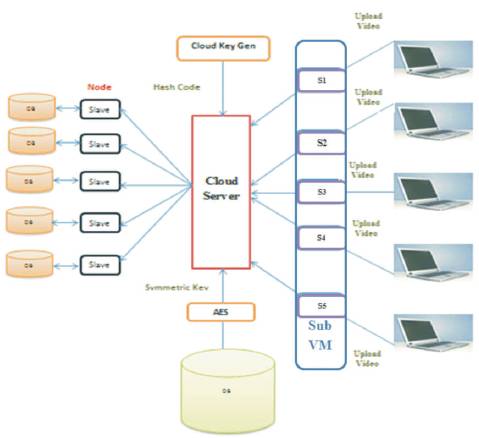
Figure 1. Cloud Video Server Architecture with Sub Virtual Machine (VM)
In today's fast growing world, everyone needs a secure storage for their important information like personal videos. So the service provider needs an excellent cloud video server with high security. But hackers easily hack any kind of security mechanism. In this paper , the novel tolerant security mechanism is proposed. A server stores all new information in its storage. The Cloud Video Server is acting as a controller of all the slaves. This system has two protocols named Promise Protocol and Review Protocol for monitoring slaves activity. This scheme uses two standard algorithms namely SHA3 (Secure Hash Algorithm -3 ) and Advanced Encryption Standard (AES) for security test. The performance is verified with the help of the metrics like security level, time complexity ,and Quality of Storage. The performance of this system is superior than the other schemes.
With the tremendous growth of Multimedia services and video information on internet, Video security is getting more important than ever. Cloud Based Applications has become essential in everyday life. People use the Cloud to work, to exchange video, to make efficient learning, in telemedicine and defence forces, etc. This growth of the Cloud use has unfortunately been accompanied by a growth of malicious activity in the Cloud. More and more vulnerabilities are discovered, and nearly every day, new security advisories are published[2][25]
Potential attackers are very numerous, even if they represent only a very small proportion among the hundreds of millions of Cloud users and clients. The problem is thus particularly tricky: on one hand, the development of the Cloud allows complex and sophisticated services to be offered, and on the other hand, these services offer to the attacker many new weaknesses and vulnerabilities to exploit [9].
The complexity of current computer systems has been causing an immense number of vulnerabilities. The number of cyber-attacks has been growing making computer security, as a whole, an important research challenge.
Database (IT) has been proposed as a new paradigm for computer system security. The idea applies the fault tolerance paradigm and virtual mechanism in the domain of system security. Malicious faults can never be entirely prevented.
Intelligent techniques and security technique used in the said field have been discussed in detail [1]. In the application of tolerant architecture and heterogeneous environment for webservers, Agreement protocol is used to provide more security. Comprehensive analysis of security mechanism has been presented in[2].
Wen-HsingKuo (2011) has designed a polynomial-time solution. From that, it supports both unicast and multicast, and both single layer and multi-layer environments. Most importantly, it can be integrated with the multicast mechanism defined in WiMAX standards, and can also be applied to any kind of wireless networks which support adaptive modulation and coding schemes [3].
The utility value can be measured using the video quality perceived by the user, which can be described by metrics such as the Peak Signal-to-Noise Ratio (PSNR) [4]. and the Mean Opinion Score (MOS) [5].
Wu and Boyce[6] investigated streaming of pre compressed video. After offline compression with several redundant representations of variable quality, the delivery policy (which redundant slices to transmit) is optimized during transmission. Baccichet et al. [7] proposed a redundant encoding scheme for live video streaming The primary picture is coded independently[10,11,12]. from the redundant slices, which may cover the entire picture or just a Region Of Interest (ROI). Redundant MBs (Macroblocks) use the same coding parameters as the primary MBs, but a larger QP (Quantization Parameter) is selected on a GOP-by-GOP (where GOP-Group of Pictures) basis via a concealment distortion model. In the MDC (Multiple Description Coding) scheme in [8], each frame is split into two slice groups [13]. Two balanced descriptions are generated by combining the primary slices from one group with the redundant slices from the other [14].
A dependable system[2] is defined as one that is able to deliver a service that can justifiably be trusted. Attributes of dependability include availability (readiness for correct service), reliability (continuity of correct service), confidentiality (prevention of unauthorized disclosure of information), and integrity (the absence of improper system state alterations).
Security is the concurrent existence of
Based on the dependable system architecture, the proposed Cloud Video Server is designed. The Cloud Video Server can be illustrated as follows:
Step 1 :User can upload a video to Cloud Video Server.
Step 2 :Video Server uses a SHA-3 to generate the Hash and Replicate the Video into Cloud Video Data Bases. Step 3 :The SHA-3 Hash is encrypted using Advanced Encryption Standard and the Hash is stored to Cloud Data base.
Step 4 :If an user needs a video , it searches from video data base and generates its hash using SHA-3.
Step 5 :Take a Encrypted Hash from Cloud DB and Decrypt using AES, compare these two values.
Step 6 :If fails, go to step 4, else provide the correct service.
Figure 1 illustates the overall system architecture. In Figure 1, the User can upload a video to Cloud Video Server. The Video Server uses a Secure Hash Algorithm to generate the Hash and Replicate the Video into Cloud Video Data Bases ie Node Slaves.The Hash Code is encrypted using Advanced Encryption Standard and the Hash is stored to Cloud Data base. In AES, it uses Symmetric Key, ie same key is used for both encryption and decryption process. Cloud key generator generates the Key for the Cloud Video Server. If an user needs a video , it searches from video data base and generates its hash code. An Encrypted Hash code is taken from Cloud Database and Decrypted using AES. These two values are compared. If Fails, the process is repeated again, else the correct service is provided.

Figure 1. Cloud Video Server Architecture with Sub Virtual Machine (VM)
Figure 2, the overall activity diagram, shows the functions of Cloud Video Server. First it performs to monitor all the slave nodes and video database, if failure occur, call promise protocol, analyze the failure rate and save the report. If the failure rate is greater, send alert message to indicate harm status and stop the service.
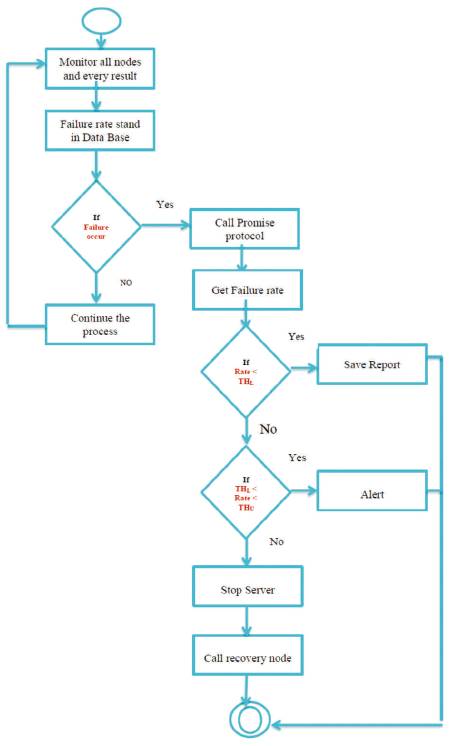
Figure 2. Activity Diagram for the Cloud Video Server Functions
Algorithm A , B , C provides the basic functionalities of the tolerant system.
SHA-3, a subset of the cryptographic primitive family Keccak is a cryptographic hash function designed by Guido Bertoni, Joan Daemen, MichaëlPeeters, and Gilles Van Assche, building upon RadioGatún [16,17]
On October 2, 2012, Keccak was selected as the winner of the NIST hash function competition. SHA-3 is not meant to replace SHA-2, as no significant attack on SHA-2 has been demonstrated. Because of the successful attacks on MD5 and SHA-0 and theoretical attacks on S-1 and SHA-2, NIST perceived a need for an alternative, dissimilar cryptographic hash, which became SHA-3 [19].
SHA-3 uses the sponge construction in which message blocks are XORed into the initial bits of the state, which is theninvertibly permuted. In the version used in SHA-3, the state consists of a 5×5 array of 64-bit words, 1600 bits total. The authors claim 12.5 cycles per byte on an Intel Core 2 CPU. However, in hardware implementations, it is notably faster than all other finalists [20,21].
Keccak's authors have proposed additional, not-yetstandardized uses for the function, including an authenticated encryption system and a "tree" hash for faster hashing on certain architectures. Keccak is also defined for smaller power-of-2 word sizes ‘w’ down to 1 bit (25 bits total state). Small state sizes can be used to test cryptanalytic attacks, and intermediate state sizes (e.g., from w=4, 100 bits, to w=32, 800 bits) could potentially provide practical, lightweight alternatives [22,23].
This is defined for any power-of-two word size, w = 2t bits. The main SHA-3 submission uses 64-bit words, ℓ= 6.
The state can be considered to be a 5×5×w array of bits. Let a[i][j][k] be bit (i×5 + j)×w + k of the input, using a little endian convention. Index arithmetic is performed ‘modulo 5’ for the first two dimensions and ‘modulo w’ for the third.
The basic block permutation function consists of 12+2ℓ iterations of five sub-rounds, each individually very simple:
Θ Compute the parity of each of the 5×w (320, when w = 64) 5-bit columns, and exclusive-or that into two nearby columns in a regular pattern. To be precise, a[i][j][k] ⊕= parity(a[i][j−1][k]) ⊕parity(a[i][j+1][k−1])
P Bitwise rotate each of the 25 words by a different triangular number 0, 1, 3, 6, 10, 15, .... To be precise, a[0][0] is not rotated, and for all 0≤t<24, a[i][j][k] = a[i][j][k−(t+1)(t+2)/2], where
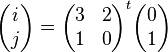
 Permute the 25 words in a fixed pattern. a[j][2i+3j] = a[i][j]
Permute the 25 words in a fixed pattern. a[j][2i+3j] = a[i][j]
Χ Bitwise combine along rows, using a = a⊕(¬b&c). To be precise, a[i][j][k] ⊕= ¬a[i][j+1][k] & a[i][j+2][k]. This is the only non-linear operation in SHA-3.
I Exclusive-or, a round constant into one word of the state. To be precise, in round n, for 0≤m≤ℓ, a[0][0][2m−1] is exclusive-ORed with bit m+7n of a degree-8 LFSR sequence. This breaks the symmetry that is preserved by the other sub-rounds[24].
Promise protocol ensures that reliable service is provided to the users by Hash code mechanism and virtual controller. It is used to provide a continual and safe service to the user. Its algorithm is as follows:
The Protocol ensures that the controller checks the web servers periodically or at a specified time based upon traffic flow to ensure that no intrusion has affected the servers .Its algorithm is as follows:
AES algorithm ensures that the hash code is encrypted in a highly secure manner. AES has a fixed block size of 128 bits and uses a key size of 128 in this paper. Its algorithm is as follows:
Cloud Video Database Manager monitors the activity of Virtual Controller and performs the following operations
The CVDBM records the information for various activities taking place in the Cloud Video Server and analyses this information to provide an activity analysis [15]. Some of the activities that are monitored are as follows:
Based upon the activity analysis, the status of alarm is decided and corresponding alarm is aroused.
Example: If the Failure rate < THL , higher level alarm is raised to intimate the administrator for necessary actions.
The Activity Analysis Process rates the sub servers into the following types.
Trust worthy - High Priority
Suspected - Medium Priority
Corrupted - Low Priority
The Primary Sub Video Server Selector selects the Primary Sub Server based on the priority and Load balance. The priority of a server is decided based upon the following formula:
Initial State of Sub Servers
ACD(X) =0 - Trust Worthy
When the first Alert occur, the system moves to the suspected states.
ACD(X) +=Awi(x) –Suspected
It remains in the suspected state, until the following condition satisfies.
ACD(X) =Awi(X) > TC- Corrupted
When the condition fails, the system moves to the corrupted state and the system is rebooted after which it moves back to trust worthy state.
ACD(X) : alert level of Cloud Database X
Awi : weight of alert I for
Figure 3 represents the Cloud video selection based on state diagram through Trust, Suspend and Corrupted states. If Failure rate is lesser, it is in Trust state and provides the service. If Failure rate increases, state changes to ‘suspend the service’ and promise and review protocol to ‘replace correct video’. If failure rate increases more, it is in corrupted state, to stop the service and restart the node.
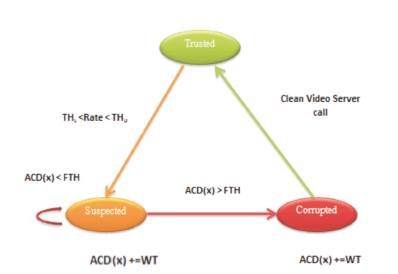
Figure 3. Cloud Video Database selection
Performance analysis for CVS was performed considering the following four factors.
The time taken to fetch the video from cloud database is described in Table 1.
Table 1 shows the time taken for loading the various videos using different cloud servers.
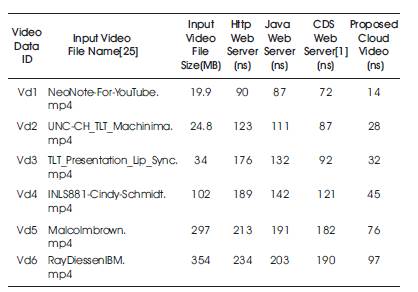
Table 1. Time Complexity Analysis
Figure 4 shows the comparative time complexity analysis for the video storage process, The time taken for process was tested for TREC (Text Retrieval Conference) Video Retrieval Test Collection standard video database. The graph shows comparison between time complexity in nano seconds and video file size in mega bytes. For that comparison, the proposed method provides very less time taken for processing data.
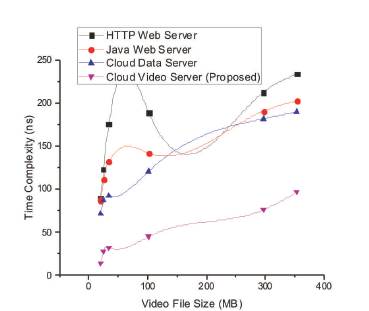
Figure 4. Time Complexity Analysis
Figure 5 shows the average time taken for loading the various videos using different cloud servers pictorially. It shows cloud video server which takes less time than other process because it is deployed in heterogeneous nodes on cloud.
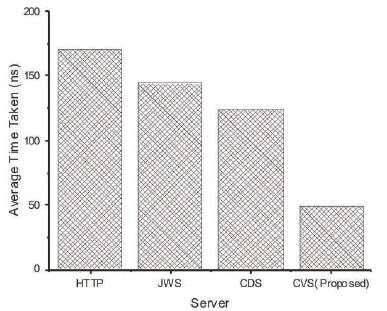
Figure 5. Average Time Complexity analysis
SHA3 Algorithm is the one of the powerful algorithm to generate hash code [18].
AES Algorithm is the one of the most secure encryption algorithm[6].
Precision and Recall are two widely used metrics for evaluating the correctness of a Cloud Video Database [26,27,28].
Precision rate and Recall rate are then defined as:
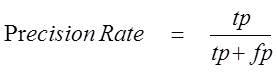
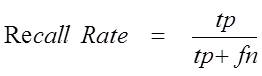
where,
fn - False negatives are considered as Normal replicated video available on the slave nodes
tp - True Positive, at the time of Video fetching, Promise Protocol tests the video and takes as good one.
fp - False Poitive, at the time of Video fetching, Promise Protocol tests the video and takes as infected one.
tn - True Negative, at the time of Review Protocol execution in periodical time, tests the video and taken as infected one[29,30].
In the Cloud Video Server for test, rail retrieving video in the Heterogeneous Client identifies 24 good videos among 30 videos and some infected videos. If 23 of the identifications are correct, but 1 is actually infected video, the program's precision is 23/24 while its recall is 24/30. Precision can be seen as a measure of exactness or quality, whereas recall is a measure of completeness or quantity
Figure 6 expresses the trial run data of Cloud video server and Precision Rate was 0.95 and Recall rate was 0.76. It shows Cloud Video server effectively tests the video and provides the service.
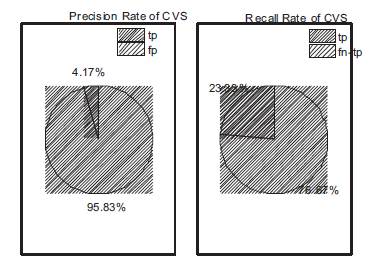
Figure 6. Precision and Recall Rate of CVS for a Trail Run
Persistent service Availability lies between 0 to 1. It is been measured using Rank Correlation by the relation between web servers.
Table 2 shows the Persistent service Availability of various servers.
Figure 7 represents the persistence availability based on average speed in which, Cloud Video server outperforms higher speed compared with others . Based on average delay, Proposed scheme gives less delay compared with existing schemes.
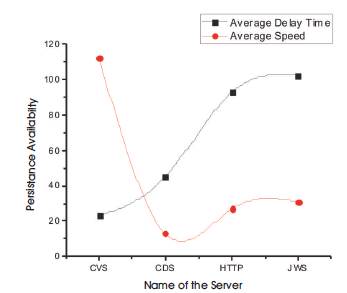
Figure 7. Persistence Availability of Different Server
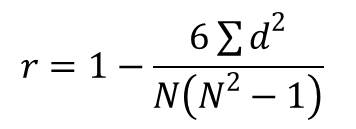
where,
r-Rank Correlation
d-differences in Rank
N-Number of Servers
Using the formula (4), Rank correlation is calculated. The Value of r=1.
In this paper, the novel tolerant security mechanism is proposed. A Server stores all new information in its storage.The Cloud Video Server is acting as a controller of all the slaves. This scheme uses two standard algorithms namely SHA3 (Secure Hash Algorithm-3) and Advanced Encryption Standard (AES) for security test. The performance is verified with the help of the metrics like security level, time complexity, and Quality of Storage. The performance of this system is superior to the other schemes. The CVS tool provides a security through Hashing and Encryption Mechanism. The proposed mechanism is more helpful for storing multimedia datas in the Cloud in a secure way. The scheme takes into consideration all the issues related to cloud storage and has proved that it works well. It provides a secure and reliable cloud video storage.