 7. Defensive Mechanism
Defensive mechanism is completely based on how soon an attacker can be detected and how near can the attack be stopped [Refer Figure 7]. This is done by detecting on various paths (Chang, 2002; Hashmi et al., 2012). Usually, when the attack is detected the victim is disconnected from the network in order to reach the targeted site; a lot of resource is being wasted during the detection of the targeted path.
It is not difficult to detect a DDoS flooding attack as this attack occurs in the form of a funnel (Bhuyan et al., 2013; Solms and Niekerk, 2013) through which the attack is being transferred, and it is received by the receiver at the other end of the funnel (Mirkovic and Reiher, 2004). It is not difficult to detect if there are more number of DDoS flooding attacks [Refer Figure 7]. The defensive algorithm is given in Figure 8.
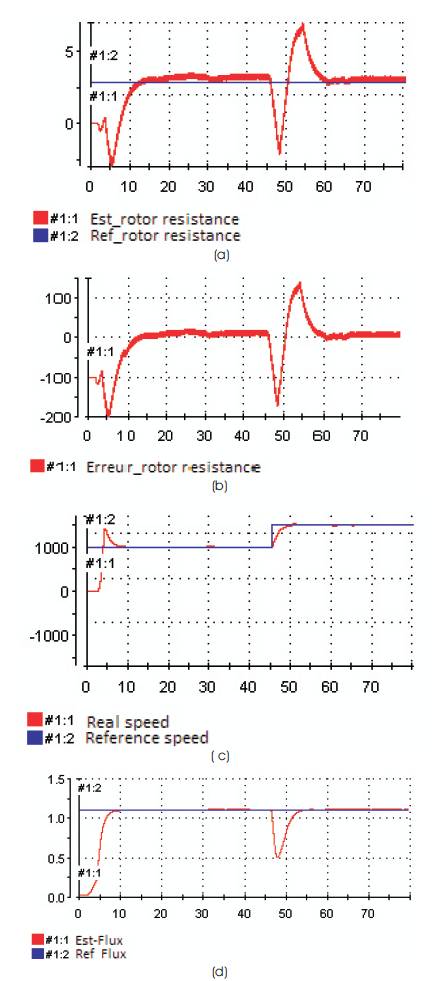
Figure 8. Defensive Algorithm
Defensive mechanisms (Peng et al., 2007; Solms and Niekerk, 2013; Zargar et al., 2013) are mainly classified into two main criteria which are as follows:
Report of Attacks gives the information on the following five dimension.
Distributed denial of services (DDoS) attack is a serious and complex problem in today's technological world. DDoS is the attack where multiple systems attack a single target, which is done by causing denial of service. There are many DDoS attacks, which are caused in many ways by the attackers and zombies. For example, when a group of people tries to enter into a single door of a shop by not letting multiple group of people entering into the door. As a counter measure of DDoS attack detection, defensive mechanisms and tools used are given and explained in detail in this paper. It is concluded that this will provoke future research work.
[1]. Alomari, E., Manickam, S., Gupta, B. B., Karuppayah, S., & Alfaris, R. (2012). Botnet-based Distributed Denial of Service (DDoS) Attacks on Web servers: Classification and Art. Cornel University Library.
[2]. Bellovin, S. M. & Gont, F. (2012). Defending against sequence number attacks. RFC 1948.
[3]. Bhuyan, M. H., Kashyap, H. J., Bhattacharyya, D. K., & Kalita, J. K. (2013). Detecting distributed denial of service attacks: methods, tools and future directions. The Computer Journal, 57(4), 537-556.
[4]. Chang, R. K. (2002). Defending against floodingbased distributed denial-of-service attacks: a tutorial. IEEE Communications Magazine, 40(10), 42-51.
[5].Cohen, M. L. & Kuykendall, D. A. (2011). Prevention of distributed denial of service attacks. U.S. Patent Application No. 12/889, 322.
[6]. Dittrich, D. (1999). The DoS Project's 'trinoo' distributed denial of service attack tool
[7]. Ferguson, P. & Senie, D. (2000). Network Ingress Filtering: Defeating Denial of service Attacks which Employ IP Source Address Spoofing. RFC 2827.
[8]. Garg, A. & Reddy, A. L. N. (2002). Mitigation of DoS attacks through QoS Regulation. In Proceedings of IWQOS workshop.
[9]. Gavrilis, D. & Dermatas, E. (2005). Real-time detection of distributed denial-of-service attacks using RBF networks and statistical features. Computer Networks, 48(2), 235- 245.
[10]. Hashmi, M. J., Saxena, M., & Saini, R. (2012). Classification of DDoS attacks and their defense techniques using intrusion prevention system. International Journal of Computer Science & Communication Networks, 2(5), 607-614.
[11]. Iumatti-Lodewyk, V. (2015). A meta-synthesis of micro facial expression literature and the legal system (Doctoral dissertation, Alaska Pacific University).
[12]. Lau, F., Rubin, S. H., Smith, M. H., & Trajkovic, L. (2000). Distributed denial of service attacks. In Systems, Man, and Cybernetics, 2000 IEEE International Conference on (Vol. 3, pp. 2275-2280). IEEE.
[13]. Leiwo, J. & Zheng, Y. (1997, July). A method to implement a denial of service protection base. In Australasian Conference on Information Security and Privacy (pp. 90-101). Springer, Berlin, Heidelberg.
[14]. Mirkovic, J. & Reiher, P. (2004). A taxonomy of DDoS attack and DDoS defense mechanisms. ACM SIGCOMM Computer Communication Review, 34(2), 39-53.
[15]. Mirkovic, J. & Reiher, P. (2005). D-WARD: a sourceend defense against flooding denial-of-service attacks. IEEE transactions on Dependable and Secure Computing, 2(3), 216-232.
[16]. Paxson, V. (2001). An analysis of using reflectors for distributed denial-of-service attacks. ACM SIGCOMM Computer Communication Review, 31(3), 38-47.
[17]. Peng, T., Leckie, C., & Ramamohanarao, K. (2007). Sur vey of network-based defense mechanisms countering the DoS and DDoS problems. ACM Computing Surveys (CSUR), 39(1), 3.
[18]. Prier, G. K. (2003). IDward: Implementing DWard on the IXP (Doctoral dissertation, University of California, Los Angeles).
[19]. Solms, R. V. & Niekerk, J. V. (2013). From information security to cyber security. Computers & Security, 38, 97- 102.
[20]. Spatscheck, O. & Peterson, L. L. (1999, February). Defending against denial of service attacks in Scout. In OSDI (Vol. 99, pp. 59-72).
[21]. Zargar, S. T., Joshi, J., & Tipper, D. (2013). A survey of defense mechanisms against distributed denial of service (DDoS) flooding attacks. IEEE Communications Surveys & Tutorials, 15(4), 2046-2069.