
Table 1. Examples of AT Commands for SMS
Security systems like surveillance cameras will only record the incident and cannot do anything to prevent it. Nowadays most of the crimes occur in the lavish shop (jewellery), where CCTV are installed. Crimes are usually found out after it is being committed and the owner gets the information only after a crime incident. As per the survey, around 51% of the crime rate is found in the robbery. In the present, security system requires more storage because of continuous surveillance. The proposed system is applicable in the area where no one is permissible to enter, also in the area, where we need to investigate the crime. Once the system detects motion, the camera starts recording and captures live images. The image is processed to verify whether it is a human or not. If human is found in the image, the owner is quickly alerted by sending an alert mail. This mail will also contain the picture of the intruder captured by the camera. The security gate closes so that the intruder is captivated inside. The buzzer is used as an alarm to alert the neighbours about the intrusion. As a result of the above technology, the owner will have no worries regarding the shop in their absence due to real-time image feedback. The intruder is not able to escape from the site because of the security gateway. False triggering of alarm is eliminated.
An increase in the number of crime incidents around the globe has made Governments and organizations take preventive actions to preclude the occurrence of such incidents. It is not just Governments or businesses that are chosen to wear a defensive posture, people at the individual level as well are concerned about personal as well as home security. More and more people are increasingly leveraging technology for personal security as well as the security of their homes. Security incidents can be brutal, they can cost a fortune and even human lives. Installing security systems to encounter potential security threats seems like a solution.
Despite the widespread adoption and growing numbers of installations across the globe, prices of security systems are still not very affordable. Expensive hardware is what most buyers notice during their first encounter with a security system. Security systems like surveillance cameras will only record the incident and cannot do anything to prevent it.
The need to develop a cost-effective surveillance system through innovative technology immensely influenced the development of this project. This project will design and implement a security system based on the Raspberry Pi microcomputer. The system should be able to detect motion of an intruder, activate a camera to take the frames of the video after motion is sensed, and then send an alert to the owner through electronic mail with an image attachment.
False triggering is one of the major shortcomings of current security systems. Siren of your home security system breaks up in the midnight and wakes up your entire family, only to find out it was a false alarm caused by your beloved cat or an unknown reason. With the widespread adoption of security systems, and bearing a crucial responsibility of safeguarding business, homes, and expensive possessions, it has become important that these systems work as expected.
In this project, it is intended to improvise the standards by employing new design techniques and developing a lowcost security system.
The anti-theft system detects a human intrusion and informs the owner by sending an SMS and also by sending a live image through email using IoT. There is also an added functionality that at the same time there will a security purpose gate installed which will be closed when the intrusion is detected so that the intruder cannot escape and provide complete security. The camera is used to capture the live images of the crimes happening. The captured are stored in a particular folder in Raspberry Pi.
This project aims to make an automated security system for the lavish shop such as jewellry. The project consists of Raspberry Pi with a camera, sensors, and an alarm. The system can effectively identify a human intruder and prevent false alarms when an intruder is non-human, by distinguishing between human and non-human objects.
Nowadays, technology plays an important role in our life, and security becomes the most important factor. In the world of Internet of Things (IoT) when we have all the technologies to protect our shop, we always want a system that can be controlled and monitored from anywhere. This project deals with the design approach of a real-time Intelligent monitoring system for intruder detection that reinforces surveillance technology to provide essential security to our life and associated control and alert operations.
The system is designed to detect burglary, the image of the person is captured by the camera and sent to the owner's mobile. Raspberry Pi based smart surveillance system presents the idea of monitoring a particular place in a remote area.
The proposed solution offers a cost-effective, ubiquitous surveillance solution, efficient, and easy to implement. This type of technology is of great importance when it comes to surveillance and security.
It continuously checks the status of the place using sensors. If the system detects the intruder, the lights and alarm are turned on simultaneously. As soon as sensors detect motion, captured images are sent to mobile through IoT and wait for the feedback from the owner.
Once the Image processing is done and if it identifies as a human being the door automatically closes and the intruder is not able to go out. This proposed system is intelligent and it eliminates the need for continuous surveillance. Using sensors, the status of the place is continuously checked.
IoT smart security system mainly consists of various devices like ultrasonic sensors, with a microcontroller unit, GSM (Sim900), smart mobile phone. Ultrasonic sensors must be deployed at the places where intruders may be expected to arrive. The system is designed and developed that will continuously monitor and inform the authorized person in case of intrusion is detected. An alarm is also intimated about the presence of intruders. This IoT unit sends the message to the authorized person with the help of the GSM (Sim900) module when it detects the presence of any intruder so that person can take some action and avoid the possible theft that could happen.
The system provides the remote alert rising in case the intruder is detected so that the owner and other important people can be informed about the unwanted happenings which may occur at vaults of the temple, banks, data centres, and other treasured places. This is a low budget and easily operated intrusion detection system, so that anybody whether rich or poor, young or old can make use of this intrusion detection system (Chandrappa et al., 2018).
The GSM module is responsible for sending information from the microcontroller to the mobile station and for sending the instruction from the mobile station to the microcontroller.
Real-time implementation is achieved by using a GSM (Global System for Mobile Communication) modem for SMS (Short Message Service) notification supplemented by e-mail notification for recording data off-site to FTP (File Transfer Protocol) storage.
The GSM modem uses specific programming language, or a set of commands called AT Commands, from the HAYES AT command created by Dennis Hayes. Few of the AT commands and their function used are shown in Table 1.

Table 1. Examples of AT Commands for SMS
The design and implementation of a real-time alert system using GSM technology and motion detection are presented here. The architecture of the system is to provide the platform for flexibility and room for user customizations.
This proposed system has managed to avoid implementing expensive surveillance products for means of input and alert systems. It has managed to detect motion and capture images send out SMS via GSM modem as an alert emulating real-time and as well as e-mail notification attached to the image file (May, 2012).
The purpose is to define a safekeeping alert device spending little handling power by the Internet of things which help out to observer plus alerts when gestures or motion are there, then send images to a cloud server.
The web camera will record an image when the intruder is entering a room, in this case, the web camera will detect and capture the motion. It alerts the owner which shows that the room has been entered by the intruder. The notification is sent as an email, short message service (SMS).
The email could be completed with the attachment and text including warning of burglars who are captured in the video. An ideal image is captured as kept as a reference image. The system continuously captures images compared with those with an ideal image. If there is any variation, then the motion is detected (Patil et al., 2017).
The embedded system used is Raspberry Pi which is operated by an Open CV. The locker room is continuously monitored through a webcam, which starts recording when it senses a change in motion. This system aims to reduce the unwanted storage hence it records when there is motion detected in the image.
Raspberry Pi will be fixed at the surveillance area which controls the video camera. Once the module is started, the program will start capturing the video. The motion detection process will be initiated, once it gets three continuous frames. If it detects any motion it will at once send the notification mail to the authorized person and start video recording until it reads the motion in the captured video frame and stores it in an internal SD card of Raspberry Pi (Murugan et al., 2017).
Whenever the motion detectors detect a motion or a person steps on to the mat, the GSM module and Halogen lamp are activated, and the GSM module sends the SMS and calls to pre-stored phone numbers. The floor mat is designed by connecting push buttons in the form of a matrix so that when any button is pressed, we get the input to the microcontroller. This type of intruder detecting floor mat appears as a normal commercial floor mat available in the market.
At the receiver end, the owner of the shop gets the alert message to his mobile phone through SMS, and another SMS to a nearby police station is also sent. Whenever the owner presses the remote key, a part of the mat will get deactivated and he can easily enter the shop through the deactivated mat portion.
This type of intruder detecting floor mat appears as a normal commercial floor mat available in the market. The design and implementation of an electronic mat (E-MAT) based security system for jewellry shops, can be tailored to many other applications like a bank, Hospitals, etc., will result in increasing the secure way to protect thefts that happen especially during night times (Fathima et al., 2017).
Raspberry Pi-based security door lock system where cameras, keypad are being utilized to provide an alarming system that can notify the owner, as well as, recognizing guests by giving them a user-id. In this way, the authorized individuals are only the ones who will get permission to access the doors.
The keypad is the input module when the guest inserts the code at the door. It then sends a signal to the control module Raspberry Pi 3 which then checks the guest id by the database. The control module then sends the guest-id to the server for verification. The server then searches for guest-id and if the id exists in the database, then the server sends a signal back to the control module as a response and at the same time activates the camera and takes snaps of the user at the door and sends it through Email. Simultaneously the server notifies the owner that a guest has appeared at the door through the message "Access door request" (Hussein & Al Mansoori, 2017)
The RFID tag that attaches to an object is integrated with a motion sensor. The interrupt function is utilized to the tag to automatically detect the motion of an object.
The tag is attached to the monitored object. The identity code in the form of a unique identification number is stored in the RFID tag and contains all information about the monitored object. The motion sensor is integrated into the tag. To enable the tag to instantly detect the tamper event, the motion sensor is connected to an interrupt pin of the microcontroller.
Any changes to the signal pattern will immediately trigger the microcontroller to analyze the input signal. The proposed RFID-based anti-theft system is capable of detecting movement of the asset attached to the RFID tag. The design of the motion-sensitive RFID tag with interrupt function is capable of sending the motion alert signal to the reader in real-time (Hamid et al., 2012).
When motion is detected, the system automatically stores images and executes the appropriate alarm according to the user's settings. Mobile phones can decode them and play the surveillance video. The moving target detection method is based on the continuous five differential frames improving the existing standards - based on three different frames. After detecting the abnormal condition, the surveillance system sends the specified content and images to the default phone number by using the GPRS control module.
The H.264 coding is based on the macroblock level, so the moving target can be set to establish an external bounding rectangular model. An external bounding rectangle contains sults of motion detection for all pixels of a region by the smallest rectangle. The pixels outside the external bounding rectangle can be considered as background. Analysis of motion detection is an important step. The system decides what to do (alarm or storing the image) in the next step according to the detection results. It is a key step to realize intelligent surveillance (Ge et al., 2011).
A video surveillance system consists of three phases: moving object recognition, tracking, and decision making. The Haar classifier is trained using hundreds of sample views of various human beings, called positive samples, as well as arbitrary images without human presence, called negative samples.
After the training, it can be applied to a region of interest in each of the extracted frames. The output for this process will be a "1" if the region is likely to contain a human being, and "0" otherwise. This paper focuses on the detection of human beings in a scene and tracking those people as long as they stay in the scene by identifying individual persons. Detection and tracking of human beings can be done from video footage which can be pre-recorded or live (Visakha & Prakash, 2018).
The proposed work is to have two controls like, one is to switch off lights during no vehicle moments in streets and automatically switch it on when vehicles arrive, and the other modes are to give less intensity light for pedestrians and to switch on bright mode during vehicle moments at sides on the roads. IR sensor is used for interruption detection and sends logic signals to the microcontroller for glowing the LEDs ahead of the vehicle.
When the movement of a vehicle is detected towards the street, this turns ON a block of street lamps in front of the vehicle. As the vehicle moves forward by, the trailing lamps turn OFF on its own. So, each of the road lights stays in OFF condition when there are no vehicles on the street. There is another method of operation where instead of turning OFF the lights totally, they stay ON with ten percent of the extreme intensity of the light. As the vehicle approaches, the block of road lamps changes to a hundred percent intensity and as the vehicle moves forward by, the trailing lights return to ten percent power once more (Yashaswini et al., 2018).
The IR sensor is placed in all possible entrance areas which act as a motion detector. When the IR sensor detects motion, with the help of a two-channel relay all the lights are turned on to achieve a clear image of the site. The captured image is processed to make sure the intruder is a human or not. Once it is identified as a human using the Sensor Flow Lite algorithm, the image captured is sent to the owner through email with the help of an online tool called Twilio which will also serve as evidence and an SMS alert will also be sent. Simultaneously with the help of DC motor, the security gate which is installed will simultaneously get closed so that the culprit is captive inside and cannot escape from the site and the alarm rings to notify the neighbours so that they can help in taking immediate actions and need not wait till the owner comes.
The block diagram of the Anti-theft security system is shown in Figure 1. The block diagram consists of Raspberry Pi 3 B, Camera, L293 Motor driver circuit, Two-channel relay, buzzer, DC motor, power supply, IR sensor and lights.
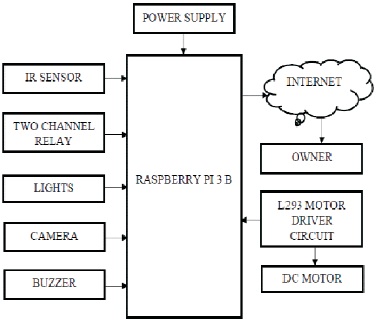
Figure 1. Block Diagram of the Implemented System
Figure 2 shows the system configuration after interfacing all the hardware components.

Figure 2. Design and Implementation of the Proposed System
In this project, we use the Raspberry Pi 3 B module which acts as an operating system to which all the components are interfaced. The camera is programmed in such a way that it starts recording only when motion is detected. It consists of an IR sensor that acts as motion detection, two channel relay as a switch which turns on all the lights to capture a clear image during night time. The captured image is processed to find whether the intruder was a human or not. If the intruder is found to be a human, then the captured image is sent to the owner through email with the help of Twilio. Simultaneously, the security gate gets closed with the help of L293 motor driver and DC motor closes the gate and the buzzer acts as an alarm which helps in notifying the neighbours about the theft happening, so that they can help in taking action against the culprit.
The flow chart of the working of the implemented system is as shown in Figure 3.
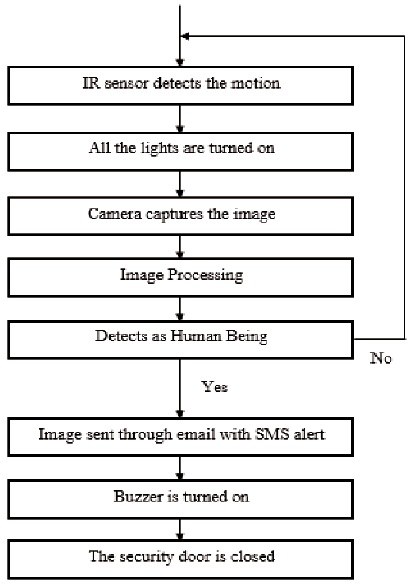
Figure 3. Flow Chart of the Device
IR sensor is used to detect motion in this proposed system. Figure 4 shows the system before motion is detected and The interfacing between the Raspberry Pi 3 B and the IR sensor is as shown below in Figure 4.
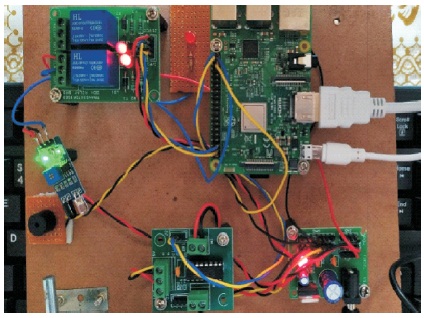
Figure 4. IR Sensor and Raspberry Pi Interface
When there is no motion detected the LED is in the off state. Figure 5 shows that when motion is detected using the IR sensor the LED is turned on. It shows that the led serving as lights are turned on to get a clear image once the motion is detected. Later, the camera captures live images, and the image is processed using a Tensor flow lite algorithm and verifies whether it is human or not. If it is human, the captured image is sent to the owner via email and the security gate closes so that the intruder is captive in the site itself.
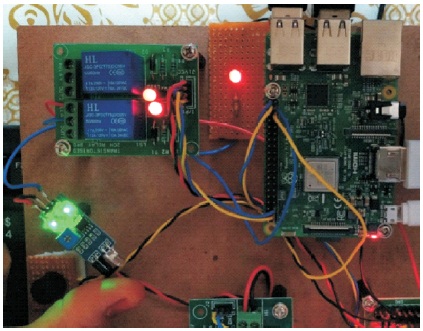
Figure 5. Object Detected using IR Sensor
Figure 6 shows the message displayed in the terminal window, i.e., the motion is detected and the security gate is open.
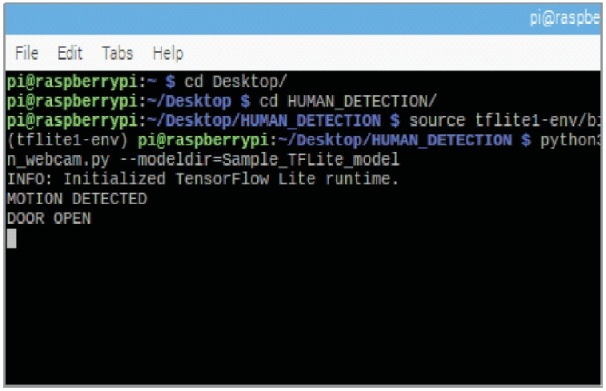
Figure 6. Terminal Window 1
Figure 7 shows that the security gate is open when the motion is detected. Figure 8 shows the message displayed in the terminal window when the object detected is human and the security door is closed.
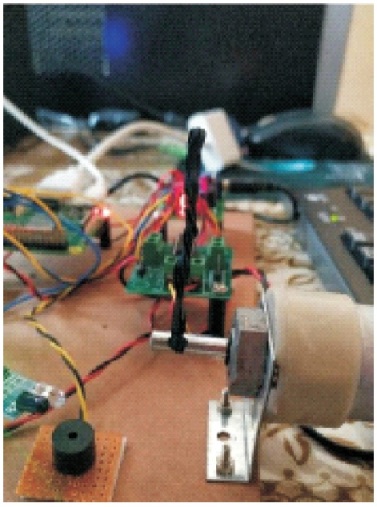
Figure 7. Measurement of Pulse Rate
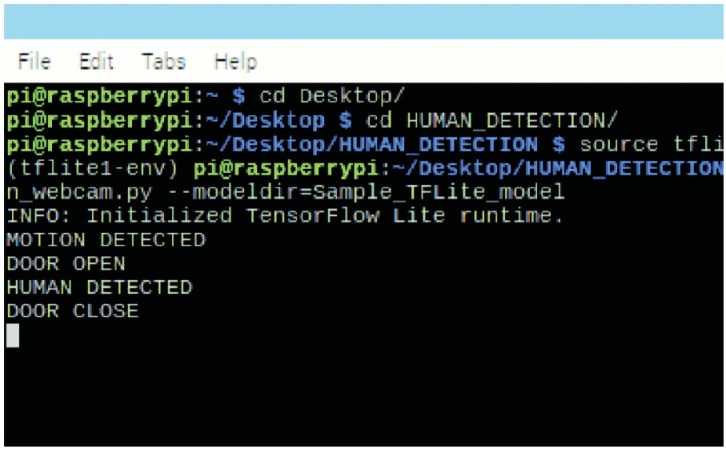
Figure 8. Message Displayed in Window
Figure 9 shows that the security door is closed when the detected object is a human. Figure 10 shows the email received to the owner when the intruder is detected. The neighbours are alerted about the theft happening using the buzzer.
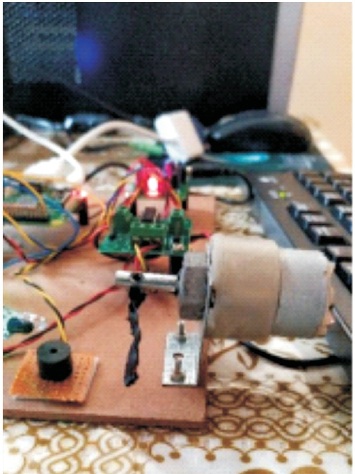
Figure 9. Security Door Close
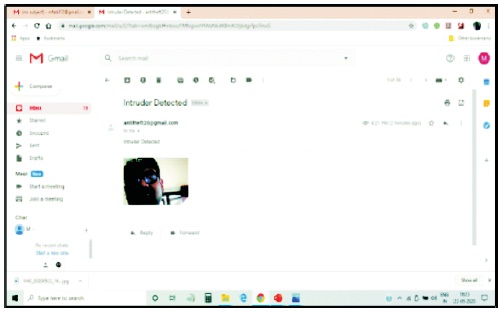
Figure 10. Email Notification