Figure 1. Categories of Biometric Systems (Mudholkar et al., 2012)
This work focuses on the design and implementation of a fingerprint biometric identification system for charging and discharging library materials. Charging of library materials denotes lending or borrowing of library materials, however discharging is done when the patron or borrower return the borrowed library material. The crux of charging and discharging library materials is the means to identify the borrower and the book borrowed amidst great number of library patrons and huge collection in the library. Many methods of charging and discharging have been developed over the years. Most of these methods use a borrower's & book's card as means of identification, until the advent of the automated system. This work is aimed at using fingerprint identification as a veritable method for patron's identification during charging of library materials. It covers the conceptual analysis and practical design of a fingerprint identification system using Digitalpersona-SDK and is implemented for charging and discharging materials in the library. The fingerprint biometric identification system is designed using Java programming language and MySQL database at the backend for storing patrons' information including fingerprint images. Usability evaluation of the system revealed that the fingerprint approach to charging and discharging of library materials is faster, more effective and efficient than the manual system.
Libraries are indispensable components for achieving the missions and vision of any institution where information is stored and organised to facilitate accessibility and utilisation. Libraries are the hubs of all academic activities in any institution of learning, as they acquire information resources in accordance with the curriculum of their parent institution to support, compliment and supplement the missions and vision. Libraries are therefore compartmentalized into departments, sections and units in order to deliver effective and efficient services to their patrons. The section/unit of the library that deals directly with the library patrons is the circulation unit, also referred to as the customer service unit. The services or functions of the circulation unit include charging and discharging of library materials to patrons. Other services of the circulation unit include registering the library patrons, keeping daily statistics of book used, controlling and regulation of library materials, shelving of books on the shelves, monitoring damaged materials for repairs etc. ( Adebowale et al., 2013). The circulation service integrates the library patrons and library materials, and make the patrons to use the library materials to a maximum extend within and outside the library building, therefore, it is the nerve centre of the library wherein the patrons find and utilize the library materials. The image of the library largely depends on the services provided by the circulation unit, and its importance is hinged on delivering impartial, effective, efficient and speedy services to the patrons ( ShodhGanga, 2018).
Charging of library materials denotes the lending of library materials to patrons. It is used interchangeable with a library loan or lending ( Adebowale et al., 2013). It is the act of lending library materials to patrons who require them outside the library building. The charging activities include obtaining the library materials (e.g books) from the shelf to the circulation desk; the circulation staff affirms the wellness of the book for charging and gives the borrowers' slip to the borrower, thereafter, the staff stamps the book slip and the book card with the date due stamp and gives it to the borrower. After these, the circulation staff files the slip behind the borrower's registration card. Moreover, the borrower must be a registered member of the library to enable a library material for his/her borrower. On the other hand, discharging of library materials is done when the borrower returns the borrowed library material(s) on or before the date with no intention of renewal. ( Adebowale et al., 2013). The circulation staff cross-check the returned item before discharging it. In a nut shell, to ensure the safety of the returned material by the patron, the circulation staff performs the following activities: (1) Identifies the patron/borrower; (2) checks the book to guarantee that it is returned in great condition; (3) Retrieves the borrowers' slip and book card from record; (4) Checks if the date return is not overdue, otherwise fines the patron based on the library policy; (5) After discharging the book, the book card is embedded in the book pocket and the book is transmitted to the stack for shelving; (6) Lastly, if the patron intends to renew the material, it is first discharged and then charged out to him/her, again with a new date due. There are certain restrictions to the number of renewals on a book by a patron depending on the library policy.
There are various methods of charging and discharging of library materials. They can be broadly categorized as manual like the Browne and Newark system, the semimechanized system like the Edge-notched card system and the IBM circulation control system, and the automated system, which involves the use of computer software to manipulate the circulation operations ( Geer, n.d.). Today, many software packages are developed to handle library circulation routine activities including charging and discharging of materials. In general, a patron will be first registered to the system as a new member before he/she can be eligible to borrow a material. Thus, there is a mode of identification to identify a patron which can be via the patrons' ID card. The focal point of this paper is on fingerprint biometric identification as a veritable strategy for users and book identification for charging and discharging of library materials.
The full essence of a library is achieved when the library delivers efficient, effective and prompt services to its patrons, which, as such, should not waste the time of the patrons. The Browne system fails to keep record or statistics of loans, and they both require the circulation staff to search through several books/borrowers' cards in order to identify an item to discharge. With the increase in the number of readers using libraries, it became necessary to design and develop a more efficient and speedy method of identifying the borrower and the book in charging and discharging of library materials. The use of Personal Identification Number (PIN) or passwords can be forgotten or misplaced by an authorized (registered) patron of the library and may be intercepted by an unauthorized user. Since biometric identifiers and features can't be forgotten, misinterpreted or shared by a patron; it is against this backdrop that the researchers consider it appropriate to design a charging and discharging system based on the fingerprint biometric identification technology as a veritable method for charging and discharging library materials.
Charging denotes lending of library materials to registered patrons of the library, which gives patrons the opportunity to use the library materials on the premises of their choice ( ShodhGanga, 2018). However, discharging of books is done when the patron returns a borrowed item. There are several methods used to charge library materials to patrons. These methods have been developed by libraries from time to time, using manual and semi-mechanized system and the recent evolution of the automated circulation system through the use of computer software.
This is the most common manual charging system used in most libraries, it was originated in 1900, which involves recording the book's title, author and call number in a card and inserting it into a paper pocket, and a date due slip is fixed or stamped in the pocket. The patrons are issued a library identification number or borrowers' identification card that uniquely identifies them ( Geer, n.d.). Modification of the Newark system include the use of embossed printers to imprint borrower's ID number on the charge card or the entire borrower's name and address to eliminates the need to refer to the registration file for sending overdue notices. Similarly, Merriam Webster Dictionary (2018) describe the Newark charging system as a charging system for library materials in which a book is obtained to a user and the date of issue or the date due is stamped on the book's card, on a plate in the book, and on the borrower's card. Moreover, the borrower's name or number is additionally included in the book's card which is filed until the book is returned or discharged and the date is recorded on the borrower's card.
According to ShodhGanga (2018) and Geer (n.d.), other methods for charging and discharging library materials developed over the years, which include the day book system, the Browne style, The ledger system, the book card system, the transaction systems, Gaylord machine, Detroit self-charging system, visible record charging system, the edge-notched card system, Dickman book charger system, Gaylord charging system; photographic charging system, audio charge system; IBM circulation control system; IBM modified circulation, control system; Wayne county charging system; double record charging system, tab charging system, punched card charging systems; tab-pocket charging system; accession number charging system, coloured card charging system, double call slip charging system etc.
The challenges or limitations of the manual system can be summarized as follows:
The advent of computer in the 1960s and microcomputers in the 70s and 80s had major impact tremendously on library circulation routine operation. Nowadays, all important statistical data pertaining to library materials used, borrowed or reserved and the library patrons can be obtained by simply sorting or searching the data of the circulation process in a computer system. The advent of barcode scanners has eliminated the card-based systems in most libraries today.
As stated earlier, the automated system requires some means of identification of the patrons/borrower and book to be borrowed, which may be through an ID card Personal Identification Number (PIN) issued to the patron during first registration in the library. The fingerprint identification system involves the use of the patron's fingerprint as a means of identifying the patron during charging and discharging of books respectively. The advantages of the method include:
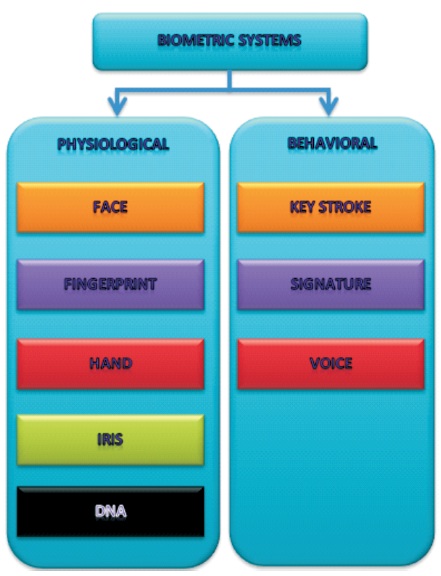
Biometrics denotes the utilization of physiological or behavioral qualities (or identifiers) to find out and confirm individuals' identity ( Muyideen et al., 2014). As indicated by Digitalpersona (2007), biometric security is referred as programmed or automatic recognition of people dependent on their idiosyncratic anatomical (face, fingerprint, hand geometry, iris) and behavioral (voice, signature) attributes. It is a strategies for distinguishing an individual based on some behavioral or biological features. Numerous biological features, for example, fingerprints, and behavioral attributes, for example, voice patterns, are idiosyncratic to every individual. Hence, biometrics is increasingly dependable and progressively reliable in recognizing a particular individual and an impostor than any other technique based on an identification (ID) inputs or a password ( Wikipedia, 2018). Correspondingly, Bhattacharyya et al. (2009) and Mudholkar et al. (2012), classified the biometric attributes into two primary classes (Figure 1): (1) Physiological qualities, which are the pattern of the shape of individual's body and in this way it differs from individual to individual, for example, fingerprints, face recognition, hand geometry and iris recognition and so on; and (b.) Behavioral qualities are patterned according to the conduct or behaviour of an individual, for example, signature, keystroke dynamics and voice recognition. Voice recognition is likewise viewed as a physiological biometric and it differs from individual to individual.

Figure 1. Categories of Biometric Systems (Mudholkar et al., 2012)
Redhu and Balkishan (2013) submitted that fingerprints are fully developed at around seven months of fetus (unborn offspring, at a phase when all the structural highlights of the grown-up are conspicuous) development in the womb. The general features of the fingerprint develop as the skin in the fingertip starts to separate the flow of amniotic liquids around the fetus and its state in the uterus is changed during the separation procedure. Therefore the cells on the fingertip are developed in a micro environment that is quite distinct from hand to hand and finger to finger.
Prasathkumar and Brindha (2014) maintained that fingerprint is the framework of ridges and valleys (likewise called furrows in literature of fingerprint) on the outside of a fingertip or graphical shape on the fingertips. Microsoft Encarta (2009) opined that, a fingerprint is the shape or pattern of ridges and furrows on the outside of a fingertip. Similarly, Subban and Mankame (2013) investigated that it is the impressions of the minute ridge of all surface area of the finger, or any part of the finger ( Bhattacharyya et al., 2009). Now, two people have the same fingerprint arrangement, and the fingerprint layout of any individual stay unaltered through out the life. Fingerprints are unmistakable to the point that even the prints of indistinguishable or identical twins are distinct. Among the diverse biometrics, fingerprints have the more adequate and convenient features including peculiarity, precision, throughput, accuracy, size and low cost of procurement, advancement in its development and innovation and comfort of utilization, which dominates the biometric technology in most business applications. Rani and Sharma (2014) maintained that fingerprint recognition technology is the most modern strategy of all biometric strategies that has been thoroughly confirmed through different applications. Besides, it is stated that, the Federal Bureau of Investigation (F.B.I.), has more than 200 million fingerprints information, and of all the fingerprint information collected over the years, there is no two fingerprints identical. ( Digitalpersona, 2007).
Usually, a fingerprint impression is obtained by applying ink at the fingertip and impressing it on a piece of paper; thereafter, the paper is scanned. However, in today's innovation, fingerprint scanners are used directly to capture people's fingerprint ( Bhattacharyya et al., 2009). The degree of detail in fingerprint images scanned and transmitted into a biometric system relies upon a few variables, including the degree of pressure exerted by the fingertip during the scanning, the presence of any cuts or deformities on the fingertip, and the dryness of the skin. In this way, any strange or noticeable highlights on a fingertip such as the endings of the fingerprint ridges, and ridge bifurcations, or branches (minutiae), are altogether utilized in a biometric system dependent on the fingerprint identification ( Subban and Mankame, 2013; Microsoft Encarta, 2009). Fingerprint biometric systems identifies people by contrasting the ridges, shapes and layout on the finger ( Digitalpersona, 20073).
The skin that lies within the surfaces of our hands, fingers, feet, and toes is ridged or secured with concentric raised patterns. These ridges are referred to as friction ridges and they lubricate the surface of our skin, making it simpler for us to handle and clutch items and surfaces without slipping. Furthermore, these ridges are designed, forked and broken in numerous ways in form of a wave that makes ridged skin areas and contribute to the distinctiveness of fingerprints ( Digitalpersona, 2007).
Significantly, there are two kinds of fingerprint features that are utilized in identifying people, they are global features and local features. The global features can be seen with the naked eye, they include (1) pattern area – some portion of the fingerprint that contains the global features; (2) core area– it is situated around the center of the finger impression and is used as a beginning reference point for understanding and categorising the print; (3) type lines – the two deepest ridges that begin parallel, diverge which almost surround the pattern area; (4) delta - the point on the principal bifurcation where the ridge forks into two distinct directions and is found straightforwardly before the line's point divergence; (5) ridge count– the quantity of ridges between the delta and the core; it is obtained by ascertaining the number of ridges that touch a straight line from the delta to the core; (6) fundamental ridge designs. Figure 2 shows the delta and pattern area of finger print.

Figure 2. Delta and Pattern Area ( Digitalpersona, 2007)
In addendum, the local features are the smaller highlights of fingerprint known as minutia points. They are generally two-dimensional in structural arrangement. The local features differentiate two people who have the same global feature. Hence, it is crux of the fingerprint identification system ( Prasathkumar & Brindha, 2014; Digitalpersona, 2007). According to Prasathkumar and Brindha (2014), the two most incredible local ridge designs (likewise called minutiae) are:
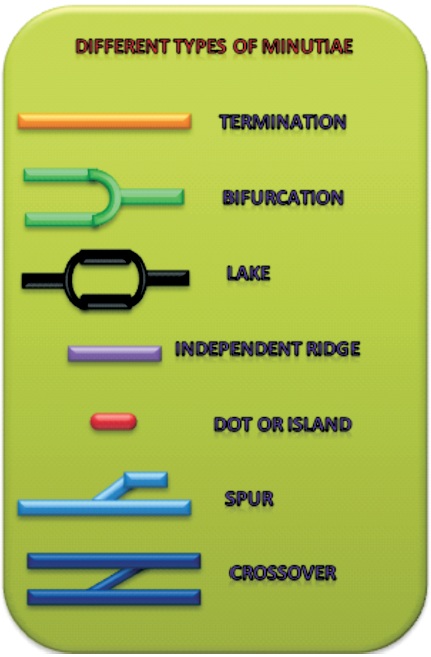
Figure 3. Different Types of Minutiae ( Redhu & Balkishan, 2013)
These two minutiae (ridge termination and ridge bifurcation) are significant in fingerprint recognition. Some researchers maintained that a qualitative fingerprint identification system has around 40-100 minutiae in each ( Redhu & Balkishan, 2013; Prasathkumar & Brindha, 2014). Minutiae can be portrayed by its position or its reference point. From a broad perspective, fundamental ridge patterns fall into three groups: whorls, loops and arches. Experts have categorized the ridge patterns into these categories in order to simplify searching of fingerprints in large databases. These groupings are not adequate for fingerprint identification in themselves, which can help accelerate the processing time and narrow down the search to a specific group. When a fingerprint is identified as a specific type like arch, the search continues in that type only and ignores the other types in the database ( Microsoft Encarta, 2009; Digitalpersona, 2007).
Fingerprint identification offer numerous solutions to security issues faced by other types of identification systems, these include:
The fingerprint biometric identification system for charging and discharging of library materials was designed using Object Oriented Programming (OOP) Language, specifically, Java. MySQL database management system was used at the backend for storing library users's information including fingerprint data. Moreover, Digital persona-SDK (Software Development Kit) was used to implement the fingerprint enrollment, verification and identification modules. Furthermore, activity diagram of the Unified Modeling Language (UML) was adopted to elucidate the dynamic parts of the system as shown in the Figure 4. The diagram illustrates the access control to the system using fingerprint biometric authentication. An authorized user needs only to scan his/her fingerprint in the scanner to borrow or discharge a library material.
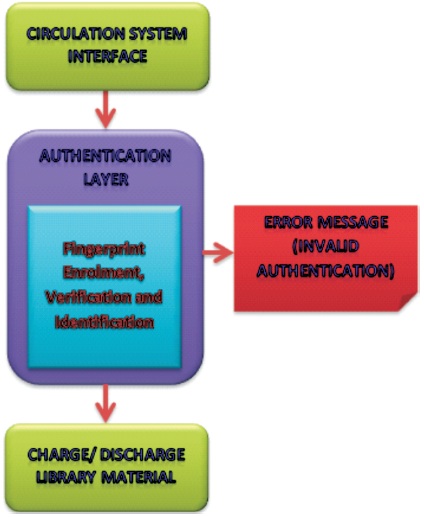
Figure 4. Activity Diagram for Users' Identification Source: Authors' Concept
The designed fingerprint biometric identification system for charging and discharging of library materials consists of three processes:
The screenshots of the interface design of the fingerprint biometric identification system for charging and discharging of library materials are presented below.
This is a list of all patrons registered into the system, showing their basic information captured during registration time and the date/time of registration (Figure 6). From this interface, the circulation staff can edit, view or delete a user accordingly.
This module handles charging of library materials to registered users. First, the item to be borrowed/charged is selected from the entire library catalogue. If the book is available (not borrowed/charged out), a dialog box appears with the details of the material to be borrowed and user simply scans his/her fingerprint to verify or authenticate. This is the verification/authentication phase of the fingerprint identification process. If the user is registered, his/her fingerprint is linked to the one in the database to identify him/her in order to charge the material against his/her account. If this process is unsuccessful, an error message is sent, otherwise, the item is charged successfully. Finally, a log is generated in the list of borrowers and list of borrowed books to keep a track of books charged out and borrowers. Figure 7 shows the error message charging the library item via fingerprint and Figure 8 shows the success message charging the library item via fingerprint.
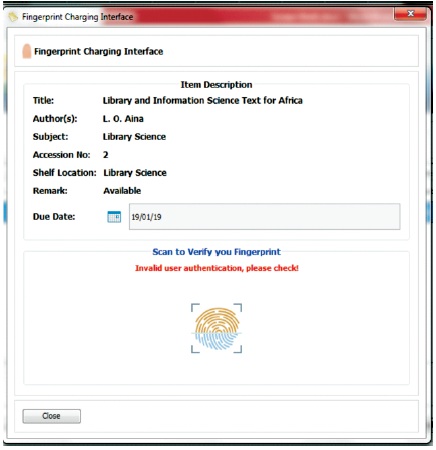
Figure 7. Error Message Charging Library Item Via Fingerprint
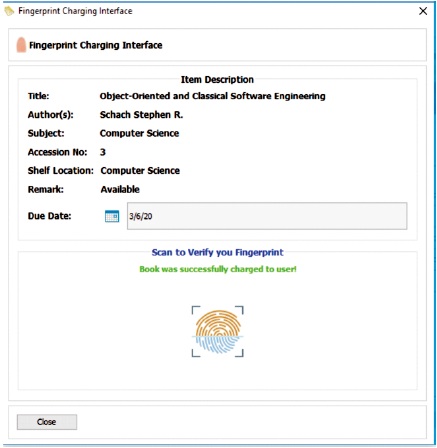
Figure 8. Success Message Charging Library Item Via Fingerprint
Discharging of books is done when the user returns the book. This is done either through the list of borrowed books or list of users as shown in the Figure 9.
The module stores the list of all books borrowed to users. It gives the bibliographic details of the books as well as the information of the borrowers with their photographs. In addition, it shows the current remark of the borrowed books in three ways: Overdue, Returned or Active. The page of overdue book is shown in Figure 10.
The system triggers overdue notice showing the number of books that are overdue and need to be returned by the borrowers. Furthermore, the list of overdue books are sorted and displayed in the list of borrowed items where the remark reads 'Overdue'. Figure 11 shows the overdue notification displayed in the screen.
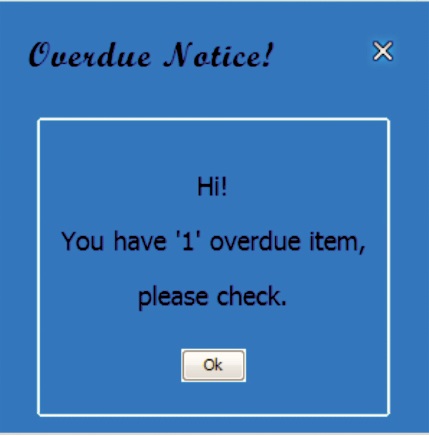
Figure 11. Overdue Notification
This aspect of the application generates statistical charts of books actively borrowed, overdue and returned accordingly, as shown in Figure 12.
The search box/wizard shown in Figure 13, facilitate accessibility of books to be borrowed as stored in the library catalogue. Ideally, the book entries are inputted during cataloging and classification and synchronised to the circulation system and other departments of the library. However, for the purpose of demonstration, a book entry module was designed to undertake the task.
The system enables the records in the database to be copied/backup to external storage media. This includes the users' profile (picture, fingerprint data, name, email, phone number etc.), circulation statistics and other vital information stored in the system. In case of emergencies, the backup file can be restored to the system conveniently. In a situation where the computer system of the unit is lost or crashed/damaged, the circulation staff can acquire a new system, install the application, and thereafter restore the backup files. The database backup/restore module is shown in Figure 14.
This study revealed that biometrics has great premise in librarianship. Although this study only deals with the application of fingerprint biometric identification for charging and discharging librar y materials, the application of biometrics in librarianship is broad. Providing safe and secure environment for library staff, resources and facilities is the crux and impetus in the adoption of biometrics in libraries. In this regard, the use of biometric technology is convenient for library professionals. Various biometrics are used in libraries. The application of biometrics in libraries encompasses collection development, staff management and user management. Moreover, other biometric identifiers such as iris, facial recognition, DNA etc., can be applied in library security for efficient service delivery.
According to Shafagat (2016), libraries use computers systems for various purposes, such as books circulation, cataloging, information services, information acquisition and processing. Biometric technologies are widely used to provide safety of the library's valuable collection, infrastructure and human resources. Biometric technologies are very useful for library information system (LIS), so that it ensures library administrators to control library resources, computers, internet access, and software from single point. Furthermore, LIS staff deals with big database processing, and provides access to on-line journals and on-line catalogs through passwords within the network, which plays an important role in the prevention of cyber-crime. Hence, the pressing need for the adoption and implementation of biometric technologies in library and information services.
This research culminated in the design of a fingerprint biometric identification system for charging and discharging of library materials, as an efficient, effective and veritable method for identifying patrons and books borrowed in the library. Fingerprint biometric identification is highly reliable; because, physical human characteristics are much more difficult to forge than security codes, passwords and hardware keys. Fingerprints are distinctive and persistent, and people's fingerprint do not change over a lifetime. This makes it a perfect biometric identification method as revealed in this work. The designed fingerprint biometric system validates library users by looking at the ridges and patterns on their fingers. The DigitalPersona fingerprint engine searches for distinction within these areas, in this manner, it uses these two properties of fingerprints with the aim of distinguishing an authorized user from an imposter.