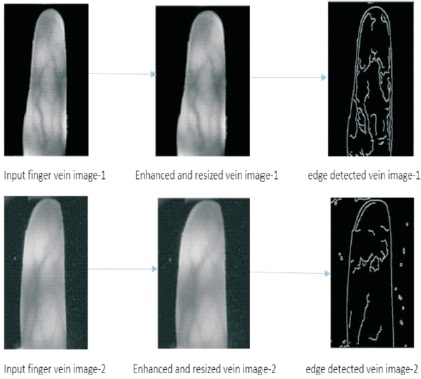
Figure 1. Edge Detection of Two Input Finger Veins
In India, electoral voting is done using electronically operated voting machines. Currently, the identity of the voter is validated by non-biometric process. Implementation of technology through computerized process has scope for using biometrics to validate voter's identity. Physiological or behavioral features of human are used as a biometric for personal identification. There is a large dataset of biometric patterns available, and many software systems have been developed and implemented, for recognition of face, hand shape, fingerprint, palm, iris, etc. The system proposed in this paper is implemented using embedded technology to utilize finger-vein image recognition. The system also has a MATLAB section, which will capture the vein in finger of the voter and their sample is registered to the controller. In order to cast a vote, the captured finger vein image must match the image already stored in the database along with the voter's RFID card. It the image identification failed to match with the authorized person, the system will send alert to authorities.
The voting mechanism follows creation of unique voters ID. People cast their vote to the candidate of their choice. The authorities conducting the election monitors the process to avoid any illegal activities. Political parties involve in illegal activities at the pooling booth by using fake IDs to gain power. To avoid these illegal activities, the new voting system is developed.
The electronic polling machine is being used in many countries but the current system does not eliminate illegal voting, where possibility of a non authenticated voter casting a vote. The system also fails to provide high security to the users as well as to the nation which can cause vulnerability to the system (Sapkale & Rajbhoj, 2016). Therefore, they have been accepted to use only in few developed countries. Hence we require a system that overcomes this security issue which is widely present.
The proposed model is a system based on the recognition of images of finger veins, which will provide a better electoral system and provide secure voting than the existing method. In an election, the voter voted with a finger, but with recent researches, systems are proposed that can extract an image of a voter's finger vein and allow the voter to cast the vote (Liu et al, 2017; Wolchok et al, 2012). Using this kind of highly secured new methodology a voter can record their vote. This highly secured methodology improves authenticity and security. In the proposed system, an authenticated voter can vote only once and therefore, this method will prevent any fraudulent activity.
When a person comes to vote, finger prints of the caster is taken as the main authentication resource. Since the finger pattern of each human being is varied, the caster can be easily authenticated. The system authenticates the voter to vote through his/her fingerprint. As soon as they cast their vote, their voter ID and other details will be locked and further access into the voting system will be denied. It is done to preserve the security (Wu et al., 2011). When every voter cast their vote, the result will be updated automatically and the results can also be published on the same day of the election. The proposed system will also support online voting. Compared to palm vein authentication, vein authenticity of finger is less time consuming and gives more accuracy too (Jain, & Kumar, 2019).
Initially the finger vein of the person is scanned and then it is compared with the image stored inside the administrator database and then displays whether the concerned person is authenticated or not. Using near-infrared spectrum (NIR) authentication method vein images are observed, which is the safest authentication technology (Waluś et al., 2017). Blood vessels absorb the infrared light and veins are visible as dark areas in the finger. From the open source dataset we have selected some images for testing and for processing.
Various stages of finger vein authentication includes,
Image acquisition is the process of capturing the image from the database where the images are already stored. Preprocessing stage includes the converting of the image to grayscale, resizing the image, normalization and image enhancement. Canny edge detection algorithm is used for edge detection mechanisms, where threshold values are being set for pressed vein image (Bhattacharyya et al., 2009). When the threshold value is above 0.07, part of the image appears as white and when below 0.07, the vein edges appears in black colour. Then, the image is compared pixel by pixel with the image stored in the database and authenticated.
Figure 1 shows the edge detection of two input finger veins images where the input image is first enhanced and then resized to perform edge detection. The step-down transformer is used to supply power to the microcontroller by stepping down the voltage from (0-230 V) to (0-6 V) level. PIC microcontroller is used because of its convenience in coding or programming (Bhuvanapriya et al., 2017; Musiał-Karg, 2014). The GPS module provides the location to the microcontroller where malpractice takes place by voting for the second time and the microcontroller alerts with the help of a buzzer. The Universal Asynchronous Receiver and Transmitter (UART) is the key controller component for the serial communications subsystem of a computer. UART is the easiest form of communication between microcontroller and Computer system (Krishnamurthy & Gayathri, 2017). The Matlab image processing section processed the image which involves gray scale conversion, segmentation, statistical parameter extraction that are shown in the figure.

Figure 1. Edge Detection of Two Input Finger Veins
Figure 2 depicts the flow diagram and Figure 3 shows the blocks used. The step-down transformer along with a bridge rectifier and voltage regulator is made use for power supply that steps down the supply voltage from (0- 230 V) to (0-6 V). PIC16F877A is the microcontroller used for the proposed work. It has a total number of 40 pins and there are 33 pins for input and output. The PIC microcontroller is used because it can write-erase as many times as possible because of the FLASH memory technology (Krishnamurthy & Gayathri, 2017). It is of low cost and is flexible to use. UART has a special function register that takes data in bytes and transmits the individual bits in a sequential method and at the destination; then UART re-assembles the bits into bytes. Data transmission serially via a single wire or other medium is cost effective than parallel transmission through multiple wires. The Global Positioning System (GPS) imparts reliable positioning and timing services to the users on a continuous basis anywhere on or near the earth. The GPS module is used to monitor and alert about the malpractice in the proposed work. GSM is a transmission and reception modem that is primarily used in mobile communication. Its module consists of a mobile station, base station subsystem and a network subsystem. The mobile station is controlled by a SIM card operating over the network. The Base Station Subsystem acts as an intermediary between the mobile station and the network subsystem. The Network Subsystem provides the basic network connection to the mobile stations.
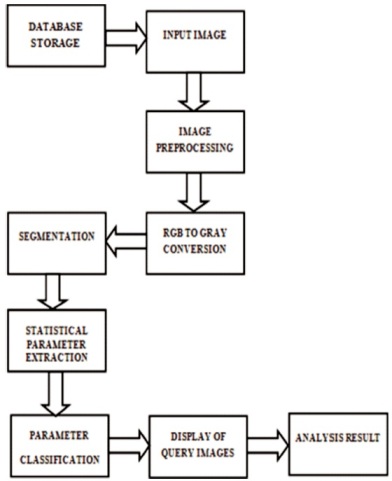
Figure 2. Work Flow Diagram
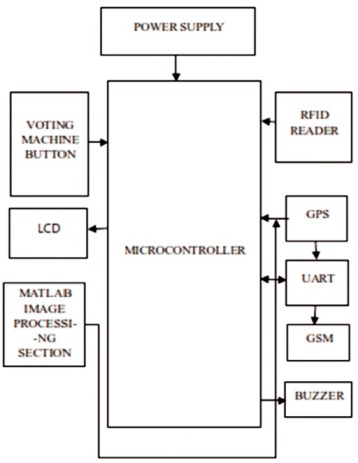
Figure 3. Block Diagram of Proposed Model
A GSM modem as shown in Figure 4 is duly interfaced to microcontroller through the level shifter IC MAX232. The SIM card mounted on the GSM modem, on receiving command via SMS from any cell phone sends that data to the microcontroller through serial communication. While the program is being executed, the GSM modem receives a command 'STOP' to develop an output at the microcontroller. The command so sent by the user is based on an intimation received by him/her through the GSM modem 'ALERT' a programmed message that is displayed only if the input is driven low. The complete operation is displayed over a 16×2 LCD display (Bhattacharyya et al., 2009).

Figure 4. GSM Modem
The system is programmed using Embedded C and for the analysis image is processed using Matlab. Embedded C supports multiple address spaces and can directly access the individual processor instructions that are designed for optimal memory access. Named address spaces use a simple approach to group the memory locations into functional groups to support Multiple Access Control buffers and a latest version of MP 8.60 is recommended to code the program using Embedded C language.
A voting machine that scans and tracks the location of voter during voting is developed and a computer system is connected to the machine using RS 232 cables (Krishnamurthy & Gayathri, 2017).
If both finger vein image matches with the real time scanned image, the user will undergo the scanning process of their voter id. If it is matched, then the voter will be allowed to cast their vote. The user trying for second time will not be allowed as their finger vein is already scanned and the login is being denied for that user. The casted votes are incremented in the database automatically and results can be declared on the election day itself with good accuracy. Figure 5 shows the proposed system consisting of the PIC microcontroller and RFID reader.
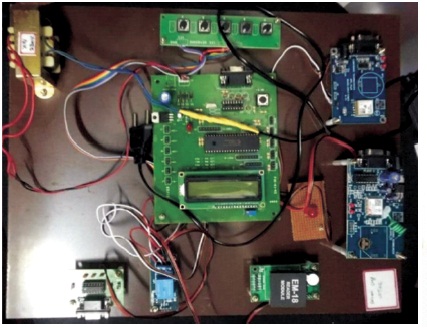
Figure 5. The Proposed System Consisting of the PIC Microcontroller, LCD, GSM Modem and Power Supply, Relay and RFID Reader
Canny algorithm is used to set the threshold value of 0.07 above which image appears in white color and remaining appears in black color. In order to get exact output, background subtraction is carried out. Figure 6 shows the authentication notification of the proposed solution. Finger vein image of the authorized person along with RFID card is given as input to the PIC16F877A microcontroller which is used in casting polls. The merits of using the proposed system for voting is reduction in manual work since digital voting takes place. It is a transparent voting system and provides secure voting by matching the finger veins.
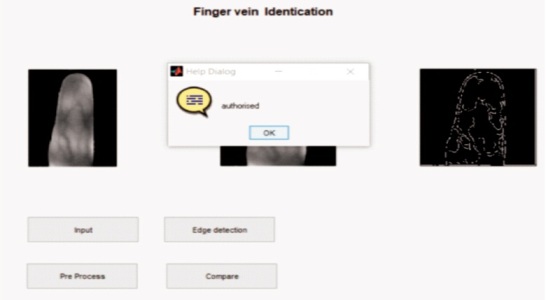
Figure 6. Authorized Finger-Vein of the Person with a Notification
Therefore, it provides a proof that the captured finger vein is from authentic person matching the RFID thus providing security. The violation that takes place during election can be avoided and make our country a better nation.
The finger vein recognition methodology is highly reliable and secured one for personal identification. It is difficult to steal because the vein is buried within and is generally invisible to naked eyes. Non-invasive and contactless capture of finger veins will be convenient for users, and more acceptable as the finger vein pattern can be derived from the living person. Therefore, it provides a proof that the captured finger-vein is from live person thus providing security. In future the same concept could be developed using block chain methodology to further improve the security and authentication in Electoral system and can also implement the authentication of other fingers in case of wound or cut in index finger.